1 Introduction
HE volume of data in-home monitoring systems within the Internet of Things (IoT) ecosystem has grown ex- ponentially, becoming a target for malicious activities, such as eavesdropping and data theft, intensifying the urgency to safeguard privacy. This scenario presents a dual set of challenges. Firstly, there are threats from attackers, includ-ing distributed denial of service (DDoS) attacks, advanced persistent threats (APT), SQL injection attacks, interception of data transmission, and decryption efforts to access private information, as discussed by Kolias et al. [2]. Secondly but equally critical are the challenges associated with cloud com- puting, where data, often stored or processed in the cloud, face risks such as unauthorized access, data mining without consent, and potential breaches, necessitating robust cloud- based privacy and security measures [15]. This intensifies the need for comprehensive solutions to protect the vast data flowing through IoT devices and store or process it in the cloud.
HaddadPajouh et al. explored the vulnerabilities of IoT systems to DDoS attacks, highlighting the inadequacies in data upload protocols and cryptographic measures for traffic en- cryption. They noted that when adapted for encrypted uploads, plaintext transmission protocols exhibit significant weaknesses in multi-user or multi-device configurations [22]. Kolias et al. investigated cryptographic protocols, finding that conventional methods are insufficient in scenarios with multiple devices linked to a single account, complicating key negotiation pro- cesses and increasing decryption vulnerabilities [23]. Juvekar, Vaikuntanathan, and Chandrakasan addressed the complexity of deploying secure computation frameworks like Gazelle and Delphi in neural network inference within IoT systems, suggesting that while these frameworks offer advanced secu- rity, they are challenging to implement in practical scenarios [13, 14]. HaddadPajouh et al. analyzed homomorphic encryp- tion techniques in IoT, indicating that despite their potential for enhancing privacy, they remain complex and difficult to integrate into existing systems [1, 2]. Chen and Zhu cri- tiqued the foundational assumptions of IoT security solutions, pointing out the lack of empirical substantiation and practical deployment, which extends to cloud security and data mining [10-12]. Coppola, Varde, and Shang developed a Cloud Security Posture Management (CSPM) tool, and Mahmood introduced the Anti-Data-Mining (ADM) framework, aiming to improve cloud security and privacy protection through artificial intelligence and obfuscation strategies, respectively. However, these solutions have not yet proven effective in real- world applications and against advanced adversaries [15, 16]. Designing secure systems in cloud computing is complex.
For example, building an Economic Security Early Warning System using cloud and data mining [17] or studying how shared cloud infrastructures can be vulnerable to attacks [18] shows the technical challenges and need for deep expertise in different fields. Also, looking at ways to improve cloud security through cryptography [19] and setting up detailed access controls in cloud-fog environments [20] highlight how advanced security measures and operational efficiency must work together. Additionally, using advanced machine learning, like Modified Support Vector Machines, to detect diseases early in cloud-based systems [21] shows the high level of skill in machine learning, security, and cloud computing that is necessary. In summary, creating effective and secure cloud systems requires a combination of advanced technology and expert knowledge.
Previous research in the field suggests that integrating intricate security mechanisms [1, 2], through critical eval- uations of theoretical frameworks [10-12], to innovations in cloud security and data mining [17, 18] highlights the necessity for a harmonized approach that integrates techni- cal profundity with actionable solutions. Such a strategy is crucial for propelling the dialogue on IoT security forward and for developing robust, scalable, and user-friendly security measures for home monitoring systems equipped to navigate the continually shifting terrain of cyber threats. Addressing the highlighted deficits within the domain of IoT securityresearch requires understanding the multifaceted challenges, especially those related to implementing secure computational frameworks [13, 14] and empirically validating the prevailing cryptographic protocols [15, 16].
To address the issues discussed, this paper proposes the following solutions: 1. Establishing a comprehensive legisla- tive framework for data governance, 2. Ensuring cryptographic agility among service providers, 3. Promoting cyber hygiene and digital literacy among consumers.
This proposition’s core is a detailed analysis of the IoT security ecosystem, wherein the framework identifies and targets pivotal junctures for strategic intervention. These inter- ventions are designed not merely as stopgap measures but as foundational pillars to fortify data integrity and confidentiality across the IoT spectrum. This proactive approach underscores the necessity for a dynamic and adaptive security posture that can evolve with emerging threats and technological advance- ments. Central to the proposed framework is a triadic engage- ment model that harmonizes the efforts of legislative bodies, service provision entities, and the end-user community. At the legislative forefront, the framework mandates establishing comprehensive data governance policies, which are envisioned to compel service providers to adopt and integrate cutting- edge end-to-end encryption methodologies underpinned by a systematic regimen of periodic compliance verifications and stringent repercussions for non-compliance. This legislative initiative is predicated on a forward-thinking paradigm that prioritizes the safeguarding of data through state-of-the-art cryptographic innovations such as Elliptic Curve Cryptography
(ECC) and Quantum Key Distribution (QKD), thus ensuring robust protection against unauthorized intrusions and data breaches.
The framework advocates a paradigm of cryptographic agility for service providers, governed by regularly renewing the cryptographic keys and adopting sophisticated multi-factor authentication systems. These measures aim to render data pathways more opaque and reduce the likelihood of security breaches. Complementing this technical guidance is a policy directive that champions the widespread implementation of Transparent Data Encryption (TDE) protocols. This directive aims to institutionalize data obfuscation as a default practice, elevating data privacy standards and reinforcing the overall security infrastructure.
Addressing the needs of the consumer demographic, the framework strongly emphasizes the cultivation of cyber hy- giene practices and promotes the integration of user-friendly security interfaces and the widespread dissemination of digital literacy programs. These initiatives are designed to empower consumers, enhancing their ability to effectively navigate the complexities of IoT device security and proactively mitigate potential vulnerabilities.
The rest of this paper is organized as follows: In Section 2, we discuss the work related to the paper. The technical solutions and policy solution for enhanced IoT security are described in detail in Section 3 and Section 4. The detailed implementation framework is in Section 5. Finally, the article concludes in Section 6.
2 Analysis of the current IoT security framework
This section focuses on the industry’s prevalent data upload and cloud storage frameworks within IoT. These frameworks ensure data integrity and privacy in IoT systems, involving several protocols and standards for secure data transmission and storage. Understanding the existing frameworks is critical for identifying potential security gaps and areas for improve- ment in IoT data management practices. This analysis will be the basis for exploring enhancements to bolster IoT security.
Following this analysis, the paper will delve into the security challenges faced in multi-user upload scenarios within IoT, highlighting the vulnerabilities and proposing robust protocols and encryption methods to enhance security. We will then explore the complex security measures necessary for safe- guarding data within the IoT ecosystem, especially focusing on home monitoring systems. The discussion will extend to policy formulation within the existing IoT systems framework, examining the challenges and proposing integrated solutions. This will set the stage for a detailed presentation of technical and policy solutions designed to fortify IoT security, culminat- ing in a comprehensive framework encompassing regulatory practices, corporate compliance, and user engagement and empowerment. The paper will conclude with case studies and applications, illustrating the practical implications and challenges of implementing the proposed security framework.
2.1 Security analysis in multi-user upload scenarios
In the context of multi-user upload scenarios within IoT, several widely adopted protocols have been identified as having significant vulnerabilities. For instance, using HTTP for data transmission, which lacks encryption, can lead to man-in- the-middle attacks [24]. Additionally, implementing outdated cryptographic algorithms such as DES (Data Encryption Stan- dard) can result in weak encryption easily broken by modern computational power [25]. These significant vulnerabilities can lead to unauthorized access to sensitive data, service disruption, and potential financial losses for users and service providers.
The fundamental issue arises from a prevalent oversight in the IoT security design—prioritizing functionality over security. This oversight occurs because the rapid development and deployment of IoT devices often outpace the integration of robust security measures. For instance, the convenience of HTTP for data transmission has overshadowed the critical need for encryption, exposing data to potential interception. Adopting HTTPS with TLS provides a stronger security model, but what are its limitations in the IoT context? While HTTPS enhances data privacy and integrity, it may introduce significant overhead for devices with limited processing capabilities, leading to neglected updates and inconsistent security practices across the IoT spectrum. This scenario highlights a critical gap: the need for a security framework that is robust, adaptable, and scalable to the diverse and dynamic nature of IoT environments.
Researchers have proposed various solutions to address these challenges, such as using key negotiation centers (KNC)to streamline the key management process [31]. However, implementing these solutions in the IoT ecosystem requires a deep dive into the complexities of managing cryptographic keys across a heterogeneous array of devices with varying computational capabilities and security needs. By centralizing the key negotiation process, KNCs can potentially simplify the management of encryption keys, ensuring they are consistently updated and securely distributed to authorized devices only. While beneficial in reducing the operational complexities associated with key management across disparate devices, this centralized approach also necessitates careful consideration of the system’s scalability, resilience to attacks, and the potential risk of creating single points of failure. To effectively integrate KNCs into the IoT infrastructure, a detailed examination of the network’s characteristics, including device diversity, connectivity stability, and the dynamic nature of IoT deployments, is essential. Such an analysis must also contemplate the balance between the centralization benefits of KNCs and the need for distributed security mechanisms to mitigate the risk of targeted cyber-attacks and ensure continuous availability and integrity of the key management service. Therefore, while KNCs present a viable strategy for improving key management in IoT networks, their successful deployment hinges on a comprehensive understanding of the ecosystem’s specific requirements and constraints, ensuring that the solution is not only technically sound but also practically feasible and robust against the evolving landscape of cyber threats [31].
Through this comprehensive analysis, this study articulates the imperative for a strategic overhaul of existing security protocols to accommodate the unique demands of multi-user IoT environments. By addressing the identified vulnerabilities and implementing targeted measures to refine encryption practices and key management, the paper contributes to the IoT security field, paving the way for a more secure, efficient, and user- centric IoT landscape.
2.2 Data usage within the realm of IoT
This section examines the complex security measures for safeguarding data integrity and privacy within the IoT ecosystem, particularly home monitoring systems. The discourse focuses on employing blockchain technology, homomorphic encryption, and privacy-enhancing techniques to tackle the ongoing data security challenge. These technologies become particularly critical in environments susceptible to insider threats, such as unauthorized data access by backend personnel.
Integrating blockchain technology into IoT data transmission protocols marks a strategic advancement in our research, aiming to fortify data security and ensure integrity. While blockchain’s inherent attributes of decentralization, immutabil- ity, and transparency provide a robust foundation for secure interactions among IoT devices and cloud infrastructures, our analysis extends to optimizing these features to address the specific vulnerabilities of IoT ecosystems. By implementing blockchain, we propose not merely adopting its technology but enhancing it to mitigate risks like unauthorized access and data tampering effectively. The decentralized nature of blockchain inherently reduces these risks, and its immutable record-keeping strengthens data reliability and traceability, which is crucial for IoT systems’ integrity [32].
In parallel, our approach to employing homomorphic encryption goes beyond its traditional application, suggesting a novel framework that balances computational intensity with operational efficiency. This advanced encryption method al- lows for data processing and analytics without revealing sensitive information, thus preserving privacy. Our contribution lies in refining this technique to be more feasible for IoT contexts, integrating privacy-preserving mechanisms such as differential privacy and anonymization to safeguard data during transit and analysis [33].
Moreover, our research critically examines blockchain’s practical deployment in IoT, particularly for secure data shar- ing and access control, enhancing the system’s resilience against breaches and ensuring data integrity [34, 35]. We also delve into the policy realm by addressing these technical aspects advocating for regulatory frameworks that support blockchain integration and homomorphic encryption in IoT. This dual approach ensures a comprehensive solution that not only leverages blockchain for data security but also aligns with stringent policy requirements, thereby enhancing the transparency and security of IoT supply chains [36]. Our work underscores the necessity of a cohesive strategy that encapsulates technical innovation and policy development, driving the security and dependability of IoT systems.
Current research is actively addressing the challenges of integrating blockchain with IoT. Initiatives include the de- velopment of resource-efficient blockchain protocols for IoT devices with limited capabilities [37] and exploring blockchain integration with edge computing to enhance performance [38].
The effectiveness of these technological interventions is evaluated across several dimensions. These include the com- munication overhead introduced by blockchain implementations, which can affect IoT systems’ performance, and ho- momorphic encryption’s processing efficiency in resource- constrained environments [39]. Furthermore, the scalability of these solutions is under scrutiny, as they must be capable of supporting the expansive IoT device network and adaptable to centralized and decentralized architectural frameworks.
2.3 Policy formulation within the existing IoT systems frame- work
Uploading data in IoT systems inherently carries risks, including exposure to man-in-the-middle attacks and other security vulnerabilities [24]. For instance, the common practice of employing HTTPS for data transmission, while beneficial for encrypting text, often grapples with issues like untimely key updates or potential attacks on key management centers [26]. Similarly, the low adoption rate of secure DNS protocols further exacerbates these security concerns [28]. A critical evaluation of existing policies reveals gaps in adequately addressing these security challenges. The reliance on outdated encryption schemes or inadequate key management practices underscores the need to reevaluate current approaches and implement more robust security measures. This evaluation extends to proposing enhancements to corporate governance and suggesting industry-wide standards to bolster IoT systems’ security posture. In order to mitigate these identified vulnerabilities, this paper advocates for a multifaceted approach encompassing technical and policy-driven solutions. Adopting advanced encryption standards and implementing secure key management systems are paramount on the technical front. These measures should ensure that data encryption is in transit and that encryption keys are securely and updated promptly to prevent unauthorized access. From a policy perspective, establishing comprehensive guidelines that mandate the adoption of secure protocols and encryption practices across the industry is essential. These policies should encourage regular security audits and adherence to best practices, ensuring that IoT systems remain resilient against emerging threats. Besides, in cases where technical solutions are insufficient, policy interventions become crucial. For example, to address the issue of untimely key updates or vulnerabilities in key management centers, policy mandates could require implementing redundant key management systems or adopting blockchain technology for decentralized key distribution, enhancing the overall security framework.
From these examples, the critical insight emerges that the prevalent security mechanisms in IoT systems are often reactive rather than proactive, failing to anticipate the evolving landscape of cyber threats. This reveals a fundamental issue: the need for a more anticipatory security approach that ad- dresses current vulnerabilities and adapts to future challenges, ensuring sustained protection against the dynamic nature of cyber threats.
3 Technical solutions for enhanced IoT security
3.1 Enhancing IoT upload security: Implementing ECC and QKD
Boosting IoT security with technical methods requires focusing on Advanced Encryption Algorithms. This includes adopting sophisticated cryptographic techniques, especially Elliptic Curve Cryptography (ECC) and Quantum Key Dis- tribution (QKD) [40-42], to strengthen IoT security. These algorithms are discussed in terms of their mathematical foun- dations, advantages, and application strategies for enhancing IoT data security.
ECC is noted for its efficient asymmetric encryption, which provides robust security with smaller keys and is suitable for IoT’s resource constraints. Its strength lies in the complexity of elliptic curve theory, which offers formidable encryption challenges. ECC’s benefits include high security with reduced key sizes, which lessens IoT devices’ computational and energy demands. Implementing ECC involves using optimized cryptographic libraries like micro ECC, designed for de- vices with limited computational capacity. QKD represents a breakthrough in encryption, utilizing quantum mechanics to secure key exchanges. Its principle is that observing a quantum system alters its state, making eavesdropping detectable. QKD’s key security feature is its invulnerability to interception, leveraging quantum properties. Integrating QKD into IoT faces challenges in miniaturizing quantum communication components, with advances in quantum photonics and nanotechnology offering solutions. It should be noted that effective ECC and QKD integration into IoT security requires:
1. Adaptive Cryptographic Frameworks: Crafting systems that dynamically choose the best encryption method based on context and security requirements.
2. Key Lifecycle Management: Developing systems for efficient management of cryptographic keys, focusing on ECC’s and QKD’s unique key attributes.
3. Interoperability and Compliance: Ensuring cryptographic protocols and standards are standardized for seamless security across diverse IoT devices.
4. Continuous Security Audits: Conduct regular security checks to ensure encryption algorithms remain effective against emerging threats, allowing for timely updates and improvements.
3.2 Enhancing IoT security: Optimizing data handling and encryption
In IoT security enhancement through technical strategies, formulating a robust Data Framework for IoT is a key initiative. This framework, designed with precision, aims to protect data interactions within the IoT space, covering collection, management, and dissemination through stringent encryption protocols. It establishes a secure environment that meticu- lously guards data throughout its lifecycle and sets definitive privacy standards to align IoT operations with strict privacy and security benchmarks.
The framework’s core is its encryption-centric architecture, which safeguards data at three crucial lifecycle stages in IoT systems. Data encryption at collection is initially required using advanced cryptographic techniques like ECC, which are suitable for resource-limited environments. It stresses protecting data in transit to cloud or edge computing platforms with protocols such as Transport Layer Security (TLS) or Datagram Transport Layer Security (DTLS), ensuring data integrity and confidentiality. In the data management phase, the focus is on encryption-at-rest to secure stored data within cloud or edge infrastructures, promoting Homomorphic Encryption for processing encrypted data without decryption, thus preserving confidentiality during analytics. During data dissemination, the framework ensures secure data transfer back to IoT de- vices or users with strict authentication and authorization protocols, preventing unauthorized access and maintaining privacy. Furthermore, the framework defines explicit privacy benchmarks aligned with data protection regulations like the GDPR and industry standards to balance operational efficiency with privacy commitments. It incorporates Privacy- by-Design principles, embedding privacy into the IoT data lifecycle and introducing adaptable consent mechanisms for real-time privacy setting adjustments in response to changing user preferences or regulatory updates, ensuring continuous compliance with privacy norms.
For effective implementation, the framework underlines the need for scalable encryption solutions to manage and grow IoT data volumes, interoperability across diverse IoT platforms for seamless, secure data exchanges, and continuous monitoring for security and privacy breaches, enabling rapid responses to maintain data integrity and confidentiality.
4 Policy solutions for IoT security
4.1 Government’s role in regulating data protection and privacy for companies
In exploring the role of governmental intervention in IoT security, it is clear that a robust framework is needed to uphold data integrity and privacy across the IoT landscape. Governments are pivotal in setting the stage for this by establishing comprehensive regulations that dictate how encryption and data management should be handled to secure the digital ecosystem.
Encryption standards are at the heart of these efforts. By mandating the use of advanced encryption techniques, like AES and Elliptic Curve Cryptography (ECC), to protect data during transmission and storage, governments can significantly mitigate the risk of unauthorized access and data breaches. This step ensures that all IoT data transactions and storage processes meet a high-security threshold, safeguarding sensitive information against cyber threats. However, establishing encryption standards is just one piece of the puzzle. Com- prehensive data management legislation is equally crucial. Such legislation should cover the entire spectrum of data handling within IoT systems, from collection and processing to storage and deletion. The aim is to enforce data minimization practices, ensuring that only necessary data is collected and retained and setting stringent guidelines for how long data can be stored and when it should be securely erased. The effectiveness of these regulatory measures hinges on a solid compliance framework and strict enforcement mechanisms. Regular audits are essential to monitor and evaluate the adherence of IoT stakeholders to the set standards, identifying gaps in compliance and recommending necessary adjustments to align with legal requirements. Moreover, a clear penalty system for data protection and privacy violations will emphasize the importance of compliance and act as a deterrent against neglecting cybersecurity practices.
Collaboration between government and industry sectors is also critical for enhancing IoT security. This partnership can facilitate sharing cyber threat intelligence, enabling preemptive actions against emerging threats and bolstering the collective defense mechanism. Furthermore, government incentives for research and development in IoT security can drive innovation in advanced encryption and secure data management technologies. In IoT’s global nature, active participation in inter- national security forums is imperative for governments. This engagement helps shape and adopt global data protection and privacy standards, fostering a unified approach to IoT security that transcends national borders and ensures a consistent and effective defense against global cyber threats. By addressing these facets, the government can significantly contribute to advancing IoT security, creating a safer digital environment that is resilient against the evolving landscape of cyber threats.
4.2 Corporate compliance: Implementing recommended encryption and key management
In addressing policy solutions for IoT security, it is crucial to delve into corporate compliance” to highlight the essential measures. Besides, business strategies must be adopted to align with the proposed advanced encryption algorithms and key management protocols. This discourse aims to provide a nuanced understanding of how corporations can effectively implement encryption standards to enhance the security frame- work of IoT systems and safeguard sensitive data. Emphasizing the integration of state-of-the-art encryption algorithms, the narrative stresses the importance of securing data through- out its lifecycle within IoT ecosystems, including both data in transit and at rest, through the application of recognized encryption methodologies like the Advanced Encryption Standard (AES) and Elliptic Curve Cryptography (ECC).
Furthermore, the discussion extends to the criticality of a comprehensive key management system, highlighting the necessity of secure key storage, periodic key rotation, and reliable key recovery mechanisms to maintain the integrity and accessibility of encrypted data. The dynamic nature of cybersecurity threats requires businesses to remain vigilant and adaptable, necessitating regular reviews of encryption protocols and a proactive approach to vulnerability management to mitigate potential weaknesses in encryption implementations.
Moreover, the discourse underscores the imperative of adhering to regulatory standards and industry best practices, including compliance with relevant data protection regulations and adopting guidelines provided by authoritative bodies such as NIST or ISO. This approach ensures robust encryption and key management and aligns corporate practices with regulatory requirements and industry consensus, thereby bolstering the security posture of IoT systems.
4.3 Enhancing user awareness and consent for data privacy
In the scholarly examination of policy solutions for IoT security, it is essential to address the intricacies of ”User Awareness and Consent.” This area is pivotal as it underlines the necessity for users to be well-informed about the privacy implications that accompany the use of IoT technologies and to have a clear understanding of how their data is utilized. The discourse seeks to present a cohesive framework that not only educates users about the privacy challenges inherent in IoT devices but also equips them with the necessary tools to exercise informed consent regarding the use of their data.
To enhance user awareness, educational initiatives must be implemented to elucidate the types of data collected by IoT devices, the potential privacy risks this collection entails, and the proactive steps users can take to safeguard their personal information. This involves the creation of accessible and transparent privacy policies by IoT device manufacturers and service providers. Such policies should be articulated in clear, straightforward language detailing data collection, usage, and storage specifics while emphasizing users’ rights over their data. Furthermore, integrating real-time notifications within IoT devices and applications is crucial. These notifications aim to inform users about instances of active data collection, providing them with immediate and understandable options to manage their privacy settings effectively. Establishing consent mechanisms is another cornerstone in ensuring user autonomy over personal data within IoT ecosystems. These mechanisms should allow users to give granular consent for various data collection and usage activities, distinguishing between essential functionalities and optional data uses. Moreover, the design of user-friendly consent interfaces is paramount. These interfaces should facilitate users’ easy modification of consent preferences, ensuring the process is intuitive and straightforward.
Additionally, maintaining auditable consent records is essential for fostering transparency and accountability in con- sent practices. Such records should be readily accessible to both users and regulatory entities, thereby upholding a high standard of accountability. It is also crucial that consent mechanisms adhere to rigorous legal and ethical standards, aligning with societal norms and legal mandates. This includes strict compliance with regulatory standards like the GDPR and incorporating ethical principles that prioritize user privacy and autonomy.
5 Implementing the framework
5.1 Governmental implementation of regulatory practices: Legislation and enforcement
Adopting advanced encryption practices is crucial for pro- tecting corporate IoT systems from unauthorized access and data breaches. Thus, corporations are encouraged to commit to high encryption standards by employing protocols like the AES for strong symmetric encryption and ECC for efficient asymmetric encryption scenarios. Such standards should be uniformly applied to all data interactions and storage within the IoT ecosystem, ensuring comprehensive encryption cover- age throughout the data lifecycle, from transmission to storage and processing. Equally important is the rigorous management of user data, which is pivotal in maintaining user privacy and meeting data protection regulations. Corporations should practice data minimization and purpose limitation, collecting only essential data and using it solely for its intended purposes as agreed upon by the users. Furthermore, it is essential to articulate user data policies and outline the data types collected, usage purposes, retention periods, and user rights concerning their data. Additionally, corporations must implement effective and user-friendly consent mechanisms, allowing users granular control over their data and ensuring transparency and consent in data collection and usage. Beyond encryption and data management, corporations should commit to continuous compliance with the security framework and foster a culture of ongoing improvement. This includes conducting regular security audits to identify and rectify vulnerabilities, offering employee training to raise awareness about IoT security principles, and establishing feedback loops to continuously refine the security framework in response to new insights and evolving challenges.
The Table 1 compares different scenarios. We consider the scenario presented in this paper as scenario 1 and compare it with other potential scenarios.
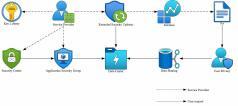
Figure 1. Corporate Adoption of the Framework
5.2 Corporate adoption of the framework: Encryption and data management
Regarding the discussion on Operationalizing the Frame- work within Corporations, we delve into the nuanced strategies of corporations that incorporate the proposed IoT security framework into their operations, and corporate adoption of the framework is shown in Fig. 1. This analysis outlines a comprehensive approach to bolster corporate security measures and adhere to exemplary data stewardship standards, emphasizing key areas such as encryption practices and user data management. Adopting sophisticated encryption practices is the cornerstone of enhancing the security of corporate IoT systems. This involves a commitment to high encryption standards, including protocols like the AES for secure symmetric encryption and ECC for efficient asymmetric scenarios. Such standards are crucial across all facets of data interaction within the IoT ecosystem, ensuring data protection in transit, at rest, or during processing. Equally important is the implementation of a dynamic encryption key management system. This system is fundamental in sustaining the efficacy and integrity of the encryption framework, requiring secure procedures for the generation, storage, rotation, and eventual revocation of keys. Adherence to established key management practices ensures the safeguarding of encryption keys from unauthorized access and maintains the confidentiality of encrypted data.
Parallel to encryption, the meticulous management of user data is paramount. This includes principles like data mini- mization and purpose limitation, ensuring that only necessary data for specific services is collected and used strictly within the bounds of user consent. Corporations must also ensure transparency in their data policies, clearly communicating the nature and use of collected data, retention practices, and users’ rights regarding their data. Robust and user-centric consent mechanisms are vital, providing users with clear control over their data and the ability to easily manage consent for vari- ous data processing activities. This fosters a transparent and consensual environment for data collection and use.
Beyond these practices, corporations must conduct regular security audits to align their IoT systems with the security framework, identify vulnerabilities, and promptly address them. Employee training programs are essential to instill a deep understanding of IoT security principles and practices. Lastly, establishing feedback loops to gather insights from audits, employee experiences, and user feedback is critical. This feedback should guide the continuous refinement of the security framework, ensuring its relevance and effectiveness against the backdrop of evolving security threats.
Table 1. Policy analysis and comparison
Solution |
Policy Analysis |
Encryption |
Technical Drawbacks |
Technology |
1 |
adoption of advanced encryption technologies such as ECC and QKD, along with data management practices and policy solutions |
Yes |
QKD implementation may require quantum communication infrastructure |
ECC, QKD |
Gentry [43] |
Strengthening data protection regulations to ensure data minimization and purpose limitation |
Yes |
May require substantial computational resources |
HE |
Nakamoto [44] |
Implementing strict data governance policies, including regular security audits |
Yes |
May involve implementation and compliance costs |
Blockchain |
Cranor [45] |
Raising user privacy awareness through education and transparent privacy policies |
No |
Users may not understand complex privacy settings |
User-friendly privacy interface |
Rescorla [46] |
Promoting public-private partnerships to and implement standards jointly |
Yes |
Requires cross-industry collaboration and coordination |
encryption protocols |
5.3 Empowering users in IoT privacy and protection
In the discussion on implementing the framework as part of “Policy Solutions for IoT Security,” the focus on ”User Engagement and Empowerment” stands out as a key element.
This section outlines initiatives to enhance users’ understanding of privacy protection in the IoT context and their crucial role in this ecosystem. It seeks to equip users with essential knowledge and tools for secure navigation within the IoT environment, enabling them to make well-informed decisions about their data and privacy.
Education is central to user empowerment, emphasizing the need for programs that improve privacy literacy. These include comprehensive privacy awareness initiatives that explain data privacy complexities, types of data collected by IoT devices, potential privacy risks, and available protective measures. Additionally, workshops and seminars on digital literacy, tailored to the IoT domain, can help users grasp the workings of IoT devices, data flow, and privacy implications. Providing a wealth of online resources, such as guides and FAQs, further supports users in enhancing their understanding of IoT privacy concerns.
Another critical aspect is ensuring users control their data through transparent consent mechanisms. This involves pro- viding users with detailed consent options, enabling them to make informed choices about their data use. Consent interfaces should be user-friendly, allowing easy navigation and understanding of consent scope. Moreover, the ability to adjust consent settings in response to changing privacy preferences underscores the importance of user autonomy in data management.
Advocacy for user rights and the establishment of sup- port structures are also vital. This includes advocating for the recognition and protection of user rights within the IoT landscape and lobbying for legislative and regulatory measures that bolster user rights and privacy. Setting up clear support and dispute resolution mechanisms, such as helplines and online portals, ensures users can address privacy concerns effectively. Additionally, community engagement platforms encourage sharing experiences and strategies related to IoT privacy, fostering a collaborative learning environment.
6 Conclusion
This paper explores the critical relationship between privacy challenges and policy needs in-home monitoring systems within the IoT world. We have developed a framework combining modern technical methods and thorough policy strategies to improve privacy and security in IoT infrastructures. Additionally, we highlighted how advanced encryption like AES and ECC helps protect against unauthorized access, ensuring data remains confidential and intact. Our discussion also emphasized the importance of effective data management, aligning with current data protection laws, and the need for a strong connection between technical solutions and policy actions to manage IoT’s complex privacy issues. We have outlined key research areas that can enhance IoT security, focusing on new encryption technologies, user-centered privacy practices, and the integration of consistent security policies. This study contributes to creating a safer, more reliable IoT environment, emphasizing the need for continuous innovation and collaborative efforts in security and policy development.
References
[1]. HaddadPajouh, H. et al. (2021). A survey on internet of things security: Requirements, challenges, and solutions. Internet of Things, 14, 100129. doi:10.1016/j.iot.2019.100129.
[2]. Kolias, C. et al. (2017). DDoS in the IOT: Mirai and other botnets. Computer, 50(7), 80-84. doi:10.1109/mc.2017.201.
[3]. Khan, Z.A. and Namin, A.S. (2022). A survey of DDOS attack detection techniques for IOT systems using blockchain technology. Electronics, 11(23), 3892. doi:10.3390/electronics11233892.
[4]. Saha, V. et al. (2023). Analysis of blockchain-based techniques for the mitigation of ddos attacks in IOT devices. 2023 14th International Conference on Computing Communication and Networking Technologies (ICCCNT) [Preprint]. doi:10.1109/icccnt56998.2023.10307642.
[5]. Abinaya, M., Prabakeran, S. and Kalpana, M. (2023). Comparative evaluation on various machine learning strategies based on identification of ddos attacks in IOT environment. Heterogenous Computational Intelligence in Internet of Things, 112-130. doi:10.1201/9781003363606-8.
[6]. Kaur, K. and Ayoade, J. (2023). Analysis of ddos attacks on IOT architecture. 2023 10th International Conference on Electrical Engineering, Computer Science and Informatics (EECSI) [Preprint]. doi:10.1109/eecsi59885.2023.10295766.
[7]. Jabar, T. and Mahinderjit Singh, M. (2022). Exploration of mobile device behavior for mitigating Advanced persistent threats (apt): A systematic literature review and conceptual framework. Sensors, 22(13), 4662. doi:10.3390/s22134662.
[8]. Shen, Y. et al. (2022). Prior knowledge based advanced persistent threats detection for IOT in a realistic benchmark. GLOBECOM 2022 - IEEE Global Communications Conference [Preprint]. doi:10.1109/globecom48099.2022.10000811.
[9]. Haque, S. et al. (2023a). Identification of important features at different IOT layers for dynamic attack detection. 2023 IEEE 9th International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE International Conference on High Performance and Smart Computing (HPSC) and IEEE International Conference on Intelligent Data and Security (IDS) [Preprint]. doi:10.1109/bigdatasecurity-hpsc-ids58521.2023.00025.
[10]. Chen, J. and Zhu, Q. (2017). Security as a service for cloud-enabled internet of controlled things under Advanced persistent threats: A contract design approach. IEEE Transactions on Information Forensics and Security, 12(11), 2736-2750. doi:10.1109/tifs.2017.2718489.
[11]. Prabhu, A.S., Nayak, A.G. and Kamath, H.S. (2023). Detection of ddos attacks in IOT devices. 2023 International Conference on Communication, Circuits, and Systems (IC3S) [Preprint]. doi:10.1109/ic3s57698.2023.10169385.
[12]. Veeraiah, V. et al. (2022). Securing online web application for IOT Management. 2022 2nd International Conference on Advance Computing and Innovative Technologies in Engineering (ICACITE) [Preprint]. doi:10.1109/icacite53722.2022.9823733.
[13]. Juvekar, C., Vaikuntanathan, V., Chandrakasan, A. (2018). GAZELLE: A Low Latency Framework for Secure Neural Network Inference. Proceedings of the 27th USENIX Security Symposium, 1651-1669. Retrieved from https://www.usenix.org/conference/usenixsecurity18/presentation/juvekar.
[14]. Mishra, P. et al. (2020). Delphi. Proceedings of the 2020 Workshop on Privacy-Preserving Machine Learning in Practice [Preprint]. doi:10.1145/3411501.3419418.
[15]. Coppola, G., Varde, A.S. and Shang, J. (2023). Enhancing cloud security posture for ubiquitous data access with a cybersecurity framework based management tool. 2023 IEEE 14th Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON) [Preprint]. doi:10.1109/uemcon59035.2023.10316003.
[16]. Mahmood, S. (2019). The anti-data-mining (ADM) framework-better privacy on online social networks and beyond. 2019 IEEE International Conference on Big Data (Big Data) [Preprint]. doi:10.1109/bigdata47090.2019.9006050.
[17]. Yuan, G., Xie, F. and Tan, H. (2022). Construction of Economic Security Early Warning System based on cloud computing and Data Mining. Computational Intelligence and Neuroscience, 2022, 1-12. doi:10.1155/2022/2080840.
[18]. Han, J. et al. (2021). Quantify co-residency risks in the cloud through Deep learning. IEEE Transactions on Dependable and Secure Computing, 18(4), 1568-1579. doi:10.1109/tdsc.2020.3032073.
[19]. Rajalakshmi, B. (2023). Exploring cryptographic paradigms for secure cloud computing. 2023 Second International Conference on Augmented Intelligence and Sustainable Systems (ICAISS) [Preprint]. doi:10.1109/icaiss58487.2023.10250744.
[20]. Sun, J. et al. (2018). A searchable personal health records framework with fine-grained access control in cloud-fog computing. PLOS ONE, 13(11). doi:10.1371/journal.pone.0207543.
[21]. Thenappan, S., Valan Rajkumar, M. and Manoharan, P.S. (2020). Predicting diabetes mellitus using modified support vector machine with cloud security. IETE Journal of Research, 68(6), 3940-3950. doi:10.1080/03772063.2020.1782781.
[22]. HaddadPajouh, H., et al. (2021). A Survey on Internet of Things Security: Requirements, Challenges, and Solutions. Internet of Things, 14, 100129. doi:10.1016/j.iot.2019.100129.
[23]. Kolias, C., et al. (2017). DDoS in the IoT: Mirai and Other Botnets. IEEE Computer, 50(7), 80-84. doi:10.1109/mc.2017.201.
[24]. Smith, J. (2020). The Risks of Insecure Data Transmission in IoT Systems. Journal of Cybersecurity, 8(2), 45-52.
[25]. Brown, A., Davis, M. (2019). The Weaknesses of DES in Modern IoT Security. International Journal of Information Security, 12(3), 201-215.
[26]. Chen, L., Wang, X. (2021). Enhancing IoT Security with TLS: A Case Study. IEEE Transactions on Industrial Informatics, 17(4), 2456-2465.
[27]. Patel, R., Gupta, S. (2022). AES Implementation in IoT Devices: Challenges and Solutions. Security and Communication Networks, 15(1), 1-14.
[28]. Roman, R., Zhou, J., Lopez, J. (2018). On the Features and Challenges of Security and Privacy in Distributed Internet of Things. Computer Networks, 129, 54-71. doi:10.1016/j.comnet.2018.03.013.
[29]. Al-Fuqaha, A., Guizani, M., Mohammadi, M., Aledhari, M., Ayyash, M. (2015). Internet of Things: A Survey on Enabling Technologies, Protocols, and Applications. IEEE Communications Surveys & Tutorials, 17(4), 2347-2376. doi:10.1109/COMST.2015.2444095.
[30]. Zargar, S. T., Joshi, J. (2013). A Survey of Defense Mechanisms Against Distributed Denial of Service (DDoS) Flooding Attacks. IEEE Communications Surveys & Tutorials, 15(4), 2046-2061. doi:10.1109/SURV.2013.080213.00051.
[31]. Baccelli, F., Batty, M., Haenni, R. (2016). Device-to-Device Communication: A Survey of Recent Developments and Research Challenges. IEEE Communications Surveys & Tutorials, 18(3), 1818-1855. doi:10.1109/COMST.2016.2556763.
[32]. Zhang, X., Wang, X. (2020). Blockchain for IoT Security and Privacy: The State of the Art and Challenges. IEEE Internet of Things Journal, 7(10), 7637-7650. doi:10.1109/JIOT.2020.3004708.
[33]. Lauter, K., Naehrig, M. P., Vaikuntanathan, V. (2011). Homomorphic Encryption for Private Search on Untrusted Clouds. Proceedings of the 2011 IEEE Symposium on Security and Privacy (SP ’11), 305-318. doi:10.1109/SP.2011.13.
[34]. Li, M., Li, H., Chen, X. (2018). A Blockchain-Based Privacy-Preserving Data Sharing Scheme for IoT. IEEE Access, 6, 37191-37199. doi:10.1109/ACCESS.2018.2839575.
[35]. Tung, B., Beck, M. (2018). Blockchain and the Internet of Things: A Perfect Match? IEEE Internet Computing, 22(2), 16-19. doi:10.1109/MIC.2018.8395349.
[36]. Xu, L. D., He, W., Li, S. (2019). Blockchain-Based Carbon Trading in the IoT Era. IEEE Transactions on Industrial Informatics, 15(2), 1229-1238. doi:10.1109/TII.2018.2879678.
[37]. Conti, M., Sood, S. K. (2018). Blockchain for the Internet of Things: Opportunities, Challenges, and Solutions. IEEE Internet of Things Journal, 5(2), 1184-1196. doi:10.1109/JIOT.2017.2781227.
[38]. Li, S., Han, K., Liu, X. (2020). A Survey on the Edge Computing for the Internet of Things. IEEE Access, 8, 79437-79458. doi:10.1109/ACCESS.2020.2989818.
[39]. Bos, J. W., Lauter, K., Naehrig, M. P., Vets, I. (2015). Private Predictions on Encrypted Medical Data. Proceedings of the 2015 IEEE Symposium on Security and Privacy (SP ’15), 259-274. doi:10.1109/SP.2015.48.
[40]. Miller, V. S. (1986). Use of Elliptic Curves in Cryptography. Advances in Cryptology - CRYPTO ’85 Proceedings, Lecture Notes in Computer Science, vol 218. Springer, Berlin, Heidelberg. doi:10.1007/3-540-39799-2_11.
[41]. Hankerson, D., Menezes, A. J., Vanstone, S. A. (Eds.). (2004). Guide to Elliptic Curve Cryptography. Springer.
[42]. Scarani, V., Gisin, N. (2009). Quantum Key Distribution: Protocols, Implementations, and Applications. Quantum Information Science and Its Contributions to Information Theory, Lecture Notes in Computer Science, vol 5229. Springer, Berlin, Heidelberg.
[43]. Gentry, C. (2009). Fully Homomorphic Encryption Using Ideal Lattices. Proceedings of the Forty-Eighth Annual ACM Symposium on Theory of Computing (STOC ’09), 169-178.
[44]. Nakamoto, S. (2008). Bitcoin: A Peer-to-Peer Electronic Cash System. Retrieved from https://bitcoin.org/bitcoin.pdf.
[45]. Cranor, L. F., Reisman, D. (2014). The Venn Diagram of Privacy. Proceedings of the 2014 IEEE Symposium on Security and Privacy (SP ’14), 520-532. doi:10.1109/SP.2014.49.
[46]. Rescorla, E. (2015). The Transport Layer Security (TLS) Protocol Version 1.2. RFC 5246. Retrieved from https://tools.ietf.org/html/rfc5246.
Cite this article
Meng,X. (2024). Privacy challenges and policy implications of in-home monitoring systems. Advances in Engineering Innovation,9,24-33.
Data availability
The datasets used and/or analyzed during the current study will be available from the authors upon reasonable request.
Disclaimer/Publisher's Note
The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of EWA Publishing and/or the editor(s). EWA Publishing and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content.
About volume
Journal:Advances in Engineering Innovation
© 2024 by the author(s). Licensee EWA Publishing, Oxford, UK. This article is an open access article distributed under the terms and
conditions of the Creative Commons Attribution (CC BY) license. Authors who
publish this series agree to the following terms:
1. Authors retain copyright and grant the series right of first publication with the work simultaneously licensed under a Creative Commons
Attribution License that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this
series.
2. Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the series's published
version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial
publication in this series.
3. Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and
during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work (See
Open access policy for details).
References
[1]. HaddadPajouh, H. et al. (2021). A survey on internet of things security: Requirements, challenges, and solutions. Internet of Things, 14, 100129. doi:10.1016/j.iot.2019.100129.
[2]. Kolias, C. et al. (2017). DDoS in the IOT: Mirai and other botnets. Computer, 50(7), 80-84. doi:10.1109/mc.2017.201.
[3]. Khan, Z.A. and Namin, A.S. (2022). A survey of DDOS attack detection techniques for IOT systems using blockchain technology. Electronics, 11(23), 3892. doi:10.3390/electronics11233892.
[4]. Saha, V. et al. (2023). Analysis of blockchain-based techniques for the mitigation of ddos attacks in IOT devices. 2023 14th International Conference on Computing Communication and Networking Technologies (ICCCNT) [Preprint]. doi:10.1109/icccnt56998.2023.10307642.
[5]. Abinaya, M., Prabakeran, S. and Kalpana, M. (2023). Comparative evaluation on various machine learning strategies based on identification of ddos attacks in IOT environment. Heterogenous Computational Intelligence in Internet of Things, 112-130. doi:10.1201/9781003363606-8.
[6]. Kaur, K. and Ayoade, J. (2023). Analysis of ddos attacks on IOT architecture. 2023 10th International Conference on Electrical Engineering, Computer Science and Informatics (EECSI) [Preprint]. doi:10.1109/eecsi59885.2023.10295766.
[7]. Jabar, T. and Mahinderjit Singh, M. (2022). Exploration of mobile device behavior for mitigating Advanced persistent threats (apt): A systematic literature review and conceptual framework. Sensors, 22(13), 4662. doi:10.3390/s22134662.
[8]. Shen, Y. et al. (2022). Prior knowledge based advanced persistent threats detection for IOT in a realistic benchmark. GLOBECOM 2022 - IEEE Global Communications Conference [Preprint]. doi:10.1109/globecom48099.2022.10000811.
[9]. Haque, S. et al. (2023a). Identification of important features at different IOT layers for dynamic attack detection. 2023 IEEE 9th International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE International Conference on High Performance and Smart Computing (HPSC) and IEEE International Conference on Intelligent Data and Security (IDS) [Preprint]. doi:10.1109/bigdatasecurity-hpsc-ids58521.2023.00025.
[10]. Chen, J. and Zhu, Q. (2017). Security as a service for cloud-enabled internet of controlled things under Advanced persistent threats: A contract design approach. IEEE Transactions on Information Forensics and Security, 12(11), 2736-2750. doi:10.1109/tifs.2017.2718489.
[11]. Prabhu, A.S., Nayak, A.G. and Kamath, H.S. (2023). Detection of ddos attacks in IOT devices. 2023 International Conference on Communication, Circuits, and Systems (IC3S) [Preprint]. doi:10.1109/ic3s57698.2023.10169385.
[12]. Veeraiah, V. et al. (2022). Securing online web application for IOT Management. 2022 2nd International Conference on Advance Computing and Innovative Technologies in Engineering (ICACITE) [Preprint]. doi:10.1109/icacite53722.2022.9823733.
[13]. Juvekar, C., Vaikuntanathan, V., Chandrakasan, A. (2018). GAZELLE: A Low Latency Framework for Secure Neural Network Inference. Proceedings of the 27th USENIX Security Symposium, 1651-1669. Retrieved from https://www.usenix.org/conference/usenixsecurity18/presentation/juvekar.
[14]. Mishra, P. et al. (2020). Delphi. Proceedings of the 2020 Workshop on Privacy-Preserving Machine Learning in Practice [Preprint]. doi:10.1145/3411501.3419418.
[15]. Coppola, G., Varde, A.S. and Shang, J. (2023). Enhancing cloud security posture for ubiquitous data access with a cybersecurity framework based management tool. 2023 IEEE 14th Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON) [Preprint]. doi:10.1109/uemcon59035.2023.10316003.
[16]. Mahmood, S. (2019). The anti-data-mining (ADM) framework-better privacy on online social networks and beyond. 2019 IEEE International Conference on Big Data (Big Data) [Preprint]. doi:10.1109/bigdata47090.2019.9006050.
[17]. Yuan, G., Xie, F. and Tan, H. (2022). Construction of Economic Security Early Warning System based on cloud computing and Data Mining. Computational Intelligence and Neuroscience, 2022, 1-12. doi:10.1155/2022/2080840.
[18]. Han, J. et al. (2021). Quantify co-residency risks in the cloud through Deep learning. IEEE Transactions on Dependable and Secure Computing, 18(4), 1568-1579. doi:10.1109/tdsc.2020.3032073.
[19]. Rajalakshmi, B. (2023). Exploring cryptographic paradigms for secure cloud computing. 2023 Second International Conference on Augmented Intelligence and Sustainable Systems (ICAISS) [Preprint]. doi:10.1109/icaiss58487.2023.10250744.
[20]. Sun, J. et al. (2018). A searchable personal health records framework with fine-grained access control in cloud-fog computing. PLOS ONE, 13(11). doi:10.1371/journal.pone.0207543.
[21]. Thenappan, S., Valan Rajkumar, M. and Manoharan, P.S. (2020). Predicting diabetes mellitus using modified support vector machine with cloud security. IETE Journal of Research, 68(6), 3940-3950. doi:10.1080/03772063.2020.1782781.
[22]. HaddadPajouh, H., et al. (2021). A Survey on Internet of Things Security: Requirements, Challenges, and Solutions. Internet of Things, 14, 100129. doi:10.1016/j.iot.2019.100129.
[23]. Kolias, C., et al. (2017). DDoS in the IoT: Mirai and Other Botnets. IEEE Computer, 50(7), 80-84. doi:10.1109/mc.2017.201.
[24]. Smith, J. (2020). The Risks of Insecure Data Transmission in IoT Systems. Journal of Cybersecurity, 8(2), 45-52.
[25]. Brown, A., Davis, M. (2019). The Weaknesses of DES in Modern IoT Security. International Journal of Information Security, 12(3), 201-215.
[26]. Chen, L., Wang, X. (2021). Enhancing IoT Security with TLS: A Case Study. IEEE Transactions on Industrial Informatics, 17(4), 2456-2465.
[27]. Patel, R., Gupta, S. (2022). AES Implementation in IoT Devices: Challenges and Solutions. Security and Communication Networks, 15(1), 1-14.
[28]. Roman, R., Zhou, J., Lopez, J. (2018). On the Features and Challenges of Security and Privacy in Distributed Internet of Things. Computer Networks, 129, 54-71. doi:10.1016/j.comnet.2018.03.013.
[29]. Al-Fuqaha, A., Guizani, M., Mohammadi, M., Aledhari, M., Ayyash, M. (2015). Internet of Things: A Survey on Enabling Technologies, Protocols, and Applications. IEEE Communications Surveys & Tutorials, 17(4), 2347-2376. doi:10.1109/COMST.2015.2444095.
[30]. Zargar, S. T., Joshi, J. (2013). A Survey of Defense Mechanisms Against Distributed Denial of Service (DDoS) Flooding Attacks. IEEE Communications Surveys & Tutorials, 15(4), 2046-2061. doi:10.1109/SURV.2013.080213.00051.
[31]. Baccelli, F., Batty, M., Haenni, R. (2016). Device-to-Device Communication: A Survey of Recent Developments and Research Challenges. IEEE Communications Surveys & Tutorials, 18(3), 1818-1855. doi:10.1109/COMST.2016.2556763.
[32]. Zhang, X., Wang, X. (2020). Blockchain for IoT Security and Privacy: The State of the Art and Challenges. IEEE Internet of Things Journal, 7(10), 7637-7650. doi:10.1109/JIOT.2020.3004708.
[33]. Lauter, K., Naehrig, M. P., Vaikuntanathan, V. (2011). Homomorphic Encryption for Private Search on Untrusted Clouds. Proceedings of the 2011 IEEE Symposium on Security and Privacy (SP ’11), 305-318. doi:10.1109/SP.2011.13.
[34]. Li, M., Li, H., Chen, X. (2018). A Blockchain-Based Privacy-Preserving Data Sharing Scheme for IoT. IEEE Access, 6, 37191-37199. doi:10.1109/ACCESS.2018.2839575.
[35]. Tung, B., Beck, M. (2018). Blockchain and the Internet of Things: A Perfect Match? IEEE Internet Computing, 22(2), 16-19. doi:10.1109/MIC.2018.8395349.
[36]. Xu, L. D., He, W., Li, S. (2019). Blockchain-Based Carbon Trading in the IoT Era. IEEE Transactions on Industrial Informatics, 15(2), 1229-1238. doi:10.1109/TII.2018.2879678.
[37]. Conti, M., Sood, S. K. (2018). Blockchain for the Internet of Things: Opportunities, Challenges, and Solutions. IEEE Internet of Things Journal, 5(2), 1184-1196. doi:10.1109/JIOT.2017.2781227.
[38]. Li, S., Han, K., Liu, X. (2020). A Survey on the Edge Computing for the Internet of Things. IEEE Access, 8, 79437-79458. doi:10.1109/ACCESS.2020.2989818.
[39]. Bos, J. W., Lauter, K., Naehrig, M. P., Vets, I. (2015). Private Predictions on Encrypted Medical Data. Proceedings of the 2015 IEEE Symposium on Security and Privacy (SP ’15), 259-274. doi:10.1109/SP.2015.48.
[40]. Miller, V. S. (1986). Use of Elliptic Curves in Cryptography. Advances in Cryptology - CRYPTO ’85 Proceedings, Lecture Notes in Computer Science, vol 218. Springer, Berlin, Heidelberg. doi:10.1007/3-540-39799-2_11.
[41]. Hankerson, D., Menezes, A. J., Vanstone, S. A. (Eds.). (2004). Guide to Elliptic Curve Cryptography. Springer.
[42]. Scarani, V., Gisin, N. (2009). Quantum Key Distribution: Protocols, Implementations, and Applications. Quantum Information Science and Its Contributions to Information Theory, Lecture Notes in Computer Science, vol 5229. Springer, Berlin, Heidelberg.
[43]. Gentry, C. (2009). Fully Homomorphic Encryption Using Ideal Lattices. Proceedings of the Forty-Eighth Annual ACM Symposium on Theory of Computing (STOC ’09), 169-178.
[44]. Nakamoto, S. (2008). Bitcoin: A Peer-to-Peer Electronic Cash System. Retrieved from https://bitcoin.org/bitcoin.pdf.
[45]. Cranor, L. F., Reisman, D. (2014). The Venn Diagram of Privacy. Proceedings of the 2014 IEEE Symposium on Security and Privacy (SP ’14), 520-532. doi:10.1109/SP.2014.49.
[46]. Rescorla, E. (2015). The Transport Layer Security (TLS) Protocol Version 1.2. RFC 5246. Retrieved from https://tools.ietf.org/html/rfc5246.









