1. Introduction
In the last three decades, face recognition technology has attracted much attention [1]. Human beings can process and analyse complex information continuously with the help of their brains and eyes, so they are capable of recognising all kinds of information and processing and analysing the information they have obtained. So face recognition is the same, the technology can require the computer to capture the object and face and the corresponding information processing to achieve similar results.
The essential algorithmic technology of the appropriate framework is what face recognition technology depends on. This involves face detection, picture processing, and image analysis, among other things. The act of scanning a particular region to identify whether there is a human face, as well as the analysis of facial feature data, is known as the face detection algorithm. The location of the face feature data found in the scanned area corresponds to the distribution and placement of faces in the vicinity. The deep learning framework is currently the most used one in face technology [2].
Machine learning, by its very nature, is a specific computational process, alteration techniques do not need to be hard-coded to produce results, and it relies on input data to achieve the task [3]. Generally, machine learning is divided into two parts, (1) unsupervised ML and (2) supervised ML. In the unsupervised part, a set of examples defined ahead of time is usually given for training, which helps obtain conclusions more accurately. In unsupervised learning, the machine is usually given some data, but the relationships between the data and the features must be identified by the machine itself [4].
From the application field of face recognition technology, the application of more frequent sub-fields is security and finance. With the development of technology, the technology also wants the entertainment field, education field, and automotive field to develop. In the financial field, face payment has been developed to a very convenient degree, people only need to scan their face with a mobile phone can be successfully paid, significantly reducing the cost of time, as well as the security of the password. This means researchers will need more accurate and secure technology in the future.
This paper will introduce the techniques related to face recognition. It will be raised from the early algorithm and deep learning stage. Then, this paper will introduce the applications of face recognition technology in three fields: security, entertainment, and finance. Finally, this study will compare the efficiency of different applications. This study explores the relevant applications of face recognition in three areas, enabling a more in-depth understanding of the technology's application in life.
2. Stages of development of significant face recognition technologies
2.1. Early algorithm
2.1.1. Principal componant analysis. Principal Componant Analysis (PCA) is a statistical dimensionality reduction technique used as face feature extraction is widely used. The reason why PCA is a statistical dimensionality reduction technique is that PCA technique will achieve data compression, for example, PCA can compress the data of recognised facial images, and then extract the features of the facial image of the low-dimensional data structure, which can remove useless information to avoid affecting the data. PCA technique retains the essential elements of the data and improves the efficiency of processing the data as well as the accuracy. It saves a lot of time cost. Although the PCA technique can save time and improve efficiency, this must be based on a large enough training data set [5].
2.1.2. Linear discriminate analysis. Linear discrimination analysis is a data separation technique. For image data with labels, using LDA can save much time, LDA can distinguish the direction of different categories of data very well. Still, when the dimension of the image being processed is too high, the difficulty of computation and storage will increase sharply [6].
2.2. Deep learning
Deep learning is an integral and vital part of machine learning, which has revolutionised the field of face recognition, where Convolutional Neural Networks (CNNs) are again an essential part of deep learning. CNNs were developed from artificial neural networks. CNNs have been widely and frequently used in image processing, etc. CNNs also inherit the characteristics of artificial neural networks, and people can directly input raw, unprocessed images to CNNs, which makes image preprocessing much easier [7]. The structural features of CNNs reduce the number of training parameters and replace the manual extraction of features. Overall, CNNs can process images efficiently and accurately.
3. Face recognition technology in specific areas of application
3.1. Face recognition technology in security
Jacob applies a deep learning model is applied for enhancement and face recognition of low-quality surveillance video, by extracting the low-quality video frame by frame to generate high-quality video with a high frame count, the method is based on the model residual dense network (RDN), after that, the high-quality video can be analysed for face recognition, the face recognition technique is based haar-based classifiers [8]. Finally, it is trained and tested. The authors have set up three modules as a process for testing and the resulting face recognition accuracy is 77.65% and the average model score is 82.35% [8]. They also used different tables to help understand the process and the results. It is constructive for surveillance videos related to criminal records.
Ratnaparkhi combined two deep learning methods for the study (MTCNN and FaceNet) and divided the ornamental process into four steps: 1. Face Detection 2. Face Embedding 3. Face Classification 4. Plotting Faces. Using the CNN The CNN model is used to detect the criminal's face, the detected face image is stored as a compressed file, and then the Keras Facent model is loaded using the FaceNet model. Subsequently, Scikit Learn and LabelEncoder were utilised to complete the classification. The authors later showed the amount of data in the graph and obtained an accuracy of 90.909 in the test, the results show that this deep learning is a positive step towards speeding up the pursuit of criminals [9].
3.2. Face recognition technology in the entertainment sector
Mahmood, developed a procedure for the automatic detection and identification of athletes in a match and to derive information about the athlete, the procedure is deployed on the mobile phones of the spectators who visit the stadium, the procedure uses the AdaBoost algorithm for haar-like features for the characterization of the athletes on the field of play, the feature recognition of the faces will be done using the AdaBoost Algorithm for face recognition will be selected using AdaBoost algorithm, Ratnaparkhi has built a complete framework based on the above-mentioned techniques and the article shows the accuracy of face recognition with the change in the number of training images in a graph, as the number of training images increases, the accuracy is almost 100%, the biggest obstacle for face recognition is not the recognition of the face, but the decrease in the accuracy due to the change in the pose of the athlete himself [10].
Cosentino proposes a system for analysing and judging the emotions of a group of people based on different facial expressions, the Waseda Entertainment Robot. In social interaction, socially assistive robots have to deal with multiple users simultaneously instead of a single user. Hence, they must recognise and perform more complex interactions and emotional scenarios. This system is based on the Microsoft Azure cloud computing solution. The system is based on a cloud computing solution from Microsoft Azure. This cloud computing includes two solutions: Solution Face API and Emotion API. So the face recognition part of Face API can be very well responsible for analysing the image and returning the data and location of the face model. The Emotion API is responsible for the emotion analysis and the use of the API will be done in a few milliseconds [11]. This experimental study teaches the robot to analyse human emotions and investigate human-emotional interaction. It can better analyse complex scenarios.
3.3. Face Recognition Technology in the Financial Sector
Vishnuvardhan has tried different technological approaches for training the face recognition model, using Histograms of Oriented Gradients (HOG) face detection, the approach will transfer learning on the face recognition model Facenet [12]. the literature proposes to carry out the process of face recognition in two steps Face recognition will be done in two steps, detection will be done using the HOG method, SVM will be done to classify the objects and after that, Facenet will be used for detection, KNN will also be applied in the detection. after that, the conclusions are 96.67% accurate.
To solve the face and mask recognition problem in financial security prevention, Chen proposed a Gaussian Mixture Model (GMM)-based face recognition method that enhances the bank login system [13]. The technique can successfully determine if the image that has been identified is a mask or an honest face. This is quite helpful in stopping crimes and financial fraud. The technique uses the OpenCV Haar classifier to locate and extract faces from images. Then, many images are trained on the GMM using the features of the detected faces. Lastly, the dlib library of deep learning algorithms detect and generate the face features again. The facial features are then classified using a hierarchical framework, and the similarity between the unknown and training samples is computed.
4. Algorithmic recognition accuracy
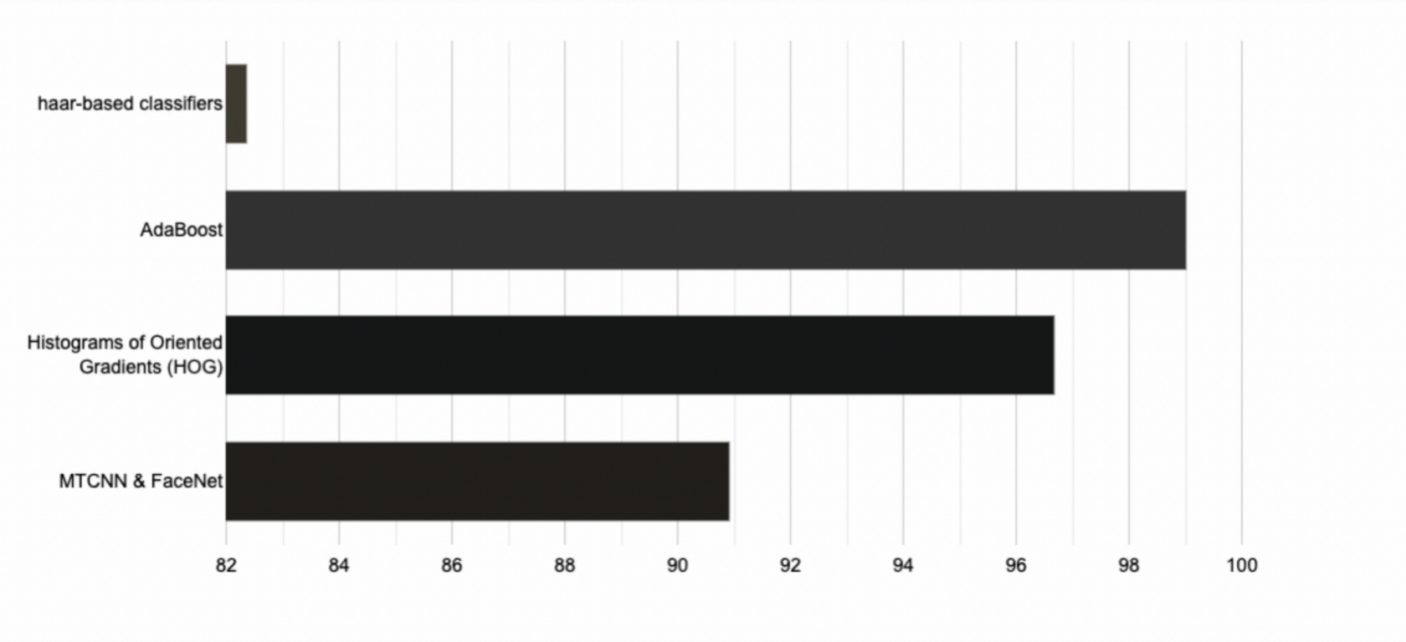
Figure 1. Accuracy of four algorithms applied in different scenarios (Original).
Figure 1 shows the accuracy of different algorithms applied in different domains, people can see that the accuracy of Adaboost is the highest, this is because, on different occasions, the specific application of the method will be different, In the reference, the authors added the body movement recognition, so it leads to a higher accuracy compared to other [5]. This also shows that different algorithms used in different scenarios can lead to different results for using these techniques, researchers need to combine different scenarios to apply in different situations. If they are applied directly without considering the application environment, there is no guarantee that the best results will be achieved.
5. Conclusion
It is undeniable that face recognition technology has permeated every aspect of contemporary life, from security and entertainment to finance. The reviewed literature and studies show the rapid trajectory of face recognition algorithms, transitioning from early approaches such as PCA and LDA to advanced deep learning frameworks such as CNN. The adaptability and effectiveness of this technology in different application scenarios highlight its growing popularity. In security, it helps enhance surveillance and crime detection; in entertainment, it enriches the viewer experience; and in finance, it enhances transaction security and user experience. However, it is also clear that the efficiency and applicability of face recognition algorithms depend on the specific application context. This adaptability highlights the importance of ensuring that these algorithms are fine-tuned to the particular challenges and requirements of the target domain. The next phase of development in face recognition technology aims to address these and other emerging challenges.
Broader dataset collection: to further improve the accuracy and robustness of face recognition systems, there is an urgent need to collect more diverse and representative datasets. This will ensure that these systems are unbiased and practical across different demographic groups.
Multi-modal systems: Combining face recognition with other biometric techniques, such as iris scanning, fingerprint recognition, and voiceprint recognition, can improve the reliability and security of the recognition process.
Enhanced real-time processing: As the demand for real-time applications grows, it will be critical to improve the efficiency of face recognition systems for faster response times.
Privacy issues: With the widespread use of face recognition technology, personal privacy is a growing concern. Future research should address strategies to ensure user consent and data protection.
Addressing challenges: As the technology becomes more widespread, it will face challenges such as obfuscation techniques, adversarial attacks, and changing environmental conditions. It is crucial to address these challenges.
References
[1]. Adjabi I, Ouahabi A, Benzaoui A, Taleb-Ahmed A 2020 Past, present, and future of face recognition: A review Electronics 9 8 1188
[2]. Li L, Mu X, Li S, Peng H 2020 A review of face recognition technology IEEE Access 8 139110-139120
[3]. El Naqa I, Murphy M J 2015 What is machine learning? Springer International Publishing 3-11
[4]. Shah N, Bhagat N, Shah M 2021 Crime forecasting: a machine learning and computer vision approach to crime prediction and prevention Visual Computing for Industry, Biomedicine, and Art 4 1-14
[5]. Li L, Mu X, Li S, Peng H 2020 A review of face recognition technology IEEE Access 8 139110-139120
[6]. Bansal A, Mehta K, Arora S 2012 Face recognition using PCA and LDA algorithm In 2012 second international conference on Advanced Computing & Communication Technologies 251-254
[7]. Wang D, Yu H, Wang D, Li G 2020 Face recognition system based on CNN In 2020 International Conference on Computer Information and Big Data Applications (CIBDA) 470-473
[8]. Jacob J E, Saritha S 2021 Video Enhancement and Low-Resolution Facial Image Reconstruction for Crime Investigation In Intelligent Data Communication Technologies and Internet of Things: Proceedings of ICICI 2020 773-788
[9]. Ratnaparkhi S T, Tandasi A, Saraswat S 2021 Face detection and recognition for criminal identification system In 2021 11th International Conference on Cloud Computing, Data Science & Engineering (Confluence) 773-777
[10]. Mahmood Z, Ali T, Khattak S, Hasan L, Khan S U 2015 Automatic player detection and identification for sports entertainment applications Pattern Analysis and Applications 18 971-982
[11]. Cosentino S, Randria E I, Lin J Y, Pellegrini T, Sessa S, Takanishi A 2018 Group emotion recognition strategies for entertainment robots In 2018 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS) 813-818
[12]. Vishnuvardhan G, Ravi V 2021 Face recognition using transfer learning on facenet: Application to banking operations In Modern Approaches in Machine Learning and Cognitive Science: A Walkthrough: Latest Trends in AI 2 301-309
[13]. Chen Q, Sang L 2018 Face-mask recognition for fraud prevention using Gaussian mixture model Journal of Visual Communication and Image Representation 55 795-801
Cite this article
Yang,W. (2024). Research on algorithm accuracy and the application of facial recognition technologies. Applied and Computational Engineering,46,273-277.
Data availability
The datasets used and/or analyzed during the current study will be available from the authors upon reasonable request.
Disclaimer/Publisher's Note
The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of EWA Publishing and/or the editor(s). EWA Publishing and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content.
About volume
Volume title: Proceedings of the 4th International Conference on Signal Processing and Machine Learning
© 2024 by the author(s). Licensee EWA Publishing, Oxford, UK. This article is an open access article distributed under the terms and
conditions of the Creative Commons Attribution (CC BY) license. Authors who
publish this series agree to the following terms:
1. Authors retain copyright and grant the series right of first publication with the work simultaneously licensed under a Creative Commons
Attribution License that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this
series.
2. Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the series's published
version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial
publication in this series.
3. Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and
during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work (See
Open access policy for details).
References
[1]. Adjabi I, Ouahabi A, Benzaoui A, Taleb-Ahmed A 2020 Past, present, and future of face recognition: A review Electronics 9 8 1188
[2]. Li L, Mu X, Li S, Peng H 2020 A review of face recognition technology IEEE Access 8 139110-139120
[3]. El Naqa I, Murphy M J 2015 What is machine learning? Springer International Publishing 3-11
[4]. Shah N, Bhagat N, Shah M 2021 Crime forecasting: a machine learning and computer vision approach to crime prediction and prevention Visual Computing for Industry, Biomedicine, and Art 4 1-14
[5]. Li L, Mu X, Li S, Peng H 2020 A review of face recognition technology IEEE Access 8 139110-139120
[6]. Bansal A, Mehta K, Arora S 2012 Face recognition using PCA and LDA algorithm In 2012 second international conference on Advanced Computing & Communication Technologies 251-254
[7]. Wang D, Yu H, Wang D, Li G 2020 Face recognition system based on CNN In 2020 International Conference on Computer Information and Big Data Applications (CIBDA) 470-473
[8]. Jacob J E, Saritha S 2021 Video Enhancement and Low-Resolution Facial Image Reconstruction for Crime Investigation In Intelligent Data Communication Technologies and Internet of Things: Proceedings of ICICI 2020 773-788
[9]. Ratnaparkhi S T, Tandasi A, Saraswat S 2021 Face detection and recognition for criminal identification system In 2021 11th International Conference on Cloud Computing, Data Science & Engineering (Confluence) 773-777
[10]. Mahmood Z, Ali T, Khattak S, Hasan L, Khan S U 2015 Automatic player detection and identification for sports entertainment applications Pattern Analysis and Applications 18 971-982
[11]. Cosentino S, Randria E I, Lin J Y, Pellegrini T, Sessa S, Takanishi A 2018 Group emotion recognition strategies for entertainment robots In 2018 IEEE/RSJ International Conference on Intelligent Robots and Systems (IROS) 813-818
[12]. Vishnuvardhan G, Ravi V 2021 Face recognition using transfer learning on facenet: Application to banking operations In Modern Approaches in Machine Learning and Cognitive Science: A Walkthrough: Latest Trends in AI 2 301-309
[13]. Chen Q, Sang L 2018 Face-mask recognition for fraud prevention using Gaussian mixture model Journal of Visual Communication and Image Representation 55 795-801









