1. Introduction
In the evolving landscape of digital technology, Application Programming Interfaces (APIs) serve as critical facilitators of software integration and functionality. As the backbone of modern web and mobile applications, the importance of well-designed APIs cannot be overstated. An API that is efficiently designed not only enhances performance but also plays a pivotal role in the scalability and reliability of software systems. Moreover, as cybersecurity threats evolve, the need for robust security measures in API design and management becomes imperative. Additionally, the overall user experience, determined largely by the API's usability, dictates its adoption and success. This paper addresses these fundamental aspects of API strategy—efficiency, security, and usability—through a detailed analysis supported by mathematical modeling and quantitative research. We explore advanced techniques for load balancing, the efficacy of various caching mechanisms, and the strategic implementation of rate limiting to ensure optimal performance and user satisfaction. The security analysis includes preventative measures against common threats and the application of secure authentication protocols. In terms of usability, the focus is on creating intuitive and easy-to-use APIs that facilitate seamless integration and developer engagement. By examining these elements through the lens of quantitative analysis, the research aims to offer actionable insights and practical guidelines that can significantly improve API design and management practices [1]. This introduction sets the stage for a deep dive into the complexities of API architecture and the strategic considerations that must inform its lifecycle management.
2. Principles of API Design
2.1. Efficiency in Design
The efficiency of an API significantly impacts its performance, affecting both latency and throughput, which are critical for user satisfaction and system scalability. Design choices, from the structure of the API endpoints to the data serialization formats used, play a pivotal role in determining the overall efficiency of an API. A detailed examination of API design patterns reveals that RESTful APIs, while versatile, can suffer from increased latency due to the over-fetching or under-fetching of data. GraphQL emerges as an efficient alternative, allowing clients to specify exactly what data is needed, thus reducing unnecessary data transfer and improving latency [2]. Throughput, the number of requests a system can handle within a given timeframe, can be significantly impacted by the choice of data serialization format. JSON, while human-readable, may not be as efficient as binary formats like Protocol Buffers in terms of parsing and serialization speed, directly affecting throughput. Mathematical modeling of API calls per second (CPS) versus server response time reveals an inversely proportional relationship. As the CPS increases, the server takes longer to respond, indicating a need for efficient design to maintain low latency.
A model incorporating Little’s Law, L=λW, where L is the average number of requests in the system, λ is the arrival rate, and W is the average waiting time, can predict the impact of design changes on system congestion and latency [3].
2.2. Security Considerations
Security in API design encompasses safeguarding data integrity, confidentiality, and availability. Incorporating security measures from the outset is paramount to mitigating vulnerabilities and protecting against unauthorized access and data breaches. Common threats to APIs include SQL injection, where attackers manipulate a SQL query via the API input, and Man-in-the-Middle (MitM) attacks, where communications between the client and server are intercepted. To counter these, parameterized queries and TLS encryption are essential. OAuth 2.0 provides a robust framework for secure client-server authentication, while JSON Web Tokens (JWT) offer a method for securely transmitting information between parties as a JSON object. A quantitative risk analysis involves calculating the potential impact of security threats and the likelihood of their occurrence. The risk level can be determined using the formula Risk=Impact×Likelihood. High-risk areas require immediate attention, dictating the prioritization of security efforts. For example, if an API endpoint handling sensitive user data has a high likelihood of being exploited and the impact of a breach is severe, it should be secured as a priority [4]. Table 1 provides an overview of potential security vulnerabilities in API design.
Table 1. Quantitative Risk Analysis of Common Security Threats to APIs
Threat Type | Description | Likelihood | Impact | Risk Level |
SQL Injection | Attackers manipulate SQL queries via API input, altering database commands. | 0.7 | 0.9 | 0.63 |
Man-in-the-Middle | Intercept communications between clients and servers to steal sensitive data. | 0.4 | 0.8 | 0.32 |
Cross-Site Scripting | Inject malicious scripts into web pages viewed by other users via API. | 0.5 | 0.6 | 0.30 |
Token Hijacking | Unauthorized access to API by hijacking authentication tokens. | 0.6 | 0.7 | 0.42 |
2.3. Enhancing Usability
Usability in API design ensures that APIs are intuitive and accessible, fostering a positive developer experience and facilitating seamless integration. An API's usability can be enhanced by adopting consistent naming conventions, offering comprehensive documentation, and providing actionable error messages. These elements reduce the cognitive load on the developer and accelerate the integration process. Additionally, implementing versioning strategies such as semantic versioning helps manage changes without disrupting existing integrations [5]. Quantitative user research, such as surveys and A/B testing, provides empirical data on how developers interact with APIs. This data can inform design improvements, making APIs more intuitive, as shown in Table 2. For instance, a survey might reveal that developers find certain endpoint names confusing, leading to an update in naming conventions. Mathematical modeling can predict user engagement based on usability improvements. For example, a regression model could correlate the reduction in integration time with the comprehensiveness of documentation, demonstrating the value of investing in clear, detailed API guides.
Table 2. Quantitative User Research Outcomes for API Usability Enhancements
Study Type | Description | Metric | Value |
Developer Survey | Survey to assess developer satisfaction with current API naming conventions. | Satisfaction Score | 82% |
A/B Testing | A/B testing to compare user responses to different API documentation formats. | Preference Rate | 75% prefer new format |
Integration Time Analysis | Analysis of integration time before and after improvements in API documentation. | Time Reduction | 30% reduction |
Through a detailed exploration of efficiency, security, and usability considerations, this analysis underscores the complex interplay of factors that inform API design [6]. By adopting a quantitative approach and utilizing mathematical models, developers and architects can make informed decisions, crafting APIs that not only meet technical requirements but also prioritize security and user experience.
3. Lifecycle Management of APIs
3.1. Version Control Strategies
In the realm of API management, implementing a robust version control strategy is indispensable for accommodating new features, bug fixes, and security updates without adversely affecting the existing client implementations. Semantic versioning (SemVer) has emerged as a prevalent method due to its clear structure and predictability, which significantly aids in maintaining backward compatibility and API stability. Semantic versioning delineates changes using a three-part format: MAJOR.MINOR.PATCH. The MAJOR version increment signals incompatible API changes, MINOR version for adding functionality in a backward-compatible manner, and PATCH version for backward-compatible bug fixes [7]. A quantitative analysis of version updates and their impact on API consumers can reveal patterns in the adoption rates and satisfaction levels, informing the optimal frequency and scale of version updates. For instance, a study might track the deployment of MINOR updates and correlate these with a decrease in reported issues or an increase in feature usage, providing empirical data to support the strategy of frequent, smaller updates rather than rare, major revamps. A mathematical model for API stability can be formulated by defining stability as a function of the frequency of breaking changes (major version updates) and the extent of adoption of backward-compatible changes (minor and patch updates). Let S(t) represent the stability of an API at time t, defined as S(t)=1−T(t)M(t), where M(t) is the number of major updates and T(t) is the total number of updates (major, minor, and patch) in a given period. This model highlights the importance of minimizing breaking changes to maintain high stability and encourage steady adoption among users [8].
3.2. Documentation Practices
Comprehensive, clear, and up-to-date documentation is a cornerstone of API usability and developer productivity. It serves not only as a guide for implementing and troubleshooting API integrations but also as a bridge between the API's capabilities and its consumers' needs. The quality of API documentation can be quantitatively analyzed by measuring developer engagement metrics such as time to first successful API call, frequency of documentation access, and direct feedback scores from user surveys. Additionally, the correlation between documentation completeness (coverage of endpoints, parameters, and examples) and developer productivity metrics (such as integration time and bug rate) can be studied. For example, regression analysis could be employed to identify how improvements in documentation clarity reduce the number of support tickets raised by developers, indicating increased self-sufficiency and lower integration costs [9]. An effective framework for API documentation includes principles such as modularity, allowing for easy updates; interactivity, providing executable examples; and accessibility, ensuring that documentation is easy to navigate. Automating the generation of documentation from the source code can ensure accuracy and timeliness. A comprehensive documentation suite might include structured guides for different use cases, autogenerated API reference documentation, and interactive API explorers that allow developers to test endpoints in real-time [10]. The impact of such a framework on developer engagement and productivity can be quantitatively assessed, demonstrating the value of high-quality documentation in fostering a positive developer experience.
3.3. Security Management
The management of API security is an ongoing process that involves monitoring, assessing, and mitigating potential security threats throughout the API lifecycle. Effective security management practices are crucial for protecting sensitive data and ensuring user trust, as shown in Figure 1. Quantitative methods for assessing security risks involve calculating the potential impact of various security threats and the likelihood of their occurrence. This can be achieved through techniques such as threat modeling and risk scoring systems. For example, the Common Vulnerability Scoring System (CVSS) provides a way to capture the principal characteristics of a security vulnerability and produce a numerical score reflecting its severity. A mathematical model for evaluating the effectiveness of security practices might quantify the reduction in risk as a function of the security measures implemented. For instance, let Ri represent the initial risk score of a given vulnerability, and Rf represent the final risk score after implementing specific security measures [11]. The effectiveness of the security practice can be evaluated as E=RiRi−Rf, where a higher value of E indicates greater effectiveness in reducing the vulnerability's risk. This model enables organizations to quantitatively assess the impact of different security practices, such as authentication mechanisms, encryption protocols, and regular security audits, on the overall security posture of their APIs.
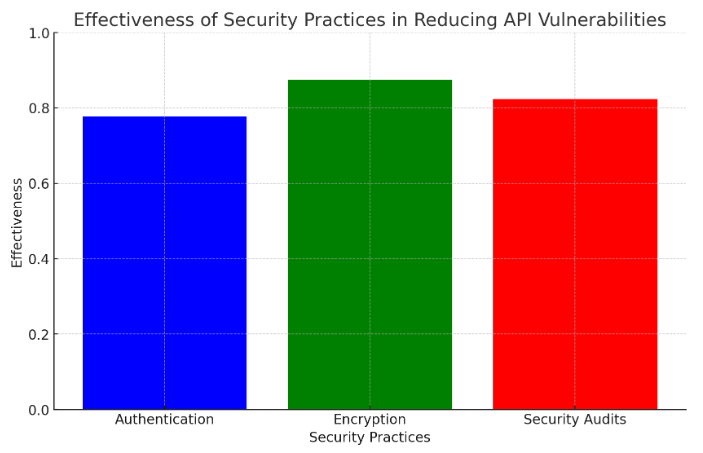
Figure 1. Effectiveness of Security Practices in Reducing API Vulnerabilities
4. Optimizing API Performance
4.1. Load Balancing and Scalability
Load balancing involves distributing incoming API requests across multiple servers to optimize resource utilization and maximize throughput. This technique not only enhances the API's ability to handle large volumes of traffic but also improves overall system reliability by preventing any single server from becoming a bottleneck. To quantify the effectiveness of load balancing strategies, we can model the traffic distribution using Poisson processes, where requests are described by lambda (λ), the rate of request arrivals. Employing round-robin and weighted distribution strategies, we calculate the expected response time and throughput under each strategy using queueing theory models such as M/M/1 and M/M/c queues. For instance, in an M/M/1 queue model—representing a single-server queueing system—the average response time T can be modeled as \( T=\frac{1}{μ-γ} \) , where µ is the service rate. In scenarios where load balancing is implemented, the model adjusts to an M/M/c queue, where c represents multiple servers. Here, the Erlang B formula can be applied to predict the probability of system saturation, thereby guiding decisions on the optimal number of servers needed for effective load balancing. Further, scalability can be addressed through auto-scaling policies which dynamically adjust the number of active servers based on current demand. This can be mathematically modeled using control theory, specifically applying feedback loops where the output (current server load) continuously adjusts the input (number of servers). For example, a proportional-integral-derivative (PID) controller can be utilized to fine-tune the system's responsiveness to changes in load, ensuring that the scale of the infrastructure matches the demand without undue delay or excess capacity.
4.2. Caching Mechanisms
Caching is critical for improving the response time of APIs by storing copies of frequently accessed data points. This section quantitatively analyzes the impact of various caching strategies on API performance. The effectiveness of caching can be measured in terms of hit rate—the proportion of requests that can be served from the cache rather than the backend system. To model this, we use the cache hit rate equation H=1−e−λtc, where λ is the request rate to the cache and tc is the average time a data point remains in the cache before being updated or evicted. By applying different caching strategies—local caching, distributed caching, and reverse proxy caching—we evaluate the performance improvements using simulations based on real-world API usage patterns. For instance, local caching, which stores data on the same server as the API, can be modeled using a simple least recently used (LRU) algorithm. The effectiveness of this approach in different configurations can be studied by varying the cache size and the request pattern, using a Markov chain to predict the probability of cache misses and subsequent hits. Moreover, the application of distributed caching involves multiple cache servers, which can be analyzed using network flow models to understand the optimal distribution of data across servers. This setup minimizes latency by geographically distributing the cache closer to the user base, and we can use graph theory to model the shortest path for data retrieval, thus minimizing response times.
4.3. Rate Limiting and Throttling
Rate limiting and throttling are essential for managing the consumption of API resources, preventing abuse, and ensuring fair access. Mathematical models such as the token bucket and leaky bucket can be used to design these controls effectively. The token bucket algorithm allows a certain capacity of requests (tokens) to accumulate at a predefined rate, which can be modeled using a differential equation dt/dQ=r−λ, where Q is the number of tokens in the bucket, r is the token rate, and λ is the request rate. Through simulations, we can analyze the impact of different configurations of token rates and bucket sizes on API performance and user experience. For example, by setting different rates r and bucket capacities, we can predict the overflow probability using the probability mass function of the token bucket's state. This analysis helps in understanding how aggressive the rate limiting should be to prevent service degradation during peak loads. Additionally, adaptive throttling mechanisms can be modeled using a dynamic feedback system where the limit adapts based on the current load. By employing a control loop, such as those used in industrial automation, the API can dynamically adjust the rate limits based on real-time usage statistics, thereby ensuring optimal performance even under fluctuating load conditions.
5. Conclusion
The study presented herein emphasizes a strategic approach to API design and management that prioritizes efficiency, security, and usability. By integrating mathematical models and quantitative analysis, the research provides a nuanced understanding of how different design choices and management practices affect API performance and user experience. The findings advocate for a balanced approach to API development, where performance optimization, security integrity, and user-centric design are seen as interconnected facets of a successful API strategy. For organizations aiming to leverage APIs as a core component of their digital infrastructure, the insights derived from this study offer a valuable blueprint for achieving robust, scalable, and user-friendly APIs. Ultimately, the adoption of these well-founded strategies will not only enhance the technical capabilities of APIs but also their strategic value in driving business success.
References
[1]. Singh, Maan, et al. "Cocrystals by design: a rational coformer selection approach for tackling the API problems." Pharmaceutics 15.4 (2023): 1161.
[2]. Nam, Daye, et al. "Improving API Knowledge Discovery with ML: A Case Study of Comparable API Methods." 2023 IEEE/ACM 45th International Conference on Software Engineering (ICSE). IEEE, 2023.
[3]. Heinonen, Ava, and Fabian Fagerholm. "Understanding initial API comprehension." 2023 IEEE/ACM 31st International Conference on Program Comprehension (ICPC). IEEE, 2023.
[4]. Constant-Inglis, Honey. Archaeological Interpretive Design for Wanuskewin Heritage Park From The Indigenous Perspective:" astam api: Stories of Indigenous Archaeology". Diss. University of Saskatchewan, 2023.
[5]. Lappalainen, Yrjo, and Nikesh Narayanan. "Aisha: A custom AI library chatbot using the ChatGPT API." Journal of Web Librarianship 17.3 (2023): 37-58.
[6]. Arcolini, Davide. Full Lifecycle API Management: Microgateway Infrastructural Pattern adopting Kong Gateway. Diss. Politecnico di Torino, 2023.
[7]. Charismiadis, Anastasios-Stavros, et al. "The 3GPP common API framework: Open-source release and application use cases." 2023 Joint European Conference on Networks and Communications & 6G Summit (EuCNC/6G Summit). IEEE, 2023.
[8]. Efuntade, Olubunmi Omotayo, Alani Olusegun Efuntade, and FCA FCIB. "Application Programming Interface (API) And Management of Web-Based Accounting Information System (AIS): Security of Transaction Processing System, General Ledger and Financial Reporting System." J. Account. Financ. Manag 9.6 (2023): 1-18.
[9]. Mbau, Rahab, et al. "Analysing the efficiency of health systems: a systematic review of the literature." Applied health economics and health policy 21.2 (2023): 205-224.
[10]. Quito, Byron, et al. "Spatiotemporal influencing factors of energy efficiency in 43 European countries: a spatial econometric analysis." Renewable and Sustainable Energy Reviews 182 (2023): 113340.
[11]. Djalilova, Zarnigor. "PEDAGOGICAL EDUCATIONAL TECHNOLOGY: ESSENCE, CHARACTERISTICS AND EFFICIENCY." Академические исследования в современной науке 2.23 (2023): 29-38.
Cite this article
Xie,N. (2024). Strategic approaches to API design and management. Applied and Computational Engineering,64,229-235.
Data availability
The datasets used and/or analyzed during the current study will be available from the authors upon reasonable request.
Disclaimer/Publisher's Note
The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of EWA Publishing and/or the editor(s). EWA Publishing and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content.
About volume
Volume title: Proceedings of the 6th International Conference on Computing and Data Science
© 2024 by the author(s). Licensee EWA Publishing, Oxford, UK. This article is an open access article distributed under the terms and
conditions of the Creative Commons Attribution (CC BY) license. Authors who
publish this series agree to the following terms:
1. Authors retain copyright and grant the series right of first publication with the work simultaneously licensed under a Creative Commons
Attribution License that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this
series.
2. Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the series's published
version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial
publication in this series.
3. Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and
during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work (See
Open access policy for details).
References
[1]. Singh, Maan, et al. "Cocrystals by design: a rational coformer selection approach for tackling the API problems." Pharmaceutics 15.4 (2023): 1161.
[2]. Nam, Daye, et al. "Improving API Knowledge Discovery with ML: A Case Study of Comparable API Methods." 2023 IEEE/ACM 45th International Conference on Software Engineering (ICSE). IEEE, 2023.
[3]. Heinonen, Ava, and Fabian Fagerholm. "Understanding initial API comprehension." 2023 IEEE/ACM 31st International Conference on Program Comprehension (ICPC). IEEE, 2023.
[4]. Constant-Inglis, Honey. Archaeological Interpretive Design for Wanuskewin Heritage Park From The Indigenous Perspective:" astam api: Stories of Indigenous Archaeology". Diss. University of Saskatchewan, 2023.
[5]. Lappalainen, Yrjo, and Nikesh Narayanan. "Aisha: A custom AI library chatbot using the ChatGPT API." Journal of Web Librarianship 17.3 (2023): 37-58.
[6]. Arcolini, Davide. Full Lifecycle API Management: Microgateway Infrastructural Pattern adopting Kong Gateway. Diss. Politecnico di Torino, 2023.
[7]. Charismiadis, Anastasios-Stavros, et al. "The 3GPP common API framework: Open-source release and application use cases." 2023 Joint European Conference on Networks and Communications & 6G Summit (EuCNC/6G Summit). IEEE, 2023.
[8]. Efuntade, Olubunmi Omotayo, Alani Olusegun Efuntade, and FCA FCIB. "Application Programming Interface (API) And Management of Web-Based Accounting Information System (AIS): Security of Transaction Processing System, General Ledger and Financial Reporting System." J. Account. Financ. Manag 9.6 (2023): 1-18.
[9]. Mbau, Rahab, et al. "Analysing the efficiency of health systems: a systematic review of the literature." Applied health economics and health policy 21.2 (2023): 205-224.
[10]. Quito, Byron, et al. "Spatiotemporal influencing factors of energy efficiency in 43 European countries: a spatial econometric analysis." Renewable and Sustainable Energy Reviews 182 (2023): 113340.
[11]. Djalilova, Zarnigor. "PEDAGOGICAL EDUCATIONAL TECHNOLOGY: ESSENCE, CHARACTERISTICS AND EFFICIENCY." Академические исследования в современной науке 2.23 (2023): 29-38.









