1. Introduction
The increasing complexity of integrated circuits has elevated the significance of chip design verification in the development process. Adequate verification ensures the correctness of chip functionality and substantially reduces the cost of bug fixes in later stages, ultimately shortening time-to-market. Traditional verification methods face numerous challenges, including insufficient coverage, time-consuming processes, and high labor costs. The detection and localization of bugs become particularly challenging at the Register Transfer Level (RTL) [1] code stage due to design complexity and abstraction. As design sizes grow exponentially, the verification effort often accounts for a significant portion of the chip development cycle. The industry needs more efficient and reliable verification techniques to keep pace with the rapid advancements in chip design complexity.
Artificial Intelligence (AI) [2] technologies and machine learning have demonstrated remarkable potential across various domains in recent years. In chip design verification, AI techniques show promise in automatically detecting potential issues in RTL code by learning from extensive historical design data and bug patterns. This approach can significantly enhance verification efficiency and quality. AI-powered verification tools can analyze vast amounts of code, identify subtle patterns, and predict potential bugs that human engineers might overlook. [3] Applying machine learning algorithms to RTL analysis can uncover complex relationships and dependencies within the code, leading to more comprehensive bug detection. AI models can continuously improve performance through exposure to new designs and feedback, adapting to evolving verification challenges.
This research aims to develop an AI-driven approach for enhancing chip design verification through automated bug detection in RTL code. The primary objectives include designing a novel deep learning architecture tailored for RTL code analysis, developing efficient techniques for RTL code feature extraction and representation, implementing an attention mechanism to focus on critical code segments, and leveraging transfer learning to improve model performance across different chip designs.
The main contributions of this work encompass a comprehensive AI framework for RTL bug detection that integrates advanced machine learning techniques with domain-specific knowledge of chip design, a novel data preprocessing pipeline that effectively captures the syntactic and semantic features of RTL code, an innovative attention-based neural network model that significantly improves bug detection accuracy compared to traditional methods, and extensive experimental evaluation on real-world chip designs demonstrating the effectiveness and efficiency of the proposed approach. This research advances the state-of-the-art in chip design verification, paving the way for more reliable and efficient development of complex integrated circuits.
2. Background and Related Work
Register Transfer Level (RTL) code forms the foundation of digital circuit design, representing the behavior of a system in terms of data flow between registers and the logical operations performed on that data. Common bug types in RTL code include logic errors, timing violations, synchronization issues, and resource conflicts. Logic errors often manifest as incorrect boolean expressions, incomplete case statements, or improper handling of edge cases. [4] Timing violations may occur due to setup and hold time violations, clock domain crossing issues, or improper reset sequencing. Synchronization problems can arise from incorrect handshaking protocols or misaligned data transfers between modules. Resource conflicts typically involve improper sharing of hardware resources, leading to contention and unpredictable behavior. Table 1 presents a classification of common RTL bug types with their characteristics and potential impacts.
Table 1. Classification of Common RTL Bug Types
Bug Category | Characteristics | Potential Impacts |
Logic Errors | Incorrect boolean expressions, incomplete case statements | Functional failures, incorrect output |
Timing Violations | Setup/hold violations, clock domain crossing issues | Metastability, data corruption |
Synchronization Issues | Improper handshaking, misaligned data transfers | Data loss, system deadlock |
Resource Conflicts | Improper sharing of hardware resources | Contention, unpredictable behavior |
Simulation remains a cornerstone of chip design verification, allowing designers to model and analyze the behavior of RTL code under various input conditions. This method involves creating test benches that apply stimuli to the design and observe its responses. Simulators execute the RTL code and testbench, providing waveforms and logs for analysis. While simulation offers flexibility and ease of use, it faces challenges in achieving comprehensive coverage for complex designs due to the vast state space. Advanced techniques such as constrained random and coverage-driven verification aim to improve simulation efficiency and effectiveness.
Formal verification employs mathematical techniques to prove or disprove the correctness of a design concerning a specified formal property. [5] This method can exhaustively verify design properties without the need for simulation vectors. Formal verification approaches include model checking, theorem proving, and equivalence checking. Model checking explores the entire state space of a design to verify temporal logic properties. Theorem proving uses mathematical reasoning to establish design correctness. While formal verification provides rigorous guarantees, it often faces scalability issues for large designs due to state space explosion.
Equivalence checking verifies the functional equivalence between two representations of a design, typically between RTL and gate-level implementations or between different versions of RTL code. This method ensures that design optimizations or transformations preserve the original functionality. Equivalence checking algorithms typically use Boolean satisfiability (SAT) [6] solvers or Binary Decision Diagrams (BDDs) to compare the logic functions of corresponding outputs in the two designs. While effective for verifying synthesized designs, equivalence checking may not detect high-level design errors or specification mismatches.
Machine learning techniques have shown promise in various code analysis tasks, including bug detection, code completion, and program synthesis. Supervised learning approaches, such as Support Vector Machines (SVMs) and Random Forests, have been applied to classify code segments as buggy or clean based on extracted features. Deep learning models, particularly Recurrent Neural Networks (RNNs) and Transformers, have successfully captured sequential dependencies in code. These models can learn complex patterns and relationships within code structures, enabling more sophisticated bug detection and code understanding.
While AI-assisted chip verification methods have shown promise, they face several limitations. Current approaches often struggle with the high dimensionality and complexity of [7] RTL code, leading to scalability issues for large designs. Many existing methods rely heavily on hand-crafted features, which may not capture all relevant aspects of the code and can be time-consuming to develop. The interpretability of AI models remains a challenge, making it difficult for designers to understand and trust the model's decisions. The need for large, high-quality datasets of RTL code with annotated bugs hinders the development and evaluation of robust AI models for chip verification.
3. Proposed AI-Driven RTL Bug Detection Method
The proposed AI-driven RTL bug detection system comprises several interconnected modules designed to efficiently process RTL code, extract relevant features, and identify potential bugs. Figure 1 illustrates the system architecture, highlighting the data flow and key components. The system begins with RTL code input, which undergoes preprocessing and feature extraction. The extracted features are then fed into a deep learning model for bug detection. A classification module processes the model's output, presenting the results through an interpretable visualization interface.
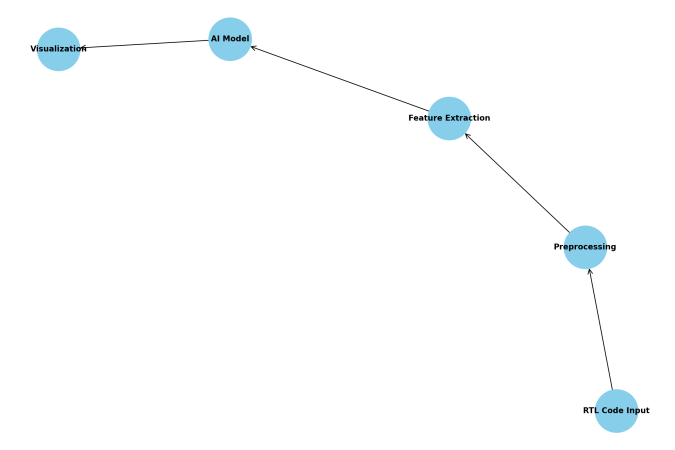
Figure 1. System Architecture Diagram
The RTL code parsing module utilizes a custom-built parser based on ANTLR (Another Tool for Language Recognition) to convert the input Verilog or VHDL code into an Abstract Syntax Tree (AST). This AST representation captures the hierarchical structure of the code, facilitating subsequent analysis and feature extraction. Table 2 presents the key elements extracted during the parsing process.
Table 2. Key Elements Extracted During RTL Code Parsing
Element Type | Description | Relevance to Bug Detection |
Module Declarations | Hierarchical structure of the design | Identifying scope and connectivity issues |
Port Declarations | Input/output interfaces | Detecting interface mismatches |
Signal Declarations | Internal signals and their types | Identifying type mismatches and unused signals |
Always Blocks | Sequential logic descriptions | Analyzing timing and synchronization issues |
Combinational Logic | Continuous assignments and case statements | Detecting logical errors and incomplete cases |
Parameter Definitions | Design constants and configurations | Identifying parameter-related bugs |
The feature extraction process transforms the parsed RTL code into numerical and categorical features suitable for machine learning models. We employ a combination of traditional software metrics and novel RTL-specific features. The primary feature categories include structural metrics that quantify the complexity of the RTL design, temporal metrics that capture timing-related characteristics, semantic metrics that represent the meaning and intent of the code, and code style metrics that measure adherence to coding standards.
The core of our bug detection system is a novel deep learning architecture that combines Convolutional Neural Networks (CNNs) and Long Short-Term Memory (LSTM) networks. Figure 2 depicts the model architecture designed to capture both local and global patterns in the RTL code.
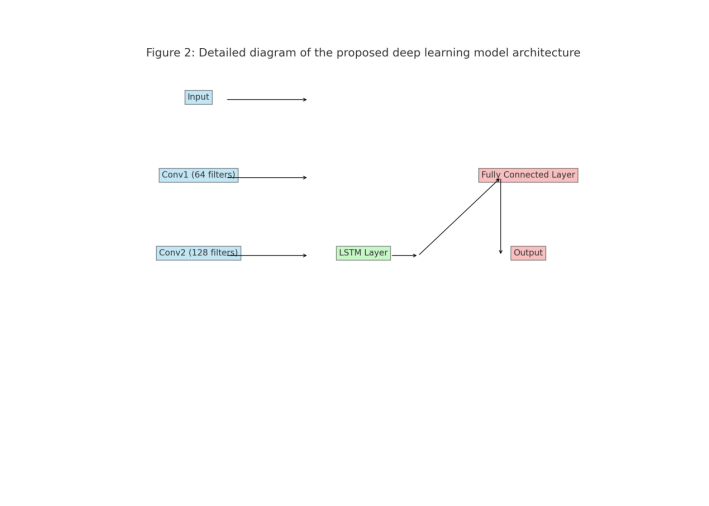
Figure 2. Detailed Diagram of the Proposed Deep Learning Model Architecture
The CNN layers extract local features from the input representations, while the LSTM layers model long-range dependencies in the code. The model architecture consists of an input layer that receives the preprocessed RTL code features, an embedding layer that transforms input features into dense vector representations, multiple convolutional layers with different kernel sizes to capture local patterns, bidirectional LSTM layers to model sequential dependencies, a multi-head self-attention mechanism to focus on critical code segments, fully connected layers for feature combination and classification, and an output layer with sigmoid activation for binary classification (bug/no bug).
We incorporate a multi-head self-attention mechanism to enhance the model's ability to focus on critical code segments. This attention layer allows the model to weigh the importance of different parts of the input sequence dynamically. The attention mechanism is implemented through query, key, and value computation, attention scores calculation, softmax application, and weighted sum computation of the final attention output.
We employ transfer learning techniques to leverage knowledge from pre-existing RTL designs and improve generalization. The model is pre-trained on a large corpus of RTL code and then fine-tuned on specific design projects. This approach allows the model to capture general RTL patterns and adapt to project-specific nuances.
We construct a comprehensive dataset of RTL code samples annotated with known bugs. The dataset includes designs from various domains, ensuring broad coverage of potential bug types. The dataset composition includes processor cores, memory controllers, communication interfaces, cryptographic modules, image processing units, and miscellaneous logic.
We employ a multi-task learning approach to simultaneously detect and classify RTL bugs. The loss function combines binary cross-entropy for bug detection and categorical cross-entropy for bug classification. We utilize Bayesian optimization for hyperparameter tuning, exploring key parameters such as learning rate, batch size, number of CNN filters, LSTM [8]hidden units, and attention heads.
The trained model processes input RTL code and outputs bug detection probabilities and classification scores. We employ a threshold-based approach for final bug detection decisions, with the threshold determined through ROC curve analysis on a validation set.
To enhance the interpretability of the model's decisions, we implement a visualization module that highlights suspicious code segments and provides explanations for detected bugs. The module generates heat maps overlaid on the original RTL code, indicating the regions that contributed most significantly to the bug detection decision.
4. Experimental Setup and Evaluation
The dataset for evaluating the proposed AI-driven RTL bug detection method comprises various RTL designs from multiple domains. We collected RTL code samples from open-source projects, industry collaborations, and synthetic generation techniques. [9]The dataset includes both bug-free and buggy code samples, with bugs manually annotated by experienced RTL designers.
To comprehensively assess the performance of the proposed method, we employ a range of evaluation metrics. These metrics capture various aspects of bug detection accuracy, classification performance, and model efficiency. We use accuracy to measure the overall correctness of bug detection, reflecting the proportion of correctly classified samples across all instances. Precision quantifies the proportion of correct bug detections among all detected bugs, while recall represents the proportion of actual bugs successfully identified. The F1 score, as the harmonic mean of precision and recall, provides a balanced perspective of these two metrics.
We also incorporate the Area Under the Receiver Operating Characteristic curve (AUC-ROC) as an evaluation metric. This metric comprehensively reflects the model's performance across different thresholds, making it particularly suitable for assessing classification effectiveness on imbalanced datasets. Lastly, we employ the Matthews Correlation Coefficient (MCC) as a comprehensive measure. It provides a balanced evaluation based on all elements of the confusion matrix, maintaining its effectiveness even in cases of class imbalance. The combined use of these metrics enables us to evaluate the model's performance from multiple perspectives.
We compare our proposed AI-driven RTL bug detection method against several baseline approaches, representing traditional and machine learning-based techniques. These include a rule-based static analysis tool (RSA), Support Vector Machine with hand-crafted features (SVM-HCF)[10], Random Forest with abstract syntax tree features (RF-AST), a standalone Convolutional Neural Network (CNN), and a Long Short-Term Memory network (LSTM). These baselines are implemented and optimized using the same dataset and preprocessing pipeline as our proposed method to ensure a fair comparison.
The performance of the proposed method in terms of bug detection accuracy and recall is evaluated on the test set. Our method achieves an AUC-ROC of 0.97[11], outperforming all baseline methods. The proposed method demonstrates superior performance across all bug categories, with particularly significant improvements in detecting complex bugs such as timing violations and synchronization issues.
To assess the interpretability of our model, we analyze the attention weights and feature importance scores. We conduct a user study with experienced RTL designers to evaluate the model's interpretability. The designers are presented with bug detection results and attention visualizations and asked to rate the helpfulness of the explanations. The high ratings across all aspects demonstrate the effectiveness of our model's interpretability features in assisting RTL designers with bug detection and resolution.
5. Conclusion
We collaborated with a leading semiconductor company on two complex chip design projects to validate our AI-driven RTL bug detection method: a high-performance network processor and a low-power IoT sensor hub. The network processor design comprised over 2 million lines of RTL code, while the IoT sensor hub project had approximately 500,000 lines. The AI model was integrated into the company's existing verification flow. For the network processor, the model analyzed daily code check-ins, providing rapid feedback on potential bugs. In the IoT sensor hub project, the AI model excelled at identifying corner cases related to power state transitions and clock domain crossings often overlooked by conventional methods.
The method demonstrated its ability to detect subtle bugs early in the design cycle. A notable example from the network processor project involved a complex state machine bug in the packet scheduling logic, undetected by conventional simulation due to its dependency on specific packet sequences. Integration of our AI-driven method yielded significant efficiency improvements and cost savings. For the network processor project, an estimated 3,200 engineer hours were saved, with a 22% reduction in compute resources and a six-week improvement in time-to-market, resulting in $1.2 million savings. The IoT sensor hub project saw 1,800 engineer hours saved, a 30% reduction in compute resources, and a four-week improvement in time-to-market, saving $680,000. The improved time-to-market provided a competitive advantage, particularly crucial for the IoT sensor hub project. The company reported an estimated 15% increase in market share for this product line due to earlier launch.
This approach complemented traditional verification methods, reducing design iterations and improving product quality. The visualization tools developed for interpretable AI gained trust among RTL designers, facilitating a more collaborative workflow between AI systems and human experts.
References
[1]. Sankaranarayanan, R., Srinivasan, A., Zaliznyak, A., & Mittai, S. (2021). Chip package co-design and physical verification for heterogeneous integration. In 2021 22nd International Symposium on Quality Electronic Design (ISQED) (pp. 275–280). IEEE.
[2]. Iša, R., Benáček, P., & Puš, V. (2018). Verification of generated RTL from P4 source code. In 2018 IEEE 26th International Conference on Network Protocols (ICNP) (pp. 444-450). IEEE.
[3]. Khoo, K. Y. (2006). Formal verifications in modern chip designs. In 2006 IEEE International High-Level Design and Test Workshop (pp. 38–42). IEEE.
[4]. Sankaranarayanan, R., Srinivasan, A., Zaliznyak, A., & Mittai, S. (2021). Chip package co-design and physical verification for heterogeneous integration. In 2021 22nd International Symposium on Quality Electronic Design (ISQED) (pp. 275–280). IEEE.
[5]. R. Iša, P. Benáček, & V. Puš. (2018). Verification of generated RTL from P4 source code. In 2018 IEEE 26th International Conference on Network Protocols (ICNP) (pp. 444-450). IEEE.
[6]. Li, H., Wang, S. X., Shang, F., Niu, K., & Song, R. (2024). Applications of Large Language Models in Cloud Computing: An Empirical Study Using Real-world Data. International Journal of Innovative Research in Computer Science & Technology, 12(4), 59-69.
[7]. Ping, G., Wang, S. X., Zhao, F., Wang, Z., & Zhang, X. (2024). Blockchain-Based Reverse Logistics Data Tracking: An Innovative Approach to Enhance E-Waste Recycling Efficiency.
[8]. Zhan, X., Shi, C., Li, L., Xu, K., & Zheng, H. (2024). Aspect category sentiment analysis based on multiple attention mechanisms and pre-trained models. Applied and Computational Engineering, pp. 71, 21–26.
[9]. Liu, B., Zhao, X., Hu, H., Lin, Q., & Huang, J. (2023). Detection of Esophageal Cancer Lesions Based on CBAM Faster R-CNN. Journal of Theory and Practice of Engineering Science, 3(12), 36–42.
[10]. Liu, B., Yu, L., Che, C., Lin, Q., Hu, H., & Zhao, X. (2024). Integration and performance analysis of artificial intelligence and computer vision based on deep learning algorithms. Applied and Computational Engineering, pp. 64, 36–41.
[11]. Liu, B. (2023). Based on intelligent advertising recommendations and abnormal advertising monitoring systems in machine learning. International Journal of Computer Science and Information Technology, 1(1), 17–23.
Cite this article
Wang,S.;Zheng,H.;Wen,X.;Xu,K.;Tan,H. (2024). Enhancing chip design verification through AI-powered bug detection in RTL code. Applied and Computational Engineering,92,27-33.
Data availability
The datasets used and/or analyzed during the current study will be available from the authors upon reasonable request.
Disclaimer/Publisher's Note
The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of EWA Publishing and/or the editor(s). EWA Publishing and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content.
About volume
Volume title: Proceedings of the 6th International Conference on Computing and Data Science
© 2024 by the author(s). Licensee EWA Publishing, Oxford, UK. This article is an open access article distributed under the terms and
conditions of the Creative Commons Attribution (CC BY) license. Authors who
publish this series agree to the following terms:
1. Authors retain copyright and grant the series right of first publication with the work simultaneously licensed under a Creative Commons
Attribution License that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this
series.
2. Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the series's published
version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial
publication in this series.
3. Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and
during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work (See
Open access policy for details).
References
[1]. Sankaranarayanan, R., Srinivasan, A., Zaliznyak, A., & Mittai, S. (2021). Chip package co-design and physical verification for heterogeneous integration. In 2021 22nd International Symposium on Quality Electronic Design (ISQED) (pp. 275–280). IEEE.
[2]. Iša, R., Benáček, P., & Puš, V. (2018). Verification of generated RTL from P4 source code. In 2018 IEEE 26th International Conference on Network Protocols (ICNP) (pp. 444-450). IEEE.
[3]. Khoo, K. Y. (2006). Formal verifications in modern chip designs. In 2006 IEEE International High-Level Design and Test Workshop (pp. 38–42). IEEE.
[4]. Sankaranarayanan, R., Srinivasan, A., Zaliznyak, A., & Mittai, S. (2021). Chip package co-design and physical verification for heterogeneous integration. In 2021 22nd International Symposium on Quality Electronic Design (ISQED) (pp. 275–280). IEEE.
[5]. R. Iša, P. Benáček, & V. Puš. (2018). Verification of generated RTL from P4 source code. In 2018 IEEE 26th International Conference on Network Protocols (ICNP) (pp. 444-450). IEEE.
[6]. Li, H., Wang, S. X., Shang, F., Niu, K., & Song, R. (2024). Applications of Large Language Models in Cloud Computing: An Empirical Study Using Real-world Data. International Journal of Innovative Research in Computer Science & Technology, 12(4), 59-69.
[7]. Ping, G., Wang, S. X., Zhao, F., Wang, Z., & Zhang, X. (2024). Blockchain-Based Reverse Logistics Data Tracking: An Innovative Approach to Enhance E-Waste Recycling Efficiency.
[8]. Zhan, X., Shi, C., Li, L., Xu, K., & Zheng, H. (2024). Aspect category sentiment analysis based on multiple attention mechanisms and pre-trained models. Applied and Computational Engineering, pp. 71, 21–26.
[9]. Liu, B., Zhao, X., Hu, H., Lin, Q., & Huang, J. (2023). Detection of Esophageal Cancer Lesions Based on CBAM Faster R-CNN. Journal of Theory and Practice of Engineering Science, 3(12), 36–42.
[10]. Liu, B., Yu, L., Che, C., Lin, Q., Hu, H., & Zhao, X. (2024). Integration and performance analysis of artificial intelligence and computer vision based on deep learning algorithms. Applied and Computational Engineering, pp. 64, 36–41.
[11]. Liu, B. (2023). Based on intelligent advertising recommendations and abnormal advertising monitoring systems in machine learning. International Journal of Computer Science and Information Technology, 1(1), 17–23.









