1. Introduction
1.1. Metaverse
Metaverse is a virtual world built by human beings using digital technology, mapped to or beyond the real world and can interact with the real world, and has a digital living space with a new social system. The word "Metaverse" is more of a commercial symbol, with no new technology in itself, but a large number of existing technologies [1].
The metaverse is a master of many evolving technologies, and different technologies play different roles. Zuckerberg described the metaverse: "The metaverse is an immersive Internet, and you're not just using or looking at it, but being in it."And display technology, in the universe will change the method of human information input and output," immersive " real-time feeling, and get rid of the bondage of space, which can be achieved by VR, AR, MR, holographic projection technology, VR/AR equipment has been widely known as human docking yuan universe entrance terminal, and VR/AR equipment immersion from higher resolution and refresh rate, Micro LED and Micro OLED display technology recently.
In addition, the display technology will be upgraded to interactive technology. The augmented reality and LCD screen will blend the virtual and the real. Under the current technical level, it has no less broad application scenarios than VR/AR equipment [2]. In addition, through brain-computer interaction, sensing technology, and other deepening sensing interaction technology, the display technology will complete the real-time transformation of virtual and reality, which can provide users with more real and effective body sensing and bring a deeper immersive experience.
The construction of the universe has just begun, as an emerging field for the future has big uncertainty, also need the patience to wait for mature technology and ecology, light industry is the bottom of the universe construction support, from the hardware support for fusion software, art, creative content technology connectivity, can meet the sports, film, and television, travel scenarios, digital, intelligent, scene, interconnection, build new ecological light industry, power yuan universe industrialization.
1.2. Digital Cash
When it comes to digital currencies, the first thing that people usually think of is Bitcoin, probably because bitcoin is the first digital currency to be issued. The emergence of digital currency was born under the expectation of human beings pursuing a more perfect social and economic transaction mode and global trade convenience. It was discovered in the process of using technology together and gradually exploring this need. The origin of digital currency dates back to the 1990s, and electronic gold is one of the best forms. Electronic gold was introduced in 1999, which is based on real precious metals.
Later, Satoshi Nakamoto published a paper called "Bitcoin: A peer-to-peer Electronic Cash System" on the cryptography forum [3]. Compared with fiat coins, Bitcoin does not have a centralized discovery party, but is generated by the calculation of the network nodes, which is a string of computer-generated complex code. Anyone can mine, buy, sell Bitcoins, and are anonymous and not tampered with. It was then surrounded by a mass of technical geeks, completely liberal suitors and speculators.
Digital currency can be divided into open mining cryptocurrency and issued cryptocurrency. It is defined as an Internet-based currency, or a medium of exchange, that is different from a physical currency. Digital currency can realize the instantaneous nature of the transaction and the transfer of ownership without borders.
1.3. Blockchain Platform
As the variety of digital currencies increases, platforms carrying digital currencies emerge, often referred to as blockchain platforms [4]. Among the blockchain platform, Token Pocket has the largest number of users, with more than 20 million global users, and more than 3.5 million monthly active users, distributed in more than 200 countries and regions. However, the good times did not last long, as Token Pocket increasingly popular, attracted criminals to its pool [5].
2. The Risks and Vulnerabilities of The Blockchain Platform
2.1. Hacking Attacks
On October 7,2022, Beijing time, the BNB Chain cross-chain bridge "token Center" (Token Hub) was hacked, involving a huge amount of money, and about the cross-chain between multiple chains, the estimated stolen assets of 800 million US dollars. The reason is that a vulnerability in the token center causes an additional BNB. At 0:55 on October 7, the hacker registered as Relayer with 10 0 B N B on the block height of 21955968. Starting at around 2:30 a. m., hackers received 2 million BNB units from BNB Chain's token Center (TokenHub) contracts twice (2:26,4:43). And pledged 900,000 BNB on the loan agreement Venus on BNB Chain, lending 62.5 million BUSD, 50 million USDT and 35 million USDC [6].
The Binance Cross-Chain Bridge BSC Token Hub uses a special precompiled contract to verify the IAVL tree when conducting cross-chain transaction validation. There is a vulnerability in this implementation that could allow an attacker to fake arbitrary messages. The attacker first selects a hash value of a submitted block (specified block: 110217401). An attack load is then constructed to serve as the leaf node on the validation IAVL tree. Add an arbitrary new leaf node to the IAVL tree. Also, a blank internal node is added to fulfill the implementation proof. Adjust the leaf nodes added in the above, so that the calculated root hash is equal to the correct root hash of the submission success selected in step 1. The withdrawal certificate for this particular block (110217401) is finally constructed.
Fortunately, the Chengdu chain security security team through the chain must chase, on October 16 of the same year, the hacker was successfully locked down tracking, forced to return $67 million to DAO. The developer is responsible for and studies an algorithm to determine the refund amount for the relevant account. And voted for 72 hours on the procedure and the amount.
As the Blockchain has passed a long period of development time, both the Blockchain projects themselves and the Blockchain security companies pay more attention to security than before, but the cross-chain bridge is complex code and contains the lower parts of the chain projects are very vulnerable to attack. Cross-chain bridge is usually some big projects, more amount of code, the combination of multiple links is easy to appear some combination of vulnerabilities, but these vulnerabilities are relatively hidden, easy to be used by hackers. There is another high risk point of cross-chain bridge, which is under-chain security. Because the code under the chain code is generally audited separately from the on-chain code, and usually guaranteed by the project party to ensure security, many vulnerabilities are ignored.
In the past, cross-chain bridge attacks are many attacks through offline vulnerabilities or private key leakage. This attack constructs a specific root hash to construct a specific block of the withdrawal certificate, so that the attack is relatively difficult, and the amount is higher than in the past. This incident also reminds us that the loopholes are often in some places that people can not think of, so people can only constantly improve the project security, and find these problems earlier than those with ulterior motives, so as to better maintain the ecological security of the Blockchain.
2.2. Kepler Machine Gun Pool AI
Although the hacking attack incident has been solved to a certain extent, but most customers and third-party platforms have still suffered serious losses, and quit the BSC chain to look for another carrier. During the suspension of Kepler 101 community service, Kepler machine gun pool AI was unable to conduct on-chain data analysis and implement effective real-time investment and withdrawal, which caused huge losses to the investment strategy of Kepler machine gun pool [7]. Until today, Binance chain still has potential security vulnerabilities, and there is the risk of downtime again. Binance chain is not in line with the concept of Kepler machine gun pool user asset safety first. Adhering to the responsible attitude to the safety of user assets, Kepler decided to exit the Binance (BSC) chain. And the ETH redeploys the machine gun pool contract in a short time. At that time, the Kepler machine gun pool will meet under the new name, a new investment method with the majority of community users, and announced in the community group announcement on the official release day. The USDT digital assets of all investors during the suspension period will be issued with equivalent KEP tokens.
3. The Development of FSV
The "hacking incident" is the largest and most difficult disaster ever for a digital platform. However, under such a blow, there is a cryptocurrency is not affected-FSV.
FSV (File System Video) is a Blockchain-based decentralized video file system for data transfer based on the GOSSIP protocol. FSV aims to provide a decentralized Blockchain video release environment for video generators, use NFT technology to cast streaming media copyright, govern through DPOS mechanism, and create a new economic ecology in the field of streaming media industry [8].
FSV provides decentralized copyright registration, trading platform, according to the registration time stamp fixed copyright holder, and generate the NFT block chain copyright certificate, through the decentralized DPOS mechanism for self-governance, solve the various problems existing in the field of global streaming media copyright, prompting the interests of each link in the field of streaming media industry to fully safeguard.
A new generation of native Blockchains was created for decentralized video transmission technology. Multi-layer BFT as a consensus mechanism, aggregation signature Gossip protocol (Aggregated Signature Gossip Scheme) resource-oriented micropayment pool, and other innovative technologies. IPFS uses the same distributed storage technology, mainly has the semantic network, strong distribution, and micro-storage three characteristics. A single video file is divided into several 256KB slices, stored with multiple fragments and multiple nodes, and sorted from the nearest node according to the distance to obtain the desired slices.
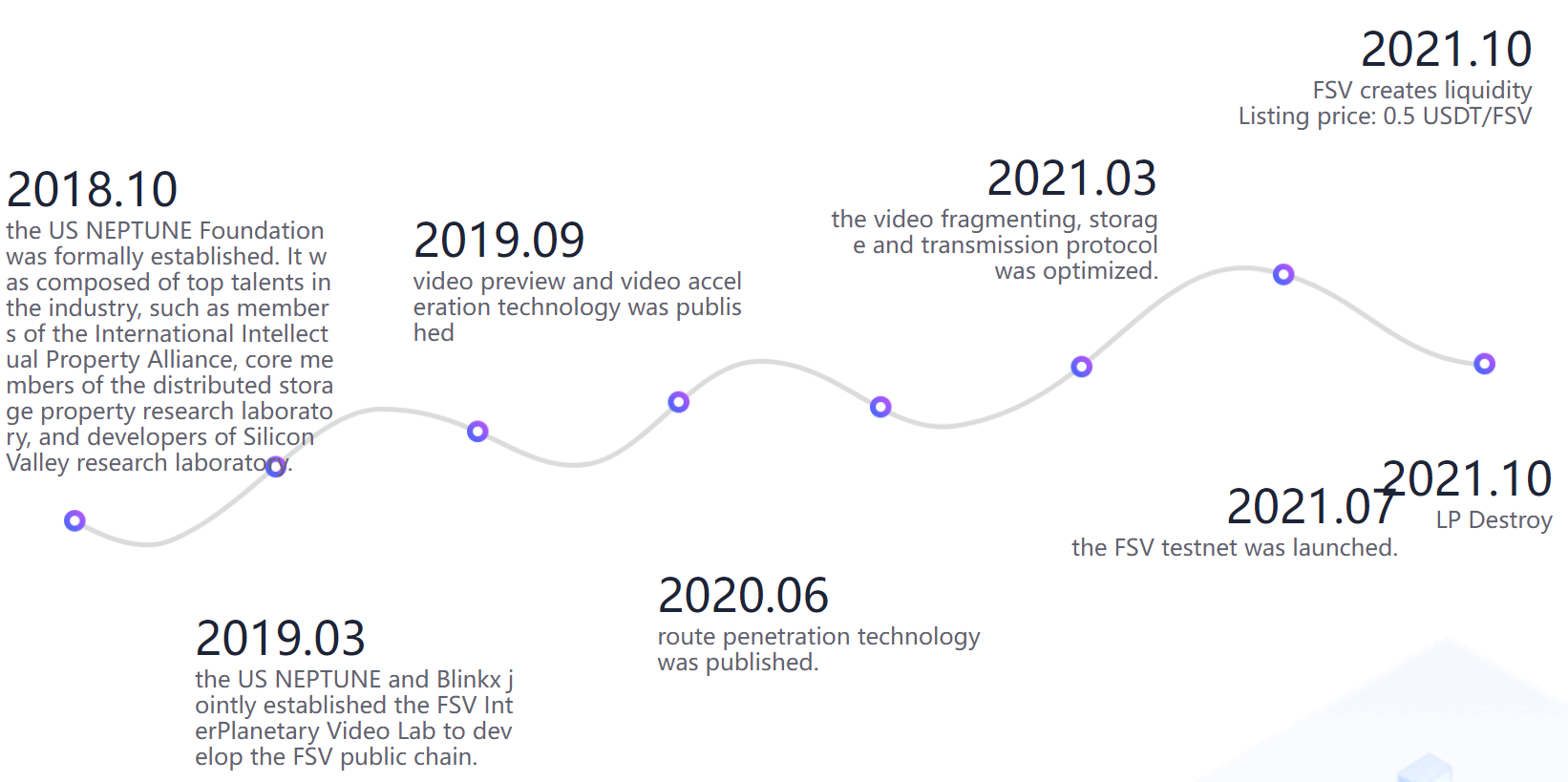
Figure 1. The developmental trajectory of the FSV.
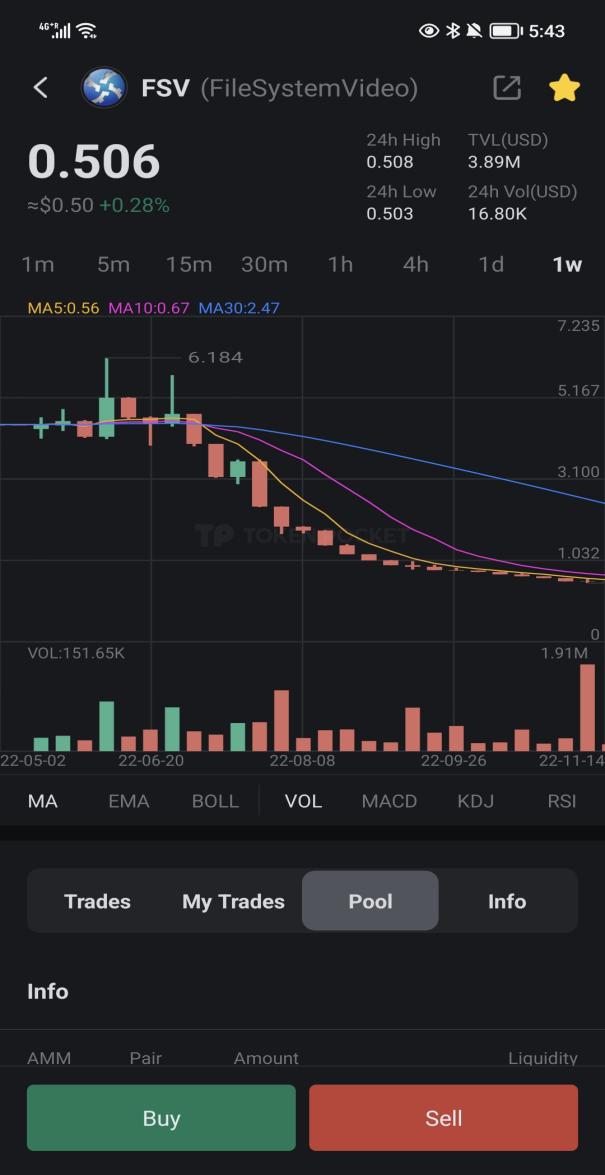
Figure 2. Price changes in the FSV.
4. Classification and Identification of Digital Currency
In addition to the risk of being hacked to steal assets, digital currency platforms also face their own profits and losses. The cryptocurrency market is a mixed area, with a lot of stable currencies with high consensus like Bitcoin, there is a lot of money. Identifying currencies of potential value is therefore necessary.
If the digital currency is graded, it can be roughly divided into three levels. The first is that its value and consensus have been strongly recognized, almost undisputed, and have been transmitted from the circle to the circle. Bitcoin and Taiwan dollar, for example, are the least abundant in the entire digital currency sector. The second category is that the consensus is already there, but the actual use value is still in the proof, or the so-called "use value" can not yet see the actual effect. Such as Ethereum, EOS, cross-chain, etc. These are slightly more coins than in the first category, but also very few in the entire digital currency space. The third category is that the consensus has not yet been formed. The design goals and scenes of such coins are not even understood or recognized by the industry, even if the understanding is very different. Their value is even more difficult to judge. These coins account for the vast majority of the current market [9].
These three types of digital currencies are not only different in value perception, but also contain different risks and difficulty to control these risks. The risks of the first type of digital currency are the easiest to judge, and it is easy for investors to judge risks and take measures against them according to changes in various factors. The risk of bitcoin is basically the smallest among all digital currencies, and there are only two risks of making bitcoin zero: global governments ban bitcoin transactions, and the second is that Internet is completely paralyzed, otherwise there is little possibility of bitcoin going to zero. If the bitcoin coin goes to zero, none of the other digital currencies would be safe [10]. The risk of the platform currency is basically only related to the government's regulatory policies and the operation of the platform. As long as the regulatory policies are loose and the platform operation is stable, the risk of the platform currency, especially the platform currency of the big exchanges, is very small.
Since the value of the second type of digital currency is still in the process of realization, whether its value can finally be realized and meet expectations is affected by many factors. Therefore, the risks of such digital currencies are much riskier than the first type of digital currencies, and it is much more difficult to control the risks. Take Ethereum and EOS, for example, which are both public chains that support smart contracts, and they are also the two biggest competitors in the field. Whether the final outcome of the two competitors will win, the other will gradually zero, or both will coexist forever. But one thing is clear, there will be at least one platform alive in this area because the application of smart contracts is just necessary for the application of Blockchain technology.
The third type of digital currency is the most complex, and therefore the riskiest. Some are former star projects that were gradually eliminated from the competition, some were once favored but proved to be fake in practice; some are just emerging in a niche, which is meaningful and potentially valuable. This field even includes some air coins and pyramid-selling coins that have temporarily confused a considerable number of investors.
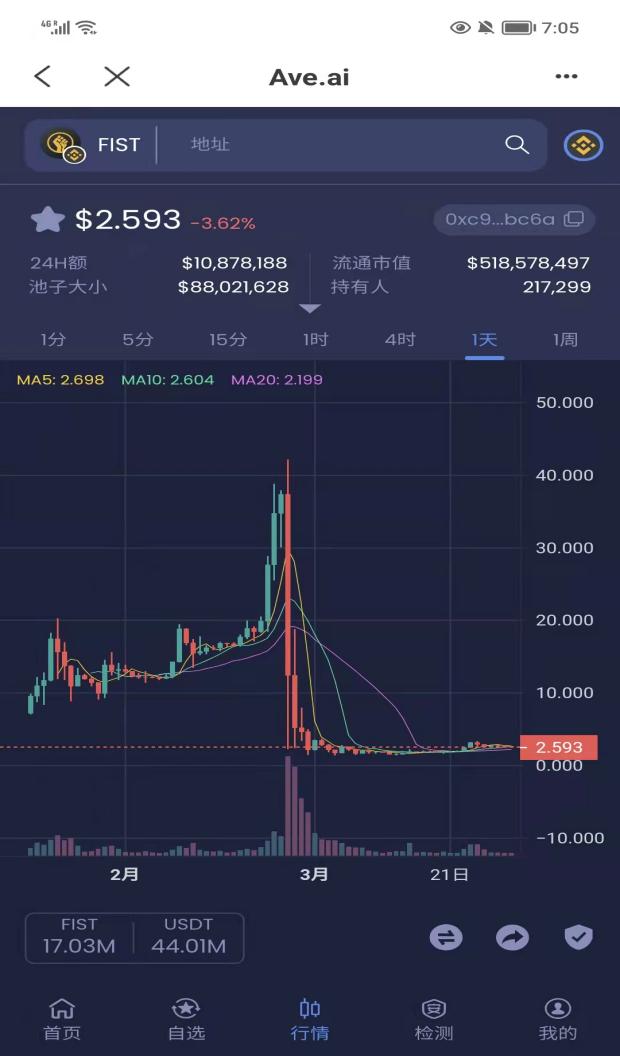
Figure 3. A very risky digital currency.
5. Conclusion
Disaster is a good touchstone in the Blockchain world, screening out cryptocurrencies with a stable collection of value, such as FSV. As the risks contained in these three types of digital currencies are different, different investors also have different cognition and control of these risk factors. Next time, they will share how to handle the investment of these three types of digital currencies according to their own risk tolerance. As the metaverse era advances, the surviving currencies will be recognized by more and more people, and under the environmental consensus, they will eventually grow into an existence that can be equally exchanged like Bitcoin.
References
[1]. What Is the Metaverse, Exactly? [EB/OL]. (2022) [12/11/2022]. https://www.wired.com/story/what-is-the-metaverse/
[2]. What’s the Difference between AR, VR, and MR? (2022) [13/11/2022]. https://www.fi.edu/difference-between-ar-vr-and-mr
[3]. Digital Cash: Advantages and Disadvantages. (2022) [14/11/2022]. https://managementstudyguide.com/digital-cash-advantages-and-disadvantages.htm
[4]. Blockchain overview. (2022) [15/11/2022]. https://www.ibm.com/topics/what-is-blockchain
[5]. Token Pocket is trusted by global users. (2022) [15/11/2022]. https://www.tokenpocket.pro/en
[6]. Binance loses cryptocurrency worth $570m in cyberattack on coin bridge. (2022) [16/11/2022]. https://techmonitor.ai/technology/binance-cyberattack-cryptocurrency-coin-bridge
[7]. Kepler AI Business Platform. (2022) [17/11/2022]. https://www.appliedai.com/product/kepler-ai-business-platform
[8]. FileSystemVideo FSV (2022) [17/11/2022]. https://coinpaprika.com/coin/fsv-filesystemvideo/#:~:text=FileSystemVideo%20%5BFSV%5D%20is%20a%20token%20based%20on%20Binance,exchanges%20with%20a%20sum%20of%201%20active%20markets.
[9]. What is Digital Currency? (2022) [18/11/2022]. https://www.plus500.com/en-AU/Trading/Forex?
[10]. What is virtual currency? (2022) [18/11/2022]. https://study.com/academy/lesson/digital-virtual-currencies-definition-types-forms.html
Cite this article
Tian,H. (2023). Digital Platforms with the Ups and Downs in the Metaverse Era. Advances in Economics, Management and Political Sciences,6,1-7.
Data availability
The datasets used and/or analyzed during the current study will be available from the authors upon reasonable request.
Disclaimer/Publisher's Note
The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of EWA Publishing and/or the editor(s). EWA Publishing and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content.
About volume
Volume title: Proceedings of the 2022 International Conference on Financial Technology and Business Analysis (ICFTBA 2022), Part 2
© 2024 by the author(s). Licensee EWA Publishing, Oxford, UK. This article is an open access article distributed under the terms and
conditions of the Creative Commons Attribution (CC BY) license. Authors who
publish this series agree to the following terms:
1. Authors retain copyright and grant the series right of first publication with the work simultaneously licensed under a Creative Commons
Attribution License that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this
series.
2. Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the series's published
version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial
publication in this series.
3. Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and
during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work (See
Open access policy for details).
References
[1]. What Is the Metaverse, Exactly? [EB/OL]. (2022) [12/11/2022]. https://www.wired.com/story/what-is-the-metaverse/
[2]. What’s the Difference between AR, VR, and MR? (2022) [13/11/2022]. https://www.fi.edu/difference-between-ar-vr-and-mr
[3]. Digital Cash: Advantages and Disadvantages. (2022) [14/11/2022]. https://managementstudyguide.com/digital-cash-advantages-and-disadvantages.htm
[4]. Blockchain overview. (2022) [15/11/2022]. https://www.ibm.com/topics/what-is-blockchain
[5]. Token Pocket is trusted by global users. (2022) [15/11/2022]. https://www.tokenpocket.pro/en
[6]. Binance loses cryptocurrency worth $570m in cyberattack on coin bridge. (2022) [16/11/2022]. https://techmonitor.ai/technology/binance-cyberattack-cryptocurrency-coin-bridge
[7]. Kepler AI Business Platform. (2022) [17/11/2022]. https://www.appliedai.com/product/kepler-ai-business-platform
[8]. FileSystemVideo FSV (2022) [17/11/2022]. https://coinpaprika.com/coin/fsv-filesystemvideo/#:~:text=FileSystemVideo%20%5BFSV%5D%20is%20a%20token%20based%20on%20Binance,exchanges%20with%20a%20sum%20of%201%20active%20markets.
[9]. What is Digital Currency? (2022) [18/11/2022]. https://www.plus500.com/en-AU/Trading/Forex?
[10]. What is virtual currency? (2022) [18/11/2022]. https://study.com/academy/lesson/digital-virtual-currencies-definition-types-forms.html









