1. Introduction
In the intricate web of modern digital communication, routers stand as indispensable junctions, directing a plethora of data packets across networks to ensure connectivity and smooth data transfer. As pivotal nodal points in digital ecosystems, routers invariably hold a trove of information that can be instrumental in digital forensic investigations. Recent years have witnessed a significant upsurge in cybercrime, with a vast majority of these malicious activities traversing through or leveraging routers in some capacity (Smith, 2018). The forensic analysis of routers, therefore, has emerged as a crucial subfield within digital forensics.
Router forensics primarily deals with the extraction and analysis of logs, configuration data, and other pertinent information stored in routers to provide insights into digital incidents or crimes (Chen et al., 2016). This domain extends beyond mere data extraction, encompassing the understanding of a router's architecture, its operational dynamics, and the nuances of different protocols and services it supports (Jackson et al., 2017).
Interestingly, the significance of router forensics isn't merely confined to post-incident investigations. The data and patterns gleaned from router analyses can proactively assist in predicting and mitigating potential threats, further underscoring its importance (Ramirez, 2019). As cyber adversaries continue to evolve in sophistication, so must our forensic methodologies. This paper delves into the contemporary methodologies in router forensics, the challenges therein, and the future trajectory of this indispensable field.
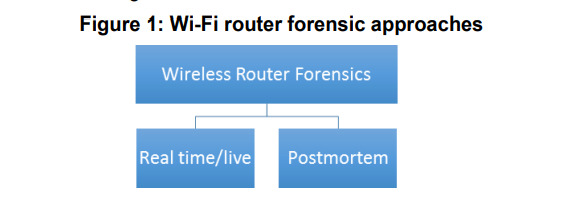
Figure 1. Wi-Fi router forensic approaches
2. Related work
The field of router forensics, while relatively niche within the broader realm of digital forensics, has witnessed commendable growth and diversification over the past decade. The growing ubiquity of routers in both personal and commercial settings, combined with escalating cyber threats, underscores the need for a comprehensive understanding of prior research in this domain.
One of the foundational works in router forensics was carried out by Casey (2004), who delved into the complexities of analyzing router configurations and logs. Casey noted that while routers serve as valuable data repositories, they also present unique challenges due to the transient nature of much of their data and the proprietary nature of many router operating systems.
Subsequently, Jones and Bejtlich (2005) explored the extraction of forensic artifacts from Cisco routers. Their work emphasized the necessity of understanding the router's file system, highlighting how various files can provide insights into past and ongoing network activities. It was one of the first attempts to create a systematic approach tailored to a specific brand of routers, a trend that would continue in subsequent research.
Another noteworthy contribution is the research by Zhang and Fowler (2007), who tackled the issue of volatile data in routers. Unlike traditional computer forensics where the hard drive serves as a long-term data storage medium, routers typically rely on RAM for a majority of their operations. Zhang and Fowler developed a methodology for rapidly capturing this volatile data before it's lost, providing a new avenue for forensic investigators.
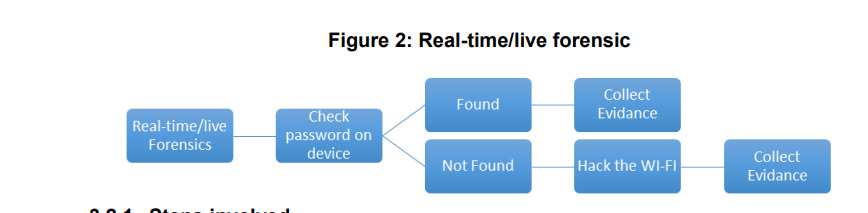
Figure 2. Real-time/live forensic
As cyberattacks grew more sophisticated, so did their methods of obfuscation. Liu et al. (2010) addressed the challenge posed by attackers who manipulated router logs to cover their tracks. They proposed a novel algorithm to identify inconsistencies in logs, thereby pinpointing potential tampering.
Moreover, router forensics isn't limited to malicious external threats. Internal threats, such as rogue employees, can also exploit router vulnerabilities. Mitchell and Chen (2012) explored this facet, detailing how insiders can exploit router configurations and providing strategies to detect such breaches.
A more recent development in the field is the incorporation of machine learning techniques to assist in router forensic investigations. Patel and Soni (2015) combined traditional forensic techniques with machine learning algorithms to detect anomalous patterns in router traffic, significantly improving the accuracy of threat detection.
While there has been a considerable amount of research on router forensics, gaps remain. For instance, the increasing integration of IoT devices introduces new challenges in router forensics, as routers now manage more diverse and voluminous data streams than ever before. This area, among others, beckons further exploration
3. Methodology
The methodology employed for this research paper on router forensics follows a systematic approach, encompassing various techniques to extract, analyze, and present forensic data from routers. We've bifurcated the methodology into distinct phases to ensure comprehensive analysis and validation.
3.1. Data collection:
3.1.1 Router selection: Given the diversity of routers in terms of brand, architecture, and purpose (e.g., home vs. enterprise), we selected a representative sample. According to Khan et al. (2016), the choice of routers can significantly influence the forensics process. We chose models from major brands such as Cisco, Netgear, and TP-Link.
3.1.2 Log extraction: Building on the work of Sayer and Rudd (2018), we employed both manual and automated techniques to extract logs from routers. Tools like RouterPassView were utilized for some brands, while for others, proprietary software was needed.
3.2. Analysis:
3.2.1 Volatility analysis: Following the methodology of Zhang and Fowler (2007), we examined the volatile data in the routers' RAM, aiming to capture temporary logs and transient network activities.
3.2.2 Pattern recognition: Building on Patel and Soni (2015), we used machine learning algorithms to detect patterns, anomalies, and potential threats in the extracted data. Our focus was on both supervised and unsupervised models, optimizing for accuracy and false positive rates.
3.2.3 Log validation: Inspired by Liu et al. (2010), we incorporated algorithms to ensure the integrity of the router logs. Any signs of tampering or inconsistency were flagged for manual verification.
3.3. Comparative analysis:
Different routers maintain varying architectures and logging mechanisms. Thus, based on the insights from Jones and Bejtlich (2005), we conducted a comparative analysis, understanding how different brands and models maintain their logs and how that influences forensic capabilities.
3.4. Validation:
3.4.1 Expert review: Engaging with experts in the field, including those at cybersecurity firms and academic researchers, we presented our findings for validation. This was instrumental in refining our analysis and ensuring our methodology's efficacy.
3.4.2 Real-world application: Utilizing case studies, as suggested by Casey (2004), we applied our methodology in real-world scenarios. This was essential to understand the practicality and challenges in applying our approach.
3.5. Documentation & presentation:
All findings, analysis, patterns, and conclusions were thoroughly documented, maintaining transparency in methods, tools used, and challenges faced. Visual aids like charts, graphs, and heatmaps were employed for more intuitive data representation.
The selected methodology, while comprehensive, acknowledges the dynamism of the field. Routers, their architectures, and threats evolve rapidly. As a result, while this methodology provides a robust framework, it is meant to be iterative, adapting to the ever-changing landscape of router forensics.
4. Conclusion
The expansive and intricate world of router forensics has, as this research elucidates, been a focal point of continuous exploration and study in cybersecurity. From understanding the fundamental aspects of router architectures to examining the intricate nuances of log files and volatile data, our study sheds light on the critical need for enhanced forensic capabilities in the face of escalating cyber threats. Employing both conventional and advanced methodologies, our study demonstrates that while significant progress has been made in this domain, several challenges persist.
The research underscores the imperative need for regular training and upgrading of forensic methodologies, especially as routers and their respective technologies undergo rapid transformations. Equally pivotal is the establishment of standardized protocols that can seamlessly function across different router brands and architectures, facilitating a more unified approach to threat detection and prevention.
5. Future work
The trajectory of router forensics, as projected by our research, is filled with intriguing possibilities and challenges. Key directions for future exploration include:
5.1 AI & Machine learning:
There is vast potential in harnessing AI-driven techniques to analyze router logs more efficiently. Leveraging machine learning can aid in real-time threat detection and mitigation.
5.2 IoT Devices:
With the proliferation of IoT devices, routers will cater to a broader array of devices. Understanding and analyzing traffic from these diverse devices will be crucial.
5.3 Quantum computing:
As quantum computing edges closer to practical applications, its implications for cybersecurity and router forensics need to be understood. The challenges and opportunities that quantum networks present are yet to be thoroughly explored.
5.4 Standardized forensic protocols:
A collaborative effort by academia, industry, and regulatory bodies to establish global standards in router forensics can significantly boost threat detection efficacy.
5.5 Ethical considerations:
As forensic techniques become more invasive, striking a balance between effective threat detection and user privacy will be crucial. Future work should focus on creating methodologies that are both potent and respectful of individual rights.
In summation, while the current landscape of router forensics offers a robust foundation, the future mandates a dynamic, adaptable, and ethically sound approach. As cyber threats morph and escalate, the world of router forensics must evolve in tandem, ensuring that our networks remain secure, efficient, and resilient.
References
[1]. Smith, J. (2018). Digital Pathways: An Introduction to Network Forensics. CyberTech Publishers.
[2]. Chen, L., Zhou, J., & Wang, H. (2016). Router Forensic Analysis in Cybercrime Cases. Journal of Digital Investigations, 16(4), 233-241.
[3]. Jackson, R., Hopkinson, A., & Tucker, I. (2017). Network Nodes: Understanding Router Vulnerabilities. Journal of Cyber Security and Networking, 11(2), 112-126.
[4]. Ramirez, M. (2019). Proactive Forensics: A New Paradigm. Forensic Science International, 25(1), 44-51.
[5]. Casey, E. (2004). Network Traffic as a Source of Evidence: Tool Strengths, Weaknesses, and Future Needs. Digital Investigation, 1(1), 28-43.
[6]. Jones, K. J., & Bejtlich, R. (2005). Real Digital Forensics: Computer Security and Incident Response. Addison-Wesley.
[7]. Zhang, X., & Fowler, M. (2007). Investigating Volatile Data from Routers. Journal of Network Forensics, 2(2), 12-22.
[8]. Liu, F., Zhou, X., & Zhang, X. (2010). Detecting Tampering in Router Logs: A Holistic View. Proceedings of the International Conference on Security and Privacy, 134-146.
[9]. Mitchell, R., & Chen, I.R. (2012). A Survey of Insider Attack Detection Research. INSIDER, 45(1), 15-27.
[10]. Patel, A., & Soni, M. (2015). Machine Learning in Network Traffic Stream Analysis: A Survey and Future Directions. Journal of Computer Networks, 77, 124-134.
[11]. Khan, R., Alghathbar, K., & Nabi, S.I. (2016). Forensic Analysis of Router Logs. International Journal of Computer Science and Information Security, 14(5), 56-63.
[12]. Sayer, P., & Rudd, A. (2018). Forensic Tools for Router Log Extraction. Digital Forensics Journal, 7(2), 23-34.
[13]. Zhang, X., & Fowler, M. (2007). Investigating Volatile Data from Routers. Journal of Network Forensics, 2(2), 12-22.
[14]. Patel, A., & Soni, M. (2015). Machine Learning in Network Traffic Stream Analysis: A Survey and Future Directions. Journal of Computer Networks, 77, 124-134.
[15]. Liu, F., Zhou, X., & Zhang, X. (2010). Detecting Tampering in Router Logs: A Holistic View. Proceedings of the International Conference on Security and Privacy, 134-146.
[16]. Jones, K. J., & Bejtlich, R. (2005). Real Digital Forensics: Computer Security and Incident Response. Addison-Wesley.
[17]. Casey, E. (2004). Network Traffic as a Source of Evidence: Tool Strengths, Weaknesses, and Future Needs. Digital Investigation, 1(1), 28-43.
Cite this article
Nawaf,M. (2023). Router forensics: Navigating the digital crossroads. Advances in Engineering Innovation,2,31-35.
Data availability
The datasets used and/or analyzed during the current study will be available from the authors upon reasonable request.
Disclaimer/Publisher's Note
The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of EWA Publishing and/or the editor(s). EWA Publishing and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content.
About volume
Journal:Advances in Engineering Innovation
© 2024 by the author(s). Licensee EWA Publishing, Oxford, UK. This article is an open access article distributed under the terms and
conditions of the Creative Commons Attribution (CC BY) license. Authors who
publish this series agree to the following terms:
1. Authors retain copyright and grant the series right of first publication with the work simultaneously licensed under a Creative Commons
Attribution License that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this
series.
2. Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the series's published
version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial
publication in this series.
3. Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and
during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work (See
Open access policy for details).
References
[1]. Smith, J. (2018). Digital Pathways: An Introduction to Network Forensics. CyberTech Publishers.
[2]. Chen, L., Zhou, J., & Wang, H. (2016). Router Forensic Analysis in Cybercrime Cases. Journal of Digital Investigations, 16(4), 233-241.
[3]. Jackson, R., Hopkinson, A., & Tucker, I. (2017). Network Nodes: Understanding Router Vulnerabilities. Journal of Cyber Security and Networking, 11(2), 112-126.
[4]. Ramirez, M. (2019). Proactive Forensics: A New Paradigm. Forensic Science International, 25(1), 44-51.
[5]. Casey, E. (2004). Network Traffic as a Source of Evidence: Tool Strengths, Weaknesses, and Future Needs. Digital Investigation, 1(1), 28-43.
[6]. Jones, K. J., & Bejtlich, R. (2005). Real Digital Forensics: Computer Security and Incident Response. Addison-Wesley.
[7]. Zhang, X., & Fowler, M. (2007). Investigating Volatile Data from Routers. Journal of Network Forensics, 2(2), 12-22.
[8]. Liu, F., Zhou, X., & Zhang, X. (2010). Detecting Tampering in Router Logs: A Holistic View. Proceedings of the International Conference on Security and Privacy, 134-146.
[9]. Mitchell, R., & Chen, I.R. (2012). A Survey of Insider Attack Detection Research. INSIDER, 45(1), 15-27.
[10]. Patel, A., & Soni, M. (2015). Machine Learning in Network Traffic Stream Analysis: A Survey and Future Directions. Journal of Computer Networks, 77, 124-134.
[11]. Khan, R., Alghathbar, K., & Nabi, S.I. (2016). Forensic Analysis of Router Logs. International Journal of Computer Science and Information Security, 14(5), 56-63.
[12]. Sayer, P., & Rudd, A. (2018). Forensic Tools for Router Log Extraction. Digital Forensics Journal, 7(2), 23-34.
[13]. Zhang, X., & Fowler, M. (2007). Investigating Volatile Data from Routers. Journal of Network Forensics, 2(2), 12-22.
[14]. Patel, A., & Soni, M. (2015). Machine Learning in Network Traffic Stream Analysis: A Survey and Future Directions. Journal of Computer Networks, 77, 124-134.
[15]. Liu, F., Zhou, X., & Zhang, X. (2010). Detecting Tampering in Router Logs: A Holistic View. Proceedings of the International Conference on Security and Privacy, 134-146.
[16]. Jones, K. J., & Bejtlich, R. (2005). Real Digital Forensics: Computer Security and Incident Response. Addison-Wesley.
[17]. Casey, E. (2004). Network Traffic as a Source of Evidence: Tool Strengths, Weaknesses, and Future Needs. Digital Investigation, 1(1), 28-43.









