1. Introduction
Quantum computing is advancing to meet the growing demand for computational efficiency in modern science and technology. Through the usage of quantum states, the field offers breakthrough applications and insights, including quantum cryptography for ultra-secure classical information transmission, quantum error correction for preserving quantum coherence amidst noise, and quantum computation for efficient processing through controlled quantum evolution [1]. Our paper mainly focuses on quantum error correction.
In recent years, the problem of noise has emerged as a predominant obstacle in the advancement of universal quantum computers. Quantum decoherence, which refers to the preservation of quantum states despite the interference of noise,is necessary in order to keep quantum computing reliable. Nowadays, experimental efforts have been made to simulate quantum computations on small-scale devices, aiming to achieve the quantum decoherence [2]. Unfortunately, these experiments are usually complicated and challenging. Though the experiments are difficult, quantum error-correcting codes offer a promising solution, which is also the reason for the exploration in our study.
Detecting effective quantum error-correcting codes involves various methodologies to compare and select optimal approaches: methods for encoding a single qubit to correct multiple errors [3]; the use of entire classes of codes makes the codes for multiple-correction of many qubits efficient [4,5]; in [6], the author provides efficient quantum error corrections codes and discusses techniques for manipulating codes and guessing new codes.
In our paper, we introduce a novel but useful method for representing qudits through polynomials. Though previous applications are limited to simpler square lattice codes, we do extend this approach to more complex scenarios in Cayley graphs, and give an example of the situation on the Cayley graph of dihedral group
We outline topics of individual sections. Section 2 introduces basic concepts of quantum information. Section 3 introduces Groups and Graphs, especially Cayley graphs. Section 4 discusses the definitions and examples of stabilizer codes. Section 5 discusses the existing representation of stabilizer codes and our own innovations of stabilizer codes for a more complex group or in a more complicated graph. Section 6 shows an example of using our innovative method to find the stabilizer codes.
2. Quantum information
Quantum information systems improve the quantum computing through the usage of quantum mechanical phenomena to enhance computational efficiency. Moreover, we would like to highlight the fundamental characteristics of quantum information, which encompass quantum superposition and entanglement.
Property.1Quantum information is uncertain.
In classical computers, data are stored, sent, received, and processed in the string of form of bits, which is either 0 or 1. Contrary to that, quantum information systems demonstrate a significantly different situation. Initially, quantum bits, also known as qubits, are present in a superposition of multiple quantum states. Later, quantum collapse may be precipitated by observation in quantum information, resulting in a state change. This collapse is the collapse of the wave function, which represents to the mathematical representation of the quantum state of a certain quantum system. Specifically, collapse refers to the transformation of a wave function from a superposition of multiple quantum states to a single state as a result of observation. Quantum supervision theory points out that the quantum states of qubits is the state in a linear combination of state 0 and state 1 instead of either 0 or 1. Observing a qubit can change its superposition state to either 0 or 1. Hence, the qubit will transition from the state of superposition to a state of definitiveness. As an illustration, consider a qubit system consisting of 500 qubits. When doing the first observation, 300 of them might be 0. However, in the second observation, the value might change to 200. In essence,every observation and measurement will result in diverse outcomes.
Property.2Quantum information is not local.
According to the theory of quantum entanglement, the quantum state of each particle is not independently determined by itself, but rather can only be described in a global context. If there is a pair of entangled particles, measurement and observation will determine the quantum state of one of them. This allows us to infer the state of the other particle based on their global state. This indicates that in a quantum information system, every qubit’s quantum state is affected by the others. Consider, for example, a pair of qubits, consisting of 0 and 1. In a quantum information system with several qubits, the quantum state of one qubit influences the states of the other qubit, leading to a complex entangled system[7].
2.1. Basic concepts
2.1.1. Qubit
In classical computer, data is stored as strings of bits (0s or 1s), and always represented as vectors over
where
There is a basic criteria for quantum error correction about the qubits and environment. The initial state of an environment is denoted by
in which
2.2. Inner product space
An inner product space is a vector space denoted by
There are totally 4 axioms of
Axiom.1
Axiom.2
Axiom.3
Axiom.4
Every inner-product space is a normed space because if there is an inner product space
2.2.1. Qudit
In d-dimentional Hilbert space
2.3. Quantum error correction
An essential goal of quantum error correction is to minimise the harmful impact of noise on quantum information. Quantum noise refers to the elements that impact the precision of calculations performed on a quantum computer. For example, cosmic rays, radiation from mobile phones, or the magnetic field of the Earth are all the sources of quantum noise. These noises may lead to quantum error, which is the error happening in quantum algorithm, finally resulting in the error in information transferred by quantum computer. When quantum error happens, the input of a pure qudit will produce a mixed state or it will become a different pure state compared with the input one.
The codes known as Quantum Error Correcting Codes (QECC) often carry out this operation. QECC always perform 3 operations to correct the error of a quantum computing. Firstly, they encode the initial state of quantum information. Then, the diagnose errors. Finally, some recovery operations will be implemented to rectify errors.
QECC can be viewd as a mapping of
Take the situation when only one error on a single qubit at a time as an example, the first step is to encode the given logical qudit as follows:
Through the encoding process above, the data can be stored as 9 qubits.
The second process is the diagnosis of errors. Suppose the first qubit is flipped by switching
Another possible error in one qubit is sign flips, which is shown as follows :
Here we only need to compare whether the first sign is same as the second and the third one, thus find the error and flip the sign. A bit flip and a sign flip can be described as the operations as follows respectively:
2.4. Pauli matrix & pauli operator
The operations introduced in Section 2.3 belong to a group of matrices called Pauli matrix.
Pauli matrix includes 4 different matrices as follows [11]:
Any
where
A Pauli operator is formed by taking a tensor product of Pauli matrix on a set of qudits
Consider a set of orthonormal basis vectors denoted by
where
Pauli operators form a group denoted by
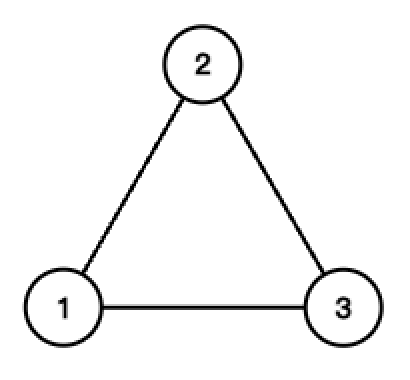
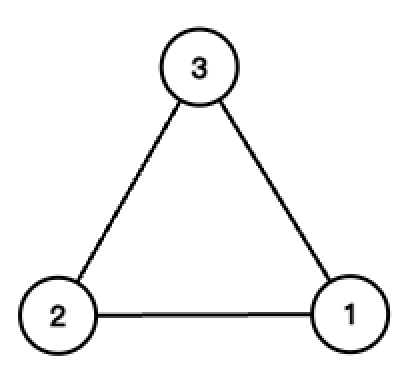
Here is an example of an equilateral triangle.
The equilateral triangle
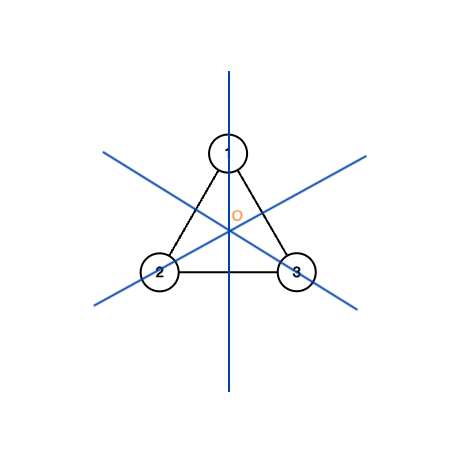
By applying the operations
|
|
3. Group and cayley graph
3.1. Definition of group
A group
Axiom.1 A group is closed under the operation.
After applying a binary operation, the third element formed by the two chosen elements should belong to the set which the two chosen elements belong to.
Axiom.2 Associativity is allowed in groups.
Associativity is allowed in groups. For example,
Axiom.3 Identity element
The identity element
Axiom.4 Inverse element
For every element in
Abelian group is also named commutative group, in which the order of two group elements does not affect the results after doing group operation, basically satisfying
3.2. Examples and counter-examples of group
Example.1 Set of all integers with operation
Example.2 Set of Pauli operators with operation
Pauli operators over a set of qudits form a group
Counter-Example.1 Set of all integers with operation
3.3. Definition of subgroups
A subgroup
Example.1
Example.2 If
3.4. Fundamental theorem of homomorphism
Given two groups
Here are some fundamental definitions of homomorphism:
Definition.1 If
Definition.2 If
Definition.3 If
Definition.4 If
Definition.5 If
Another essential concept in terms of homomorphism is
The image of
After introducing some basic definitions, we need to know one of the most important theorem involved in group, which is Group Isomorphism Theorem.
Property.1 If
Property.2 Suppose
3.5. Group representation
Group representation theory examines homomorphisms mapping a group to the group of invertible linear transformations over vector spaces. To be more specific, it studies how abstract groups can be showed in the form of matrices and how their elements relates to linear transformations of vector spaces. Through the analysis of these representations, researches can get some helpful inspirations into the structure and properties of the group [13].
3.6. Group generators & generating set
If there is an element
Here is an example,
A generating set refers to a group of elements that can be combined (including themselves, their inverses, and all possible combinations of them) to produce all the elements of an entire group. In simple terms, if a group
3.7. Definition of graph
According to the directed and undirected nature of the edges of the graph, graphs can be classified as directed graphs, undirected graphs, and mixed graphs. In directed graph, edges have directions, usually presented as an arrow.
3.8. Cayley graph
Cayley graph is a directed graph associated to
• Vertices are elements in set
• Edges are elements in set
Constructing a Cayley graph is the way of producing an unbounded sequence of
In a Cayley graph, each edge is associated with a pair
Therefore, through the generator
Here is an example of a Cayley graph in the sequence
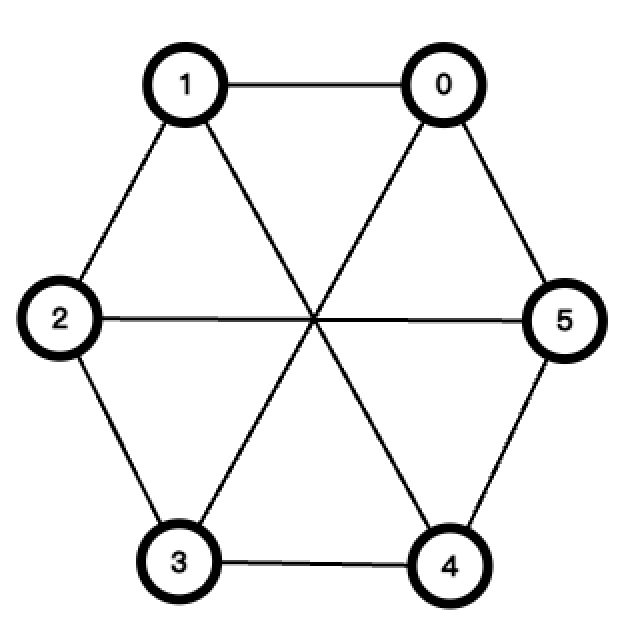
4. Stabilizer codes
In quantum information and theoretical condensed matter physics, stabilizer codes are often mentioned(defined below). They originate from quantum error correction, but are widely studied now as toy models for exotic quantum phases. The famous toric code model for anyons as well as the X-cube model for fractons both fall under this category.
4.1. Definition
Stabilizer codes refer to a collection of quantum codes utilized for performing quantum error correction. Given a set of qudits
A theorem from linear algebra stipulates that any two stabilizers
Firstly, assuming
Obviously,
Next, assuming eigenvalues of
Conversely, if
Let
Property.1 They have the order of 2. Any elements from
Property.2 They are commutative to each other.
Property.3 They are unitary and Hermitian.
Back to the quantum stabilizer codes, denoted by
4.2. An example of pauli stabilizer group
Taking a 1-qubit Pauli group as an example, the following is how the Pauli matrix generates it:
Pauli matrices have the same algebraic relationships as the four units if quaternions
Another example is called Shor’s 9-qubit code, which encodes 1 logical qubit,
The stabilizer codes are :
Notice that the stabilizers pairwise commute [15].
5. Representation of stabilizer codes
One amazing observation is that Pauli stabilizer codes with certain “translation symmetry” can be studied using modules over certain group algebra. This section first illustrates how this is done in the case of regular
5.1. Qudits on square lattice
Assign
Proposition 1.
Proof. Denote the standard basis of
We often use elements in
The definitions that follow are influenced by symplectic vector spaces. Let
For some positive integer
with
where
In fact given
5.2. Qudits on cayley graph
Let
On each vertex of
Action of
5.3. Connection to group representation
Consider
with
is still well-defined on
6. Translation-invariant stabilizer code on a cayley graph
6.1. Generalized polynomial method for searching new stabilizer codes
The method mentioned in Secion 5 can be applied to any Cayley graph. Given any Cayley graph, we can represent stabilizer codes using our methods. In detail, we firstly represent the vertices in a Cayley graph by a group ring. One chosen Pauli operator will be the stabilizers of the graph. By using the formula for commutativity, we can find another stabilizer that commutes with the chosen one. Through this way, we can have various chosen stabilizers. Also by continuing using the same way to calculate more stabilizers, we can combine them to form stabilizer codes.
In general, there are some steps we can follow to find a new stabilizer code:
1. Start by choosing a Pauli operator as stabilizer.
2. We solve commuting equations and select a new stabilizer.
3. Repeat step 2 till satisfy any pre-set condition (set before the calculation).
4. The commuting equation will get too restrictive and it is not worth to calculate that, so we can stop our calculations.
5. We can amalgamate the stabilizers to create stabilizer codes.
6.2. An example of finding stabilizer codes on a cayley graph
We will give an example of the Cayley graph of a dihedral group
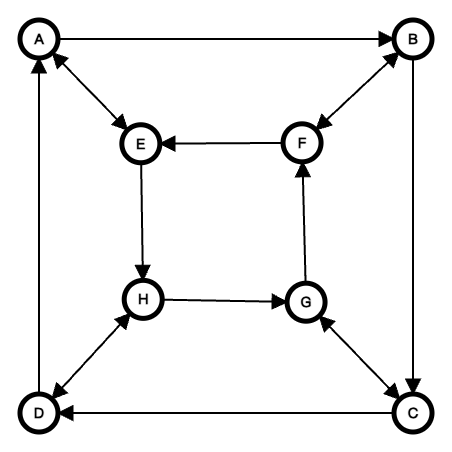
The reason why we choose to find stabilizer codes in the Cayley graph of a dihedral group is because it is a commutative group. We place qudits on the vertices of the Cayley graph. For each qudit, they represent different operations. We define the flip between the vertices in the outer square and the vertices in the inner square to be
Firstly, we choose a stabilizer, in which
Our purpose is to find a vector
We can apply our formula, thus we can get
Through basic calculation, we can get
Then,
The relationship between
In this case, it is easy to notice that there are multiple solutions for this equation. We can consider different cases. Here are some possible cases:
6. When
7. When
8. When
9. Also, we can have some more complicated cases. For example, when
Note that when we find stabilizer codes through this way, we can continue to find another one by using the one we just get. For example, for Case 1, we have already got
Therefore, by continuing calculating and finding various solutions, we can get different kinds of stabilizer codes and all of them can be clearly presented on Cayley graph.
7. Conclusion & further exploration
In conclusion, based on existing information of quantum computing and abstract algebra, we have devised an innovative method to find a stabilizer codes to solve our the problem of quantum errors. Specifically, we use a mathematical way to write the common way to find stabilizer codes and find that the methods can be extended to find stabilizer codes on a more complicated group or graph. We also give an example of how to use this method to find a stabilizer group on a dihedral graph
The further exploration is to develop a program on computer or to find a mathematical way to compare codes found through this methods among themselves and with existing stabilizer codes, thus contributing to the development of quantum computing.
References
[1]. Andrew Steane. Quantum computing. Reports on Progress in Physics, 61(2):117, 1998.
[2]. David P DiVincenzo and Daniel Loss. Quantum computers and quantum coherence. Journal of Magnetism and Magnetic Materials, 200(1-3):202–218, 1999.
[3]. Andrew M Steane. Error correcting codes in quantum theory. Physical Review Letters, 77(5):793, 1996.
[4]. A Robert Calderbank and Peter W Shor. Good quantum error-correcting codes exist. Physical Review A, 54(2):1098, 1996.
[5]. Andrew Steane. Multiple-particle interference and quantum error correction. Proceedings of the Royal Society of London. Series A: Mathematical, Physical and Engineering Sciences, 452(1954):2551–2577, 1996.
[6]. Andrew M Steane. Simple quantum error-correcting codes. Physical Review A, 54(6):4741, 1996.
[7]. Lucio Piccirillo. Introduction to the Maths and Physics of Quantum Mechanics. CRC Press, 2023.
[8]. Mike Krebs and Anthony Shaheen. Expander families and Cayley graphs: a beginner’s guide. Oxford University Press, 2011.
[9]. Ivan Djordjevic. Quantum information processing and quantum error correction: an engineering approach. Academic press, 2012.
[10]. James C Robinson. An introduction to functional analysis. Cambridge University Press, 2020.
[11]. Jeongwan Haah. Algebraic methods for quantum codes on lattices. arXiv preprint arXiv: 1607. 01387, 2016.
[12]. Gerhard Rosenberger, Annika Schürenberg, and Leonard Wienke. Abstract Algebra: With Applications to Galois Theory, Algebraic Geometry, Representation Theory and Cryptography. Walter de Gruyter GmbH & Co KG, 2024.
[13]. Weisheng Qiu. Group representation theory. Higher Education Press, 2011.
[14]. Mark J DeBonis. Fundamentals of Abstract Algebra. CRC Press, 2024.
[15]. Steven H Simon. Topological quantum: Lecture notes and proto-book. Unpublished prototype. [online] Available at: http://www-thphys. physics. ox. ac. uk/people/SteveSimon, 26:35, 2020.
[16]. Volker Diekert, Manfred Kufleitner, Gerhard Rosenberger, and Ulrich Hertrampf. Elements of Discrete Mathematics: Numbers and Counting, Groups, Graphs, Orders and Lattices. Walter de Gruyter GmbH & Co KG, 2023.
Cite this article
Gui,Y. (2025). Stabilizer Codes on a Cayley Graph. Advances in Operation Research and Production Management,4(1),79-91.
Data availability
The datasets used and/or analyzed during the current study will be available from the authors upon reasonable request.
Disclaimer/Publisher's Note
The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of EWA Publishing and/or the editor(s). EWA Publishing and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content.
About volume
Journal:Advances in Operation Research and Production Management
© 2024 by the author(s). Licensee EWA Publishing, Oxford, UK. This article is an open access article distributed under the terms and
conditions of the Creative Commons Attribution (CC BY) license. Authors who
publish this series agree to the following terms:
1. Authors retain copyright and grant the series right of first publication with the work simultaneously licensed under a Creative Commons
Attribution License that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this
series.
2. Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the series's published
version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial
publication in this series.
3. Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and
during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work (See
Open access policy for details).
References
[1]. Andrew Steane. Quantum computing. Reports on Progress in Physics, 61(2):117, 1998.
[2]. David P DiVincenzo and Daniel Loss. Quantum computers and quantum coherence. Journal of Magnetism and Magnetic Materials, 200(1-3):202–218, 1999.
[3]. Andrew M Steane. Error correcting codes in quantum theory. Physical Review Letters, 77(5):793, 1996.
[4]. A Robert Calderbank and Peter W Shor. Good quantum error-correcting codes exist. Physical Review A, 54(2):1098, 1996.
[5]. Andrew Steane. Multiple-particle interference and quantum error correction. Proceedings of the Royal Society of London. Series A: Mathematical, Physical and Engineering Sciences, 452(1954):2551–2577, 1996.
[6]. Andrew M Steane. Simple quantum error-correcting codes. Physical Review A, 54(6):4741, 1996.
[7]. Lucio Piccirillo. Introduction to the Maths and Physics of Quantum Mechanics. CRC Press, 2023.
[8]. Mike Krebs and Anthony Shaheen. Expander families and Cayley graphs: a beginner’s guide. Oxford University Press, 2011.
[9]. Ivan Djordjevic. Quantum information processing and quantum error correction: an engineering approach. Academic press, 2012.
[10]. James C Robinson. An introduction to functional analysis. Cambridge University Press, 2020.
[11]. Jeongwan Haah. Algebraic methods for quantum codes on lattices. arXiv preprint arXiv: 1607. 01387, 2016.
[12]. Gerhard Rosenberger, Annika Schürenberg, and Leonard Wienke. Abstract Algebra: With Applications to Galois Theory, Algebraic Geometry, Representation Theory and Cryptography. Walter de Gruyter GmbH & Co KG, 2024.
[13]. Weisheng Qiu. Group representation theory. Higher Education Press, 2011.
[14]. Mark J DeBonis. Fundamentals of Abstract Algebra. CRC Press, 2024.
[15]. Steven H Simon. Topological quantum: Lecture notes and proto-book. Unpublished prototype. [online] Available at: http://www-thphys. physics. ox. ac. uk/people/SteveSimon, 26:35, 2020.
[16]. Volker Diekert, Manfred Kufleitner, Gerhard Rosenberger, and Ulrich Hertrampf. Elements of Discrete Mathematics: Numbers and Counting, Groups, Graphs, Orders and Lattices. Walter de Gruyter GmbH & Co KG, 2023.









