1. Introduction
The rapid advancement of digital technologies has revolutionized the way content is created, distributed, and consumed. However, this digital transformation has also brought significant challenges in protecting intellectual property rights, leading to the development and implementation of Digital Rights Management (DRM) systems. DRM encompasses a range of technological tools and legal measures designed to control the use of digital content, ensuring that creators and rights holders can protect their works from unauthorized access and infringement. Encryption technologies and digital watermarking are fundamental components of DRM systems, each providing distinct mechanisms for securing digital content. Encryption transforms plaintext information into an unreadable format, accessible only to authorized users, while digital watermarking embeds hidden information within the content to track and identify usage. To understand the effectiveness of these technologies, we introduce mathematical models that quantify their performance over time [1]. The encryption effectiveness model and the watermark robustness model provide a framework for evaluating the security and resilience of DRM technologies against unauthorized access and degradation. Additionally, a comprehensive DRM effectiveness model integrates these individual models, considering user inconvenience to offer a holistic assessment of DRM system performance. This paper also explores the legal and regulatory aspects of DRM, highlighting the importance of compliance with international treaties and national laws. Case studies from the music, film, and publishing industries illustrate the practical implementation and impact of DRM technologies, providing insights into best practices and regulatory adherence. By examining these multifaceted aspects, this study aims to contribute to the academic and practical understanding of DRM, offering a framework for optimizing DRM strategies in a dynamic digital landscape.
2. Encryption Technologies in DRM
2.1. Theoretical Foundations of Encryption
Encryption serves as a cornerstone of DRM technologies, providing a robust method for securing digital content against unauthorized access and distribution. At its core, encryption involves converting plaintext information into an unreadable format using cryptographic algorithms, ensuring that only authorized users with the correct decryption key can access the original content. The strength of encryption lies in its ability to safeguard data at rest, in transit, and during processing, making it an essential tool in the DRM toolkit. Symmetric and asymmetric encryption are the two primary types used in DRM, each with its advantages and trade-offs in terms of security, performance, and implementation complexity. To mathematically model the effectiveness of encryption, we define the encryption effectiveness function E(t) as a function of time and security parameters, E(t)=α⋅S(t)−β⋅P(t), where S(t) is the security strength of the encryption algorithm over time, P(t) is the probability of a successful attack over time, and α and β are weighting factors [2]. Table 1 shows the simulated results of the encryption effectiveness model over a 12-month period. The model calculates the encryption effectiveness E(t) based on the security strength S(t) and the attack probability P(t), using the formula E(t)=α⋅S(t)−β⋅P(t), where α=0.9 and β=0.7. The values demonstrate how the effectiveness of encryption fluctuates over time, influenced by changes in security strength and attack probability.
Table 1. Encryption Effectiveness Model Results
Month | Security Strength (S(t)) | Attack Probability (P(t)) | Encryption Effectiveness (E(t)) |
1 | 0.903794 | 0.029220 | 0.792960 |
2 | 0.966982 | 0.015769 | 0.859245 |
3 | 0.988086 | 0.065278 | 0.843583 |
4 | 0.826819 | 0.013211 | 0.734890 |
5 | 0.824424 | 0.022294 | 0.726376 |
6 | 0.842203 | 0.061190 | 0.715150 |
7 | 0.968356 | 0.047475 | 0.838288 |
8 | 0.862330 | 0.010625 | 0.768659 |
9 | 0.853758 | 0.011187 | 0.760552 |
10 | 0.871170 | 0.060250 | 0.741878 |
11 | 0.811442 | 0.093589 | 0.664786 |
12 | 0.802686 | 0.058582 | 0.681410 |
2.2. Practical Applications of Encryption in DRM
In practical applications, encryption is employed across various digital platforms and content types, from e-books and software to multimedia files and streaming services. For instance, Advanced Encryption Standard (AES) is widely used to protect digital content distributed over the internet, ensuring that only paying customers can access and use the material. In streaming services, encryption protocols such as Secure Sockets Layer (SSL) and Transport Layer Security (TLS) are used to secure data transmission, preventing interception and unauthorized copying of content. These applications demonstrate how encryption technologies are integral to maintaining the integrity and security of digital content in a DRM context. By applying our encryption effectiveness model E(t), we can evaluate the expected reduction in unauthorized access over time, helping to optimize the deployment of encryption technologies. [3]
2.3. Legal and Regulatory Aspects of Encryption
The legal landscape surrounding encryption is complex and varies significantly across different jurisdictions. In the context of DRM, regulations often mandate the use of robust encryption standards to protect digital content, while also imposing restrictions on the export and use of certain cryptographic technologies. Laws such as the General Data Protection Regulation (GDPR) in the European Union and the Digital Millennium Copyright Act (DMCA) in the United States highlight the regulatory requirements and compliance obligations for organizations implementing DRM solutions. These legal frameworks aim to balance the need for strong encryption to protect intellectual property with national security concerns and law enforcement access. By integrating legal compliance into our encryption effectiveness model E(t), we can incorporate regulatory constraints into the optimization of encryption strategies.
3. Digital Watermarking in DRM
3.1. 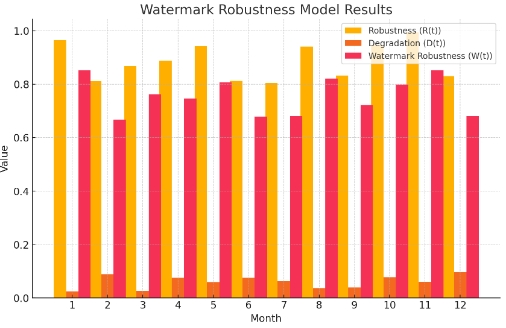 Concept and Mechanisms of Digital Watermarking
Concept and Mechanisms of Digital Watermarking
Figure 1. Watermark Robustness Model Results
Digital watermarking is another critical component of DRM systems, enabling the embedding of hidden information within digital content to identify and track its usage. This technique involves altering the original content in a way that is imperceptible to human senses but can be detected and extracted by specialized software. Watermarks can be either visible or invisible and may contain various types of information, such as ownership details, usage rights, or unique identifiers. The robustness of digital watermarking is determined by its resistance to common attacks such as compression, cropping, and re-encoding, ensuring that the embedded information remains intact and detectable under various conditions. To model the effectiveness of watermarking, we define the watermark robustness function W(t) as W(t)=γ⋅R(t)−δ⋅D(t), where R(t) represents the robustness of the watermark over time, D(t) is the degradation of the watermark due to attacks, and γ and δ are weighting factors. Figure 1 displays the simulated results of the watermark robustness model over a 12-month period. The model calculates the watermark robustness W(t) based on the robustness R(t) and the degradation D(t)), using the formula W(t)=γ⋅R(t)−δ⋅D(t), where γ=0.9 and δ=0.7. The values for robustness, degradation, and overall watermark robustness demonstrate how the effectiveness of digital watermarking varies over time, influenced by the robustness of the watermark and the degree of degradation due to attacks [4].
3.2. Applications of Digital Watermarking
In practice, digital watermarking is used across a wide range of media, including images, audio, video, and text documents. For instance, in the film and music industries, watermarking is used to trace the distribution of copyrighted materials and identify sources of unauthorized copies. In the publishing industry, digital watermarks are embedded in e-books and online articles to monitor their distribution and ensure compliance with licensing agreements [5]. These applications highlight the versatility of digital watermarking as a tool for enforcing DRM policies and protecting intellectual property rights across different types of digital content.
4. Copyright Protection Systems
4.1. Design and Implementation of Copyright Protection Systems
Comprehensive copyright protection systems integrate various DRM technologies to provide a holistic approach to intellectual property protection. These systems are designed to manage the entire lifecycle of digital content, from creation and distribution to consumption and enforcement. Key components include content encryption, access control mechanisms, usage tracking, and rights management information. The design of such systems must consider factors such as user convenience, scalability, and interoperability with other DRM solutions to ensure widespread adoption and effectiveness in preventing unauthorized use. To model the overall effectiveness of a copyright protection system, we combine our previously defined models E(t) and W(t) into a comprehensive DRM effectiveness function C(t), where C(t)=αE(t)+βW(t)−ϵ⋅U(t), with U(t) representing user inconvenience and ϵ\epsilonϵ being a weighting factor [16]. Table 2 shows the simulated results of the comprehensive DRM effectiveness model over a 12-month period. The model combines the encryption effectiveness E(t) and the watermark robustness W(t) into a comprehensive DRM effectiveness function C(t), which also accounts for user inconvenience U(t). The formula used is C(t)=αE(t)+βW(t)−ϵU(t), where α=0.9, β=0.7, and ϵ=0.5. The values demonstrate how the overall effectiveness of the DRM system varies over time, influenced by the effectiveness of encryption, the robustness of watermarking, and the level of user inconvenience [7].
Table 2. Comprehensive DRM Effectiveness Model Results
Month | Encryption Effectiveness (E(t)) | Watermark Robustness (W(t)) | User Inconvenience (U(t)) | Comprehensive DRM Effectiveness (C(t)) |
1 | 0.792960 | 0.851608 | 0.106573 | 1.256503 |
2 | 0.859245 | 0.668159 | 0.210333 | 1.135866 |
3 | 0.843583 | 0.762387 | 0.181058 | 1.202367 |
4 | 0.734890 | 0.746560 | 0.286947 | 1.040519 |
5 | 0.726376 | 0.806584 | 0.161156 | 1.137769 |
6 | 0.715150 | 0.678938 | 0.140253 | 1.048765 |
7 | 0.838288 | 0.679750 | 0.287904 | 1.086332 |
8 | 0.768659 | 0.821785 | 0.105583 | 1.214251 |
9 | 0.760552 | 0.721835 | 0.165123 | 1.107219 |
10 | 0.741878 | 0.798327 | 0.218432 | 1.117303 |
11 | 0.664786 | 0.852252 | 0.180739 | 1.104514 |
12 | 0.681410 | 0.680355 | 0.297449 | 0.940793 |
4.2. Case Studies of Copyright Protection Systems
Several case studies illustrate the practical implementation and impact of copyright protection systems in different industries. For example, the music streaming service Spotify employs a combination of encryption and watermarking technologies to protect its vast library of songs from piracy. Similarly, the publishing platform Kindle uses DRM technologies to control access to e-books and enforce licensing agreements. These case studies provide valuable insights into the challenges and successes of implementing comprehensive DRM solutions, highlighting best practices and lessons learned that can inform future developments in this field. By applying our comprehensive DRM effectiveness model C(t), we can quantitatively assess the success of these case studies and identify areas for improvement [8].
4.3. Regulatory Framework for Copyright Protection Systems
The regulatory framework for copyright protection systems encompasses a range of international and national laws aimed at harmonizing DRM practices and ensuring consistent enforcement of intellectual property rights. International treaties such as the WCT and the Agreement on Trade-Related Aspects of Intellectual Property Rights (TRIPS) establish baseline standards for copyright protection that member countries must adhere to. National laws, such as the DMCA and the EU Directive on Copyright in the Digital Single Market, provide specific legal provisions for the implementation and enforcement of DRM technologies. These regulations play a crucial role in shaping the development and deployment of copyright protection systems, ensuring that they comply with legal requirements and effectively safeguard intellectual property [9]. By integrating legal compliance considerations into our comprehensive DRM effectiveness model C(t), we can ensure that DRM systems are both effective and legally robust.
5. Challenges and Future Directions
5.1. Technological Challenges
Despite the advancements in DRM technologies, several technological challenges remain that hinder their effectiveness. One significant challenge is the constant evolution of piracy techniques, which requires DRM systems to be continuously updated and improved to stay ahead of potential threats. Another challenge is the balance between robust security measures and user convenience, as overly restrictive DRM can lead to a poor user experience and potentially drive consumers towards unauthorized alternatives. Addressing these challenges requires ongoing research and development to enhance the capabilities of DRM technologies while maintaining a user-friendly approach. Our comprehensive DRM effectiveness model C(t) can be used to identify and mitigate these technological challenges by optimizing the trade-offs between security, effectiveness, and user convenience [10].
5.2. Future Directions and Innovations
Looking ahead, several emerging technologies and trends hold promise for the future of DRM. Blockchain technology, for example, offers potential applications in the secure management and tracking of digital rights, providing a decentralized and tamper-proof solution for DRM. Additionally, advances in artificial intelligence and machine learning can enhance the capabilities of DRM systems, enabling more sophisticated detection and prevention of unauthorized access and distribution. Future research and innovation in these areas are essential to address the evolving challenges of digital content protection and ensure the continued effectiveness of DRM technologies. By integrating these emerging technologies into our comprehensive DRM effectiveness model C(t), we can develop next-generation DRM systems that are more resilient, adaptive, and effective in protecting intellectual property.
6. Conclusion
In conclusion, this paper has explored the multifaceted aspects of Digital Rights Management, focusing on the application and regulation of encryption technologies, digital watermarking, and comprehensive copyright protection systems. Through a detailed analysis of the technological mechanisms and legal frameworks that support DRM, this study has highlighted the critical role these systems play in protecting intellectual property in the digital age. The introduction of mathematical models to quantify the effectiveness of DRM technologies provides a robust framework for evaluating and optimizing these systems. The discussion has also identified key challenges and future directions for DRM, emphasizing the need for ongoing research and innovation to address the dynamic and complex landscape of digital content protection. By integrating technological advancements with robust legal standards, DRM can continue to provide a vital safeguard for intellectual property rights, ensuring that creators and rights holders can thrive in the digital economy.
Contribution
Lu Han and Mohong Liu: Conceptualization, Methodology, Data curation, Writing- Original draft preparation, Visualization, Investigation.
References
[1]. Calzada, Igor, Marc Pérez-Batlle, and Joan Batlle-Montserrat. "People-centered smart cities: An exploratory action research on the cities’ coalition for digital rights." Journal of Urban Affairs 45.9 (2023): 1537-1562.
[2]. Frolova, E. E., and E. V. Kupchina. "Digital Tools for the Protection of Intellectual Property Rights: A Case Study of Blockchain and Artificial Intelligence." Perm U. Herald Jurid. Sci. 61 (2023): 479.
[3]. Bühler, Michael Max, et al. "Unlocking the power of digital commons: Data cooperatives as a pathway for data sovereign, innovative and equitable digital communities." Digital 3.3 (2023): 146-171.
[4]. Eke, Damian, and Bernd Stahl. "Ethics in the Governance of Data and Digital Technology: An Analysis of European Data Regulations and Policies." Digital Society 3.1 (2024): 11.
[5]. Ngwenyama, Ojelanki, Helle Zinner Henriksen, and Daniel Hardt. "Public management challenges in the digital risk society: A critical analysis of the public debate on implementation of the Danish NemID." European Journal of Information Systems 32.2 (2023): 108-126.]
[6]. Alexan, Wassim, et al. "Color image encryption through chaos and kaa map." IEEE Access 11 (2023): 11541-11554.
[7]. Hohenberger, Susan, et al. "Registered attribute-based encryption." Annual International Conference on the Theory and Applications of Cryptographic Techniques. Cham: Springer Nature Switzerland, 2023.
[8]. Alawida, Moatsum. "A novel chaos-based permutation for image encryption." Journal of King Saud University-Computer and Information Sciences 35.6 (2023): 101595.
[9]. Lancaster, Thomas. "Artificial intelligence, text generation tools and ChatGPT–does digital watermarking offer a solution?." International Journal for Educational Integrity 19.1 (2023): 10.
[10]. Nematollahi, Mohammad Ali. "A machine learning approach for digital watermarking." Australian Journal of Multi-Disciplinary Engineering 19.1 (2023): 53-63.
Cite this article
Han,L.;Liu,M. (2024). Digital Rights Management (DRM) technologies and legal research: Applications and regulations of encryption, digital watermarking, and copyright protection systems. Applied and Computational Engineering,82,106-111.
Data availability
The datasets used and/or analyzed during the current study will be available from the authors upon reasonable request.
Disclaimer/Publisher's Note
The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of EWA Publishing and/or the editor(s). EWA Publishing and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content.
About volume
Volume title: Proceedings of the 2nd International Conference on Machine Learning and Automation
© 2024 by the author(s). Licensee EWA Publishing, Oxford, UK. This article is an open access article distributed under the terms and
conditions of the Creative Commons Attribution (CC BY) license. Authors who
publish this series agree to the following terms:
1. Authors retain copyright and grant the series right of first publication with the work simultaneously licensed under a Creative Commons
Attribution License that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this
series.
2. Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the series's published
version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial
publication in this series.
3. Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and
during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work (See
Open access policy for details).
References
[1]. Calzada, Igor, Marc Pérez-Batlle, and Joan Batlle-Montserrat. "People-centered smart cities: An exploratory action research on the cities’ coalition for digital rights." Journal of Urban Affairs 45.9 (2023): 1537-1562.
[2]. Frolova, E. E., and E. V. Kupchina. "Digital Tools for the Protection of Intellectual Property Rights: A Case Study of Blockchain and Artificial Intelligence." Perm U. Herald Jurid. Sci. 61 (2023): 479.
[3]. Bühler, Michael Max, et al. "Unlocking the power of digital commons: Data cooperatives as a pathway for data sovereign, innovative and equitable digital communities." Digital 3.3 (2023): 146-171.
[4]. Eke, Damian, and Bernd Stahl. "Ethics in the Governance of Data and Digital Technology: An Analysis of European Data Regulations and Policies." Digital Society 3.1 (2024): 11.
[5]. Ngwenyama, Ojelanki, Helle Zinner Henriksen, and Daniel Hardt. "Public management challenges in the digital risk society: A critical analysis of the public debate on implementation of the Danish NemID." European Journal of Information Systems 32.2 (2023): 108-126.]
[6]. Alexan, Wassim, et al. "Color image encryption through chaos and kaa map." IEEE Access 11 (2023): 11541-11554.
[7]. Hohenberger, Susan, et al. "Registered attribute-based encryption." Annual International Conference on the Theory and Applications of Cryptographic Techniques. Cham: Springer Nature Switzerland, 2023.
[8]. Alawida, Moatsum. "A novel chaos-based permutation for image encryption." Journal of King Saud University-Computer and Information Sciences 35.6 (2023): 101595.
[9]. Lancaster, Thomas. "Artificial intelligence, text generation tools and ChatGPT–does digital watermarking offer a solution?." International Journal for Educational Integrity 19.1 (2023): 10.
[10]. Nematollahi, Mohammad Ali. "A machine learning approach for digital watermarking." Australian Journal of Multi-Disciplinary Engineering 19.1 (2023): 53-63.









