1. Introduction
Underwater wireless sensor networks are one of the primary topics of global discussion and research, representing a crucial path for the development and utilization of marine resources. Underwater Wireless Sensor Networks (UWSNs) are network systems composed of multiple underwater sensor nodes interconnected through wireless communication technologies, primarily acoustic communication. The nodes in the network collect information, process the data, and transmit it to surface base stations, from which the data is then transmitted to land via satellite.
However, in underwater environments, optical and radio waves are incapable of long-distance transmission; therefore, acoustic communication is widely used. In the complex underwater environment, factors such as the temperature, salinity, and multipath effects of the medium can all influence the efficiency of underwater sensor networks. Due to the unique underwater conditions, terrestrial wireless sensor network protocols cannot be directly applied in underwater environments. Therefore, addressing the risks underwater sensor networks face and ensuring secure and efficient wireless network transmission is paramount. This paper discusses, in Section 2, underwater sensor network communication technologies and the structural characteristics of underwater sensor network nodes; in Section 3, the risks faced by underwater sensor networks; in Section 4, positioning and navigation technologies in underwater communications; and in Section 5, it concludes the paper.
2. Underwater Sensor Network Communication Technologies and Structural Characteristics of Underwater Sensor Network Nodes
2.1. Underwater Sensor Network Communication Technologies
Optical communication has characteristics of absorption and scattering, which cause a significant reduction in signal strength during transmission. Even microorganisms in the water can reduce the intensity of optical communication signals. The effective communication range of optical communication is limited, and water’s absorption of light signals makes long-distance communication difficult. An underwater optical communication system, using a high-power LED array at 470 nm and employing discrete pulse interval modulation, successfully achieved communication over a distance of 50 meters with a data rate of 2.28 Mbit/s [1]. Radio wave communication also suffers from severe intensity attenuation in water, with both high-frequency and low-frequency signals failing to meet the requirements for long-distance propagation. Electromagnetic waves propagating through water are subject to interference from underwater electromagnetic phenomena, making stable transmission difficult. The propagation speed of acoustic waves in water is only 1500 m/s, and the data transmission rate is limited to tens of kbps, thus failing to meet the demands for large-capacity data transmission [2].
2.2. Structural Characteristics of Underwater sensor Network Nodes
Underwater Sensor Networks (USNs) consist of numerous underwater sensor nodes that collect data and transmit communication in the water. The nodes have different functions, such as data collection, processing, storage, and forwarding. Underwater sensor nodes are typically composed of sensor units, communication units, processing units, storage units, and power units, with each unit responsible for different tasks in the complex underwater environment. The sensor units, such as depth and pH sensors, detect environmental parameters such as temperature, salinity, and depth in the water, which are then processed and analyzed by the processing unit. The communication units are responsible for data transmission between nodes and the communication base station on the surface.
2.3. Underwater Sensor Mobile Nodes
Underwater Sensor Mobile Nodes are underwater robotic devices equipped with sensor, communication, power, and control systems. In real-life applications, they are commonly used in underwater environmental monitoring, marine exploration, scientific research, fisheries monitoring, environmental protection, and other fields. Commonly used underwater mobile nodes include Autonomous Underwater Vehicles (AUVs), Remotely Operated Vehicles (ROVs), and small freely moving sensors. For example, the REMUS series AUVs produced by Hydroid have a cruising speed ranging from 1.5 m/s to 2.9 m/s, with endurance capabilities of up to several dozen hours in the case of shorter missions [3].
2.4. Architecture of Underwater Sensor Networks
Underwater sensor networks generally adopt a three-layer architecture, including the underwater sensing, relay, and surface layers. The underwater sensing layer is typically used for collecting environmental data from underwater; the relay layer mainly consists of underwater mobile nodes and Autonomous Underwater Vehicles (AUVs) (which use multi-hop communication); the surface layer acts as a bridge between the underwater network and the land, such as buoy base stations or surface unmanned vehicles.
Classification of UWSN topology.
(1) Star topology involves information transmission through a single hop to the surface base station.
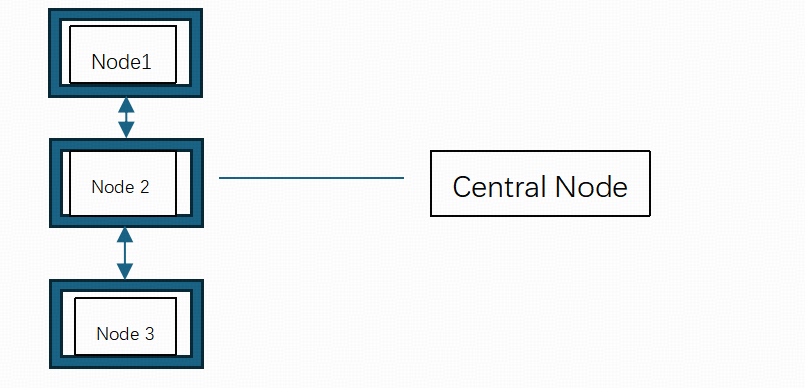
Figure 1: Star Topology
Star topology is elementary and easy to manage; however, the entire network system will fail if the central node fails.
(2) Cluster-based topology divides the sensor nodes into multiple clusters, where each cluster collects data from its nodes, processes it, and then transmits it to the surface base station.
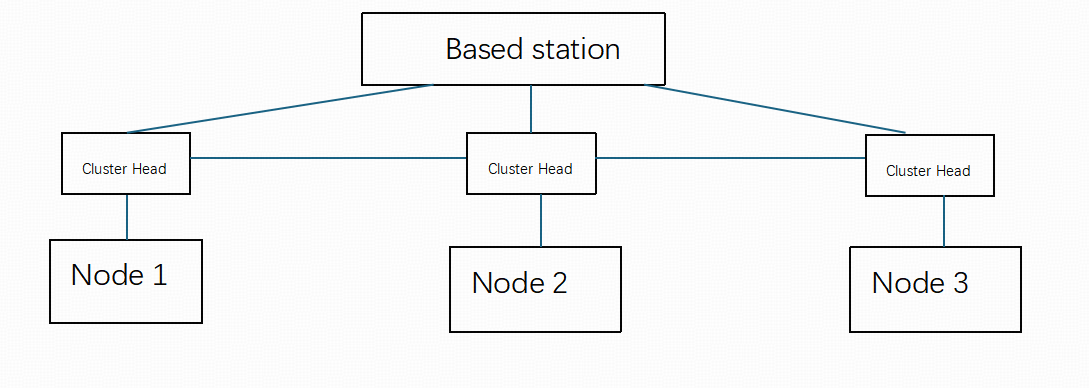
Figure 2: Cluster-Based Topology
(3) Mobile topology involves mobile nodes, such as AUVs and ROVs, that collect data underwater. These nodes are capable of adapting to complex underwater environments, offering high variability. The freely moving nodes can alter the transmission path as needed.
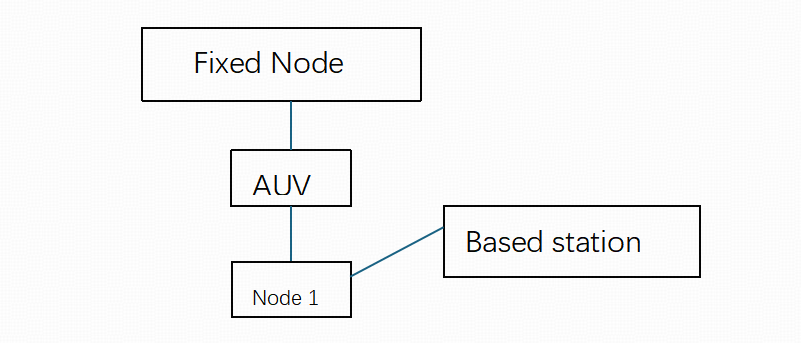
Figure 3: Mobile Topology
(4) Mesh topology consists of multiple mobile nodes that, in addition to their inherent flexibility, can transmit data to the surface base station through multiple paths. Even if some nodes fail, data transmission can still proceed smoothly.
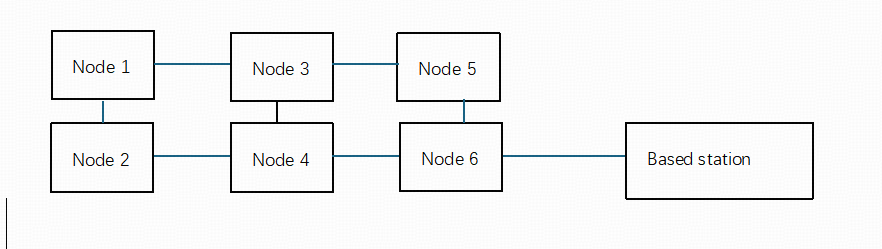
Figure 4: Mesh Topology
2.5. The Protocol Stack of Underwater Wireless Sensor Networks (UWSNs)
The protocol stack of Underwater Wireless Sensor Networks (UWSNs) can be divided into the Physical Layer, Data Link Layer, Network Layer, Transport Layer, Application Layer, and Security Layer.
(1) Physical Layer:
The Physical Layer is the foundational component of the network protocol stack, responsible for transmitting and receiving information in underwater environments. It transmits binary data (0s and 1s) and restores the original data at the receiving end. This layer often employs Multiple-Input Multiple-Output (MIMO) technology to enhance accuracy by sending multiple signals concurrently. Additionally, Orthogonal Frequency Division Multiplexing (OFDM) is a prevalent multi-carrier digital modulation technique that modulates data streams onto orthogonal subcarriers, providing benefits such as robust fading and interference resistance, high spectral efficiency, and straightforward system implementation [4].
(2) Network Layer:
The function of the Network Layer is to select routes and manage data. Since the positions of underwater mobile nodes are highly variable, routing protocols must cope with node location changes. Therefore, the routing protocols for underwater sensor networks must be capable of adapting to node mobility and dynamic underwater channels. Key considerations for the network layer include adaptability, low latency, and energy efficiency.
(3) Data Link Layer:
The Data Link Layer primarily ensures reliable data transmission between nodes by framing data within the network. It reconstructs the transmitted data from the Physical Layer's binary signals and incorporates error detection codes, such as CRC, to identify transmission errors, prompting retransmissions when necessary. Additionally, it manages physical layer resource allocation, including MAC addresses. Common MAC protocols include Aloha, which waits for a time gap post-collision before sending data, and TDMA, which allocates specific transmission times to prevent collisions. Underwater Data Link Layer protocols are uniquely designed to address high latency, interference, and packet loss, categorizing underwater MAC protocols into contention-based and fixed allocation types [5].
3. The Risks Faced by Underwater Sensor Networks (UWSNs)
Underwater Sensor Networks (UWSNs) are applied in many fields, such as marine resource exploration and military applications. Due to the high attenuation and delay of signal propagation in underwater channels, as well as the complex structural classification of the topology, various challenges arise.
Physical Layer Attacks include Jamming Attacks, Congestion Attacks, and Physical Tampering Attacks. A Congestion Attack occurs when an attacker sends noise and useless information, causing the neighboring nodes within the range to be unable to send or receive data. An optimized form of congestion attack targets only the Request-To-Send (RTS) packets, reducing the attacker's energy consumption [6-7]. Physical Tampering refers to direct physical damage that causes loss of functionality, such as direct destruction or explosion, or the recovery of nodes for data tampering and theft.
The Data Link Layer manages data transmission between nodes in the underwater sensor network. During data transmission and reception, nodes may face Collision Attacks, Denial of Service (DoS) Attacks, and MAC Spoofing Attacks, all of which can lead to information loss, leakage, and other issues.
Collision Attacks refer to the transmission of interfering data that disrupts normal data transmission. Under the competitive conditions of the MAC protocol, this attack prevents nodes from accessing channel resources. A Denial of Service (DoS) Attack exploits unnecessary handshake requests, consuming resources and causing service denial. DoS attacks can be categorized into bandwidth consumption, computational resource depletion, and protocol vulnerability exploitation.
Protocol Vulnerability Exploitation DoS: A typical example is the TCP Half-Connection Attack (SYN Flood), in which multiple TCP handshakes are initiated but not completed, thus occupying the server's response capacity. This leads to the server being maliciously attacked and the service being denied. Another example is the UDP Amplification Attack, where a forged IP address sends small requests to the server, which responds with much larger data. This response exceeds the initial request and fills up the available bandwidth, leading to congestion and disruption of normal network operations. MAC Spoofing Attack involves an attacker impersonating a legitimate node, causing the transmission node to believe it is communicating with a legitimate node, and leading to the malicious node intercepting or dropping and tampering with data.
Network Layer Attacks target routing information and IP addresses, such as Blackhole Attacks. In this attack, a malicious node falsely claims to be the shortest route, allowing data packets to be routed through it. The malicious node then drops the packets, causing data transmission failure. A Grayhole Attack is similar to the blackhole attack but is harder to detect because it selectively drops a portion of the data, forcing both the sender and receiver to verify the delivery of each data packet during transmission.
The Application Layer, the topmost layer of the OSI model, facilitates network services and data exchange. It is frequently targeted by email attacks, resulting in spam floods and mailbox failures. Attackers may also embed malware, including trojans and ransomware, into websites. In healthcare, infected systems can extort patients or lock medical data, demanding ransom for access. Preventive measures against application layer attacks include authentication and AI-driven detection.
4. Underwater Communication Localization and Navigation
The underwater acoustic positioning and navigation system technology relies on measuring sound wave propagation, phase, and other information to achieve positioning and navigation. Acoustic communication is, to date, the most effective carrier of information, and underwater acoustic positioning technology is currently the primary method for underwater target localization and tracking [8]. Depending on the baseline length of the positioning system and its operational mode, it is generally classified into long baseline systems, short baseline systems, ultra-short baseline systems, and integrated positioning systems [9-11].
Acoustic positioning is the primary method for underwater communication, utilizing techniques such as Long Baseline (LBL) and Short Baseline (SBL) systems. In LBL, an Autonomous Underwater Vehicle (AUV) transmits an acoustic signal to a known station, with distance calculated via return wave time. SBL employs multiple surface sensors to send signals to a target, determining position through distance and angle calculations. Inertial navigation, a novel technology, assesses acceleration and angular velocity to track positional changes. The evolution from acoustic positioning to a hybrid of acoustic and inertial navigation signifies a shift from narrowband to broadband systems, transitioning from limited user operations to dense, targeted applications, and expanding from singular positioning functions to multi-functional integration. Consequently, positioning accuracy has advanced from tens of meters to meter-level precision [10].
However, the observation data from underwater acoustic positioning and navigation systems are characterized by high latency, low data rates, and low effectiveness, meaning that underwater acoustic positioning and navigation technology is still in its early stages [10].
New Underwater Communication Technologies: Today, underwater communication technologies rely primarily on acoustic communication, but future developments are expected to move toward underwater optical communication, offering broadband and high-speed capabilities. Intelligent underwater communication networks represent the current trend, such as the Internet of Underwater Things (IoUT), which will make underwater sensor networks smarter and enable collaborative work. The integration of ocean digital twins with underwater sensor networks can predict marine natural disasters and protect the ecological environment.
5. Conclusion
Underwater sensor networks are an important technological support for ocean resource development and military applications. Currently, underwater sensor networks rely on acoustic communication technology, but due to low bandwidth and the impact of multipath effects, the information transmission efficiency is not high. Optical communication and radio wave communication still face challenges and difficulties in underwater environments. Underwater sensor networks employ multiple architectures, combining star, cluster, mobile, and mesh topologies to meet the needs of different scenarios. The protocol stack of underwater sensor networks differs greatly from terrestrial networks; the physical layer, data link layer, network layer, and application layer are all modified to accommodate the underwater environment. Underwater sensor networks encounter numerous security threats, with attacks targeting the physical, data link, network, and application layers.
References
[1]. Yale University. (2024, June 19). Aqua Optical III: Research and prospects of underwater optical communication technology. NetEase Subscription.
[2]. Google Patents. (n.d.). CN111245523B - Underwater data transmission system. Retrieved from https://patents.google.com/patent/CN111245523B/zh
[3]. Stokey, R., Roup, A., & Alt, V. (2005). Development of the REMUS 600 Autonomous Underwater Vehicle. In Proceedings of OCEANS 2005 (pp. 1301-1304). IEEE.
[4]. Gu, C., Zhang, J. D., & Zhu, X. H. (2009). Signal processing and detection of multi-carrier modulation radar systems based on OFDM. Journal of Electronics and Information Technology, 31(6), 1298-1300.
[5]. Wei, Z. Q., Yang, G., & Cong, Y. P. (2012). Research on underwater sensor network security (Doctoral dissertation).
[6]. Law, Y. W., van Hoesel, L., Doumen, J., Hartel, P., Havinga, P., & Palaniswami, M. (2009). Energy-efficient link-layer jamming attacks against wireless sensor network MAC protocols. ACM Transactions on Sensor Networks, 5(1), 76-88.
[7]. Raymond, D. R., Marchany, R. C., Brownfield, M. I., & Midki, S. F. (n.d.). Effects of denial-of-sleep attacks on wireless sensor networks.
[8]. Sun, D. J., Zheng, C. E., Zhang, J. C., Han, Y. F., & Cui, H. Y. (2019). Development and prospects of underwater acoustic positioning and navigation technology. Bulletin of the Chinese Academy of Sciences, 34(3), 331-338.
[9]. Qian, H. B., & Sun, D. J. (2011). Current status of underwater acoustic positioning systems. Acoustics Technology, 30(3), 389-391.
[10]. Sun, D. J., Zheng, C. E., Qian, H. B., et al. (2012). Application of underwater acoustic positioning systems in marine engineering. Acoustics Technology, (2), 125-132. https://doi.org/10.3969/j.issn1000-3630.2012.02.003
[11]. Tian, T. (2007). Underwater positioning and navigation technology. Beijing: National Defense Industry Press.
Cite this article
Zhou,G. (2025). Current Status and Future Prospects of Underwater Wireless Sensor Networks. Applied and Computational Engineering,150,21-26.
Data availability
The datasets used and/or analyzed during the current study will be available from the authors upon reasonable request.
Disclaimer/Publisher's Note
The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of EWA Publishing and/or the editor(s). EWA Publishing and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content.
About volume
Volume title: Proceedings of the 3rd International Conference on Software Engineering and Machine Learning
© 2024 by the author(s). Licensee EWA Publishing, Oxford, UK. This article is an open access article distributed under the terms and
conditions of the Creative Commons Attribution (CC BY) license. Authors who
publish this series agree to the following terms:
1. Authors retain copyright and grant the series right of first publication with the work simultaneously licensed under a Creative Commons
Attribution License that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this
series.
2. Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the series's published
version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial
publication in this series.
3. Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and
during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work (See
Open access policy for details).
References
[1]. Yale University. (2024, June 19). Aqua Optical III: Research and prospects of underwater optical communication technology. NetEase Subscription.
[2]. Google Patents. (n.d.). CN111245523B - Underwater data transmission system. Retrieved from https://patents.google.com/patent/CN111245523B/zh
[3]. Stokey, R., Roup, A., & Alt, V. (2005). Development of the REMUS 600 Autonomous Underwater Vehicle. In Proceedings of OCEANS 2005 (pp. 1301-1304). IEEE.
[4]. Gu, C., Zhang, J. D., & Zhu, X. H. (2009). Signal processing and detection of multi-carrier modulation radar systems based on OFDM. Journal of Electronics and Information Technology, 31(6), 1298-1300.
[5]. Wei, Z. Q., Yang, G., & Cong, Y. P. (2012). Research on underwater sensor network security (Doctoral dissertation).
[6]. Law, Y. W., van Hoesel, L., Doumen, J., Hartel, P., Havinga, P., & Palaniswami, M. (2009). Energy-efficient link-layer jamming attacks against wireless sensor network MAC protocols. ACM Transactions on Sensor Networks, 5(1), 76-88.
[7]. Raymond, D. R., Marchany, R. C., Brownfield, M. I., & Midki, S. F. (n.d.). Effects of denial-of-sleep attacks on wireless sensor networks.
[8]. Sun, D. J., Zheng, C. E., Zhang, J. C., Han, Y. F., & Cui, H. Y. (2019). Development and prospects of underwater acoustic positioning and navigation technology. Bulletin of the Chinese Academy of Sciences, 34(3), 331-338.
[9]. Qian, H. B., & Sun, D. J. (2011). Current status of underwater acoustic positioning systems. Acoustics Technology, 30(3), 389-391.
[10]. Sun, D. J., Zheng, C. E., Qian, H. B., et al. (2012). Application of underwater acoustic positioning systems in marine engineering. Acoustics Technology, (2), 125-132. https://doi.org/10.3969/j.issn1000-3630.2012.02.003
[11]. Tian, T. (2007). Underwater positioning and navigation technology. Beijing: National Defense Industry Press.









