1. Introduction
With the rapid pace of digitization, maintaining data integrity and protecting privacy have emerged as significant challenges within the information technology landscape. The frequent incidents of data breaches and privacy violations pose severe threats to individuals, businesses, and even national security [1]. Blockchain technology, characterized by its inherent resistance to modification, decentralization, and cryptographic security, offers innovative solutions to these challenges [2].
Blockchain technology assures that once data is recorded on its ledger, it cannot be altered covertly, thus safeguarding the data’s authenticity and enabling traceability [3]. This immutable nature of blockchain is crucial for the verification and integrity of data. Moreover, blockchain's decentralized architecture reduces the risk of centralized control, thereby enhancing the system's resilience against attacks [4]. In terms of privacy, the application of advanced encryption techniques within blockchain ensures the secure transmission and storage of data, allowing only authorized users access to sensitive information, which is vital for protecting user privacy [5][6].
However, despite the theoretical benefits, blockchain faces practical challenges such as scalability, performance, and integration with existing systems. These issues must be addressed to fully leverage blockchain in safeguarding data integrity and privacy [7][8]. This study aims to explore how blockchain can overcome these limitations to enhance secure data storage, processing, and transmission. It also seeks to propose practical solutions to facilitate the broader application of blockchain in data integrity and privacy protection sectors.
This paper will provide a detailed analysis of blockchain's mechanisms and principles related to data integrity and privacy protection, evaluate its effectiveness in real-world scenarios, and explore potential integrations with other cutting-edge technologies like artificial intelligence and the Internet of Things (IoT) to further enhance data security [9]-[14].
2. The effect of blockchain technology application in real scenarios
2.1. Application in Financial Transaction Scene
In financial transaction scenarios, the application of blockchain technology demonstrates its excellent potential in data integrity and privacy protection. The traditional financial transaction system relies on centralized intermediaries, which not only increases transaction costs, but also is vulnerable to single point of failure and fraud. In contrast, the distributed nature of the blockchain allows each transaction record to be replicated and stored on multiple nodes of the network, creating a tamper-proof public ledger (L) that ensures data integrity and transparency.
The formula:
L = 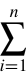 Ti , (1)
Ti , (1)
In this context, Ti represents the i-th transaction record, and n is the total number of transaction records. This decentralized architecture eliminates the need for trust in third parties, reducing the time and cost of transaction verification. In terms of privacy protection, blockchain technologies like Zero-Knowledge Proofs (ZKP) allow one party
(the prover P) to demonstrate to another party (the verifier V) that they possess certain information (e.g., ownership of specific funds) without revealing the information itself:
P → V : (proof|Z KP), (2)
Such interactions ensure the anonymity and privacy of transactions while preventing double-spending attacks and other fraudulent activities.
Furthermore, the implementation of Smart Contracts (SC) on the blockchain further enhances the security and automation of financial transactions:
SC (c, t1, t2, . . . , tn ) → Execution, (3)
In this context,c represents the contract conditions,ti is the events that trigger the execution of the contract. Smart contracts automate predefined rules, reducing the need for human intervention and lowering the risk of breach.
In summary, blockchain technology enhances the integrity and privacy of data in financial transactions through its distributed ledger, zero-knowledge proofs, and smart contracts, bringing revolutionary changes to the financial industry. However, despite these advancements, attention must still be paid to the scalability, energy consumption, and regulatory adaptability of blockchain technology to promote its application in broader fields.
2.2. Application in Medical Record Scenarios
In the context of medical records, the application of blockchain technology demonstrates its exceptional potential for data integrity and privacy protection. Traditional medical information systems often face issues like data silos, patient privacy breaches, and tampering risks. The distributed nature of blockchain, its immutable ledger, and smart contracts provide innovative solutions to these problems.
Firstly, through a decentralized network structure, blockchain technology enables medical data to be stored not in a single institution but distributed across various network nodes. This method of distributed storage (Table 1) reduces the risk of single points of failure, enhancing data availability and reliability. Each block contains the hash value of the previous block, forming a continuous chain-like structure. Any modifications to existing data will result in changes in the hash values of subsequent blocks, thereby facilitating the detection of tampering.
Table 1. Blockchain Distributed Storage Schematic
Block | Data | Previous Block Hash |
1 | Patient A’s Record | - |
2 | Update to Patient A’s Record | Hash of Block 1 |
3 | Additional Data | Hash of Block 2 |
... | ... | ... |
n | Latest Update | Hash of Block (n-1) |
2.3. Application in Supply Chain Management
In the complex and dynamic field of supply chain management, the application of blockchain technology demonstrates its unique advantages. Traditional supply chain management systems are often limited by information silos, lack of transparency, and trust issues, leading to inefficiency and increased potential risks. Blockchain technology, with its distributed ledger and smart contracts, provides innovative solutions to these problems (Table 1).
In practical applications, blockchain technology significantly enhances the transparency of the supply chain. For example, by recording every transaction on the blockchain, all participants can view the status of goods in real-time, from production to delivery, making the entire process transparent and reducing the possibility of fraud (1-4).
Table 2. Core Advantages of Blockchain Technology in Supply Chain Management
Advantage | Description |
Decentralization | Eliminates single points of failure, enhancing system robustness |
Transparency | All transaction records are publicly accessible, enhancing trust |
Immutability | Once data is recorded, it cannot be altered, ensuring data integrity |
Smart Contract | Automatically executes contractual terms, reducing operational errors and disputes |
Traceability | Real-time tracking of goods, ensuring traceability from source, improving efficiency |
T = 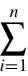 Ti , (4)
Ti , (4)
In this context, T represents the overall transparency of the supply chain, while Ti indicates the transparency of the i -th link in the chain.
Additionally, smart contracts automatically execute contract terms, reducing manual intervention and minimizing operational errors and disputes. When preset conditions are met, the contract automatically executes actions such as payment and delivery, enhancing transaction efficiency (1-5):
E = f (C, V), (5)
In this context,E represents efficiency improvement,C stands for smart contracts,V denotes the verification and execution process.
In summary, the application of blockchain technology in supply chain management not only enhances data integrity but also effectively protects the privacy of participants. By increasing transparency and automating processes, it significantly improves the operational efficiency and security of the supply chain. However, despite these significant achievements, attention must still be given to the standardization of technology, regulatory adaptability, and the costs of large-scale deployment to promote the widespread application of blockchain in supply chain management.
3. Comparative Analysis with Traditional Network Security Technologies
In exploring the application of blockchain technology for data integrity and privacy protection, we focuses on the comparative analysis between blockchain technology and traditional network security technologies. Blockchain technology, with its core features of a distributed ledger and cryptographic algorithms, has brought revolutionary changes to network security. Compared to traditional centralized storage and authentication methods, blockchain's decentralized architecture eliminates single points of failure and enhances data immutability, thereby showing significant advantages in protecting data integrity.
Traditional network security technologies rely on firewalls and access control lists to prevent unauthorized access, but these measures are often inadequate in the face of internal threats or advanced persistent threats. In contrast, blockchain’s smart contracts provide automatically executed rules, ensuring that only transactions that meet preset conditions are executed, greatly enhancing the security management efficiency of network resources. Additionally, blockchain's cryptographic algorithms, such as Elliptic Curve Cryptography (ECC) and hash functions (H(x)), ensure the privacy of data transmission and storage, making it difficult for intercepted data to be easily decrypted or tampered with.
However, blockchain is not a panacea. It faces challenges such as scalability issues and energy consumption. For example, the transaction processing speed of the Bitcoin network is much lower than that of credit card networks, and it consumes a significant amount of energy. Moreover, although anonymity is a notable feature of blockchain, the maturity of technologies like zero-knowledge proofs still needs to be improved to fully balance privacy protection with anti-money laundering and anti-fraud requirements.
In conclusion, blockchain technology demonstrates strong potential in data integrity and privacy protection, but it also needs to address the limitations of existing technologies for broader and deeper application. Through continuous technological innovation and optimization, blockchain is expected to become an indispensable pillar in the field of network security, complementing traditional technologies to build a more secure and trustworthy network environment.
4. Conclusion
In this research, we have explored in-depth the core role of blockchain technology in data integrity and privacy protection, revealing its potential as the future infrastructure for information security. Our findings are summarized as follows:
Firstly, we have shown how blockchain's distributed nature ensures data immutability. Through the hash-linked block structure (2-1), each block contains the hash value of the previous block, forming a chain. Any modification to historical data will cause changes in subsequent block hash values, which are quickly discovered by nodes in the network.
Hi = H (datai ||Hi−1) (6)
Secondly, the introduction of smart contracts has enhanced the transparency and automation of data processing. These self-executing contracts (2-2) define rules and conditions that automatically execute when preset conditions are met, reducing human intervention and enhancing the security of data exchange.
f (state, input) → (output , new_state) (7)
Furthermore, we have explored how Zero-Knowledge Proofs (ZKP) can verify the authenticity of data without disclosing the original information. ZKP allows one party (the prover) to prove to another party (the verifier) that they know certain information without revealing the information itself, thus finding a balance between privacy protection and verification (2-3).
P ⊢Σ K : Proof (8)
Despite these advancements, blockchain technology still faces challenges related to scalability, energy consumption, and regulatory adaptability. Future research should focus on optimizing consensus algorithms, exploring more energy-efficient solutions, and aligning with existing regulatory frameworks to promote the widespread application of blockchain in the fields of data integrity and privacy protection.
In summary, blockchain technology has not only revolutionized the way data is managed and protected but has also laid the foundation for building a more secure and transparent information environment. As the technology matures, we look forward to blockchain demonstrating its unique value in more areas, providing strong support for the global digital transformation.
References
[1]. Zhang, X. (2023). Applications of Artificial Intelligence in Cybersecurity. Wireless Internet Technology, 20(06), 29-35.
[2]. Lin, H. Y., Wang, J., Niu, D., et al. (2024). Blockchain-driven framework for construction waste recycling and reuse. Journal of Building Engineering, 89109355.
[3]. Zhu, L., Jiang, H., Zhu, J., et al. (2024). Hardware method for zero optical path difference position detection of FTIR spectrometer. Measurement: Sensors, 33101153.
[4]. Endace. (2020). Endace Wins Big in Cyber Defense Magazine and Info Security Products Guide Awards; EndaceProbe Analytics Platform receives ten awards including Best Security Hardware, Best Packet Capture Product, Most Innovative Security Hardware, and Best Network Security and Management. M2 Presswire.
[5]. Dong, Y., & Han, Q.-L. (2019). Guest Editorial Special Issue on New Trends in Energy Internet: Artificial Intelligence-Based Control, Network Security, and Management. IEEE Transactions on Systems, Man, and Cybernetics: Systems, 49(8).
[6]. IEEE. (2019). Special Issue on New Trends in Energy Internet: Artificial intelligence-Based Control, Network Security and Management. IEEE Transactions on Systems, Man, and Cybernetics: Systems, 49(1).
[7]. Cai, Z., Hu, C., Zheng, K., Xu, Y., & Fu, Q. (2018). Network Security and Management in SDN. Security and Communication Networks, 2018(2018).
[8]. Cyberoam Technologies Pvt. Ltd. (2015). Patent Issued for Identity and Policy-Based Network Security and Management System and Method. Journal of Engineering.
[9]. Zubaydi, H. D., Varga, P., & Molnár, S. (2023). Leveraging Blockchain Technology for Ensuring Security and Privacy Aspects in Internet of Things: A Systematic Literature Review. Sensors, 23(2), 788. https://doi.org/10.3390/s23020788
[10]. Taherdoost, H. (2023). Privacy and Security of Blockchain in Healthcare: Applications, Challenges, and Future Perspectives. Sci, 5(4), 41. https://doi.org/10.3390/sci5040041
[11]. Zhang, X. (2023). Applications of Artificial Intelligence in Cybersecurity. Wireless Internet Technology, 20(06), 29-35.
[12]. Lin, H. Y., Wang, J., Niu, D., et al. (2024). Blockchain-driven framework for construction waste recycling and reuse. Journal of Building Engineering, 89109355.
[13]. Zhu, L., Jiang, H., Zhu, J., et al. (2024). Hardware method for zero optical path difference position detection of FTIR spectrometer. Measurement: Sensors, 33101153.
[14]. Endace. (2020). Endace Wins Big in Cyber Defense Magazineand Info Security Products Guide Awards; EndaceProbe Analytics Platform receives ten awards including Best Security Hardware, Best Packet Capture Product, Most Innovative Security Hardware, and Best Network Security and Management. M2 Presswire.
Cite this article
Meng,X. (2024). Exploring the role of blockchain technology in enhancing data integrity and privacy protection. Applied and Computational Engineering,87,1-5.
Data availability
The datasets used and/or analyzed during the current study will be available from the authors upon reasonable request.
Disclaimer/Publisher's Note
The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of EWA Publishing and/or the editor(s). EWA Publishing and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content.
About volume
Volume title: Proceedings of the 6th International Conference on Computing and Data Science
© 2024 by the author(s). Licensee EWA Publishing, Oxford, UK. This article is an open access article distributed under the terms and
conditions of the Creative Commons Attribution (CC BY) license. Authors who
publish this series agree to the following terms:
1. Authors retain copyright and grant the series right of first publication with the work simultaneously licensed under a Creative Commons
Attribution License that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this
series.
2. Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the series's published
version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial
publication in this series.
3. Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and
during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work (See
Open access policy for details).
References
[1]. Zhang, X. (2023). Applications of Artificial Intelligence in Cybersecurity. Wireless Internet Technology, 20(06), 29-35.
[2]. Lin, H. Y., Wang, J., Niu, D., et al. (2024). Blockchain-driven framework for construction waste recycling and reuse. Journal of Building Engineering, 89109355.
[3]. Zhu, L., Jiang, H., Zhu, J., et al. (2024). Hardware method for zero optical path difference position detection of FTIR spectrometer. Measurement: Sensors, 33101153.
[4]. Endace. (2020). Endace Wins Big in Cyber Defense Magazine and Info Security Products Guide Awards; EndaceProbe Analytics Platform receives ten awards including Best Security Hardware, Best Packet Capture Product, Most Innovative Security Hardware, and Best Network Security and Management. M2 Presswire.
[5]. Dong, Y., & Han, Q.-L. (2019). Guest Editorial Special Issue on New Trends in Energy Internet: Artificial Intelligence-Based Control, Network Security, and Management. IEEE Transactions on Systems, Man, and Cybernetics: Systems, 49(8).
[6]. IEEE. (2019). Special Issue on New Trends in Energy Internet: Artificial intelligence-Based Control, Network Security and Management. IEEE Transactions on Systems, Man, and Cybernetics: Systems, 49(1).
[7]. Cai, Z., Hu, C., Zheng, K., Xu, Y., & Fu, Q. (2018). Network Security and Management in SDN. Security and Communication Networks, 2018(2018).
[8]. Cyberoam Technologies Pvt. Ltd. (2015). Patent Issued for Identity and Policy-Based Network Security and Management System and Method. Journal of Engineering.
[9]. Zubaydi, H. D., Varga, P., & Molnár, S. (2023). Leveraging Blockchain Technology for Ensuring Security and Privacy Aspects in Internet of Things: A Systematic Literature Review. Sensors, 23(2), 788. https://doi.org/10.3390/s23020788
[10]. Taherdoost, H. (2023). Privacy and Security of Blockchain in Healthcare: Applications, Challenges, and Future Perspectives. Sci, 5(4), 41. https://doi.org/10.3390/sci5040041
[11]. Zhang, X. (2023). Applications of Artificial Intelligence in Cybersecurity. Wireless Internet Technology, 20(06), 29-35.
[12]. Lin, H. Y., Wang, J., Niu, D., et al. (2024). Blockchain-driven framework for construction waste recycling and reuse. Journal of Building Engineering, 89109355.
[13]. Zhu, L., Jiang, H., Zhu, J., et al. (2024). Hardware method for zero optical path difference position detection of FTIR spectrometer. Measurement: Sensors, 33101153.
[14]. Endace. (2020). Endace Wins Big in Cyber Defense Magazineand Info Security Products Guide Awards; EndaceProbe Analytics Platform receives ten awards including Best Security Hardware, Best Packet Capture Product, Most Innovative Security Hardware, and Best Network Security and Management. M2 Presswire.









