1. Introduction
It is widely acknowledged that the rapid technological advancement in computing and the proliferation of IoT devices is a revolution that has positively transformed many sectors, ranging from healthcare, transportation, manufacturing and smart cities, to name just a few. These IoT devices consist of a myriad of sensors, actuators and smart appliances that generate data which can then be modelled and analysed for the purposes of optimising the operations, increasing efficiency and enhancing the user's experience. The technological revolution has, however, substantial challenges, particularly pertaining to the security and privacy of the data that is generated and transmitted by the physical IoT devices. The prime concern is the protection of the data transmitted by the IoT devices against unauthorised access and cyber-attacks. As the IoT devices become more prevalent in our daily lives, the attack surface is likely to increase since there is a greater likelihood of malicious actors exploiting the vulnerabilities in these devices. This is more likely, given that the devices are characterised by limited computational power and storage, which constrain the ability to implement robust security measures. Moreover, the heterogeneity of the IoT devices constitutes a challenge to the security landscape given that there are no uniform standards for security implementation. The regulatory landscape for IoT security and privacy is also in a rapid state of change, where various regions have varying standards and requirements. For organisations operating in several jurisdictions across the world, the challenge is to locate the intersections of these various laws and be compliant with laws such as the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA) in the United States, which were introduced in May 2018. Non-compliance incurs hefty penalties and reputational damage, and it is therefore crucial that organisations keep abreast of the regulatory changes and implement appropriate measures to safeguard the data of their users. This paper explores innovations in computer technology and IoT security regarding encryption, blockchain technology and applications of artificial intelligence (AI) and machine learning (ML) employed to enhance IoT security [1]. It also discusses critical challenges, such as data overload, regulatory compliance and the security vulnerabilities in IoT devices. Finally, it outlines strategies to strengthen privacy protection, such as implementing strong encryption protocols, Privacy by Design and increasing user awareness and education.
2. Innovations in Computer Technology and IoT Security
2.1. Advanced Encryption Techniques
Since time immemorial, encryption has played a vital role in data security. Recently, new encryption techniques have improved the level of security between IoT devices and central systems, for example, quantum cryptography uses the laws of quantum mechanics to generate unbreakable encryption keys and protect data from all known cyber-attacks. Quantum key distribution (QKD) is a quantum cryptography technique that uses quantum mechanics to exchange encryption keys between parties in a way that guarantees any eavesdropping will be detected. When measuring the quantum key, it changes the state of the key, thus notifying the communicating parties of an intruder. Homomorphic encryption is another technique that allows computations to be performed on encrypted data without the need to decrypt it, enabling data processing in cloud environments [2]. Homomorphic encryption enables cryptographic algorithms that support addition and multiplication on ciphertexts. Homomorphic encryption protects data confidentiality by allowing complex computations on the ciphertext without having to first decrypt it. Table 1 outlines the main innovations, challenges and strategies discussed in this paper in a compact and digestible way, highlighting the key innovations for IoT security and privacy protection [3].
Table 1. Innovations, Challenges, and Strategies in IoT Security and Privacy
Category | Subcategory | Details | Example | Impact |
Innovations in IoT Security | Advanced Encryption Techniques | Quantum cryptography, homomorphic encryption, and quantum key distribution | Unbreakable encryption keys, secure data processing | Enhanced data confidentiality, reduced risk of data breaches |
Challenges in Privacy Protection | Data Overload and Privacy Management | Managing large volumes of data, ensuring privacy protection for sensitive information | Handling sensitive personal data from smart home devices | Improved data governance, protection from unauthorized access |
Strategies for Enhancing Privacy Protection | Implementing Strong Encryption Protocols | End-to-end encryption, secure communication protocols, and regular updates | TLS for web communications, updated encryption standards | Increased data security, compliance with regulations |
2.2. Blockchain for IoT Security
The blockchain technology represents a unique solution for securing IoT as it enables decentralised and tamper-proof data storage. Any transaction or data entry is recorded in a distributed ledger, cryptographically secured and immutable, meaning that data cannot be altered or deleted without the consensus of all the network participants. That’s why IoT smart supply chain management system using blockchain can track the origin and movement of goods, a process that can be completely transparent to all participants of a supply chain with the guarantee that the data is tamper-proof. Smart contracts, that are self-executing contracts with the terms of the agreement written into the lines of code and executed automatically, can add more security to the IoT building block as all processes can be automated in this way, reducing the possibilities of human errors and fraud. In IoT terms, these smart contracts can automate interactions between devices, such as automatically ordering a new part when a sensor detects malfunctioning. [4] IoT systems supported by blockchain can reduce the possibility of hackers to attack the system, significantly increasing the trust of all the parties involved, thus providing us with a robust IoT solution for securing IoT networks and data.
2.3. Artificial Intelligence and Machine Learning
AI and ML also play a significant role in IoT security as they enable both real-time threat detection and response. These technologies can analyse the large data streams generated by IoT devices to detect anomalies that might indicate potential security threats. For example, ML algorithms trained on historical data can detect the normal operating patterns of industrial machinery and when anomalies occur that might indicate a cyber-attack or mechanical failure. AI-based security systems can also adapt and evolve based on new threats, facilitating better, more dynamic cybersecurity. For example, a neural network-based IDS can learn from new data and improve its ability to detect increasingly sophisticated attacks [5]. Anomaly detection algorithms can detect unusual behaviour in IoT devices such as unexpected data transmissions or unauthorised access attempts, and generate alerts or automatic responses. The adoption of AI and ML in IoT security systems improves the ability to protect against new threats, enabling the continuous protection of sensitive data within IoT ecosystems.
3. Challenges in Privacy Protection
3.1. Data Overload and Privacy Management
Because of its exponential growth, IoT now generates an enormous amount of data. It needs to be processed and stored. Ensuring the privacy of IoT users is a complex challenge. IoT devices are used to collect private information, such as personal health data, precise locations at all times, and behavioural patterns. If this data is not appropriately protected, it can be used to harm individuals. For instance, smart home devices can track a user’s daily routines, and if an attacker could access this data, they could use it to break into homes or target users when they are most vulnerable [6]. Conventional approaches to data management might not be adequate to deal with the size and complexity of IoT data. Privacy management requires data governance, such as randomisation, controls on data transfer, and regular audits of data flows to make sure that sensitive information is well protected from unauthorised access and misuse. Data randomisation relies on techniques like k-anonymity and differential privacy, which can protect the identity of individuals so that it cannot be traced back to them [7]. Enforcing strict access controls and conducting regular security audits can further improve data protections and make sure they comply with the privacy regulation requirements.
3.2. Regulatory and Compliance Issues
IoT security and privacy regulatory landscape is constantly changing; different regions have different standards and requirements, which is challenging to navigate for an organisation that operates in multiple jurisdictions. Ensuring compliance with the General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA) and other regional privacy laws, is necessary for any organisation that collects information from individuals. Figure 1 represents the compliance measures and penalties for various IoT security and privacy regulations. GDPR is a strict regulation with heavy penalties for non-compliance, so it requires organisations to take measures such as data encryption, DPIA, and breach notification. For example, GDPR mandates that organisations do all they can to ensure the safety of stored personal data. If they don't, they can be slapped with a hefty fine and serious reputational consequences [8]. Organisations caught in non-compliance can face up to €20,000,000 or 4% of total annual turnover. Therefore, it is imperative for organisations to ensure that their IoT systems comply with these regulations to avoid any cost. They should develop a strategy for compliance, which includes regular training of employees on new regulations, continuous monitoring of regulatory changes, and seeking advice from legal experts.
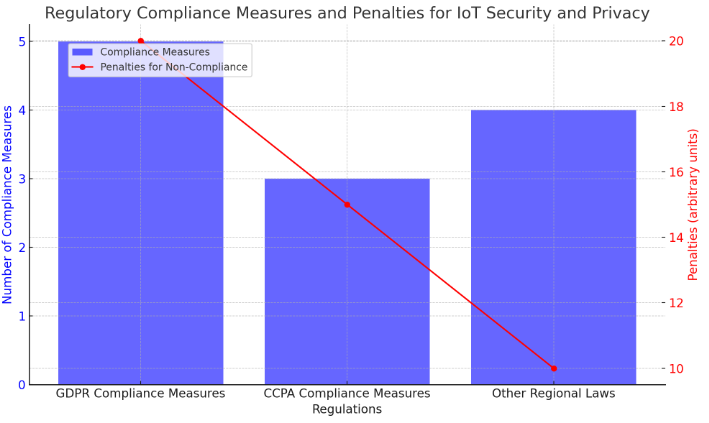 Figure 1. Regulatory Compliance Measures and Penalties for IoT Security and Privacy
Figure 1. Regulatory Compliance Measures and Penalties for IoT Security and Privacy
3.3. Security Vulnerabilities in IoT Devices
The limited computing power and storage of these devices puts limitations on the type of security protection that can be implemented. Many IoT devices may not have hardware-enforced secure boot mechanisms, which can allow attackers to install malicious firmware instead of the legitimate firmware. Without such a mechanism, an IoT device cannot fully trust its own firmware, leaving it vulnerable to data breaches and malware infections. IoT ecosystems are also diverse, ranging from sensors to smart appliances. Smart appliances (eg, a smart TV) are typically more complex than simple sensors (eg, a smoke detector). As devices become more complex, the opportunities for attacks that exploit vulnerabilities increase. For example, a smart TV can be hacked by attackers who can manipulate settings and steal user data. Such devices also have the potential to be used as instruments in botnets or other distributed attacks that target websites and other resources [9]. For IoT devices to become truly secure, better security is needed in three main areas: secure device design, secure firmware updates and authentication.Secure device design must be included from the beginning of the manufacturing process. Manufacturers and developers must incorporate the best practices when designing their products, from the software code to the hardware, to protect against vulnerabilities. Sensitive data generated by IoT devices should be encrypted during transmission and at rest to prevent misuse or unauthorised access. The firmware running the hardware needs to be kept up to date by manufacturers and developers through regular updates [10].
4. Strategies for Enhancing Privacy Protection
4.1. Implementing Strong Encryption Protocols
Strong encryption protocols can be implemented at all stages of communication to protect the privacy of data flowing through an IoT device. This is called end-to-end encryption. It assures that the data is encrypted at the source and remains so throughout the communication chain until it reaches the destination. For example, end-to-end encryption can be implemented to secure data communication between a smart thermostat and the cloud server. It allows any temperature setting and usage pattern in the thermostat to remain confidential since the data remains encrypted throughout its route from the thermostat to the cloud server. It is also important to protect data in transit so that it cannot be intercepted or manipulated in the middle. This can be done by using secure encrypted communication protocols such as Transport Layer Security (TLS). The TLS protocol is widely used to secure communications on the web, providing confidentiality and integrity of data that is transmitted between a web browser and the web server. Organisations should always use encryption standards set by the most recent guidelines [11]. They should also regularly review and update the encryption protocols to account for changes in the landscape of emerging threats and vulnerabilities. It is important to conduct security audits and keep yourself updated on the latest emerging technologies to ensure effective IoT privacy protection. Figure 2 below represents the implementation of strong encryption protocols in IoT privacy protection.
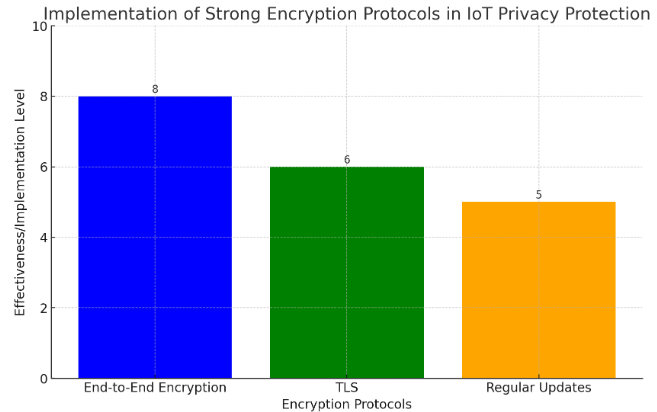 Figure 2. Implementation Of Strong Encryption Protocols In IoT Privacy Protection
Figure 2. Implementation Of Strong Encryption Protocols In IoT Privacy Protection
4.2. Adopting Privacy by Design Principles:
Privacy by Design (PbD) starts by putting privacy considerations at the forefront of the design and implementation of products and services right from the beginning. Embedding privacy features in the design of IoT systems can help to minimise privacy risks throughout the lifecycle of those systems by addressing privacy risk at the design stage. Some of the PbD principles include: data minimisation, meaning that only the required data is collected and processed; and user consent, where the users are informed about how their data will be collected and processed and provide consent for such data collection and processing activities. A PbD IoT health monitoring system can collect only the data required for monitoring the vital signs and provide the users with clear choices for consenting to data collection and processing. Implementing PbD principles helps to establish trust with the users and demonstrate that the organisation is protecting and respecting privacy. Organisations can further enhance privacy protection and compliance with laws and regulations by engaging in transparent data practices, providing the users with control over their data, and conducting regular PIAs. [12]
5. Conclusion
It is important to say that the computer technology and the Internet of Things integration is bringing great innovations, opportunities, but also important challenges in term of privacy protection. This work has explored the innovations brought by IoT security, such as the end to end encryption, the blockchain technology and the artificial intelligence solutions, and has also pointed out the critical challenges affecting privacy protection, such as the data overload with concurrent security requirements, the regulatory compliance and the vulnerabilities of the devices. In order to face the challenge of IoT security and privacy protection, companies should implement strong security measures, should adopt the Privacy by Design principles and should improve the awareness of the users with the aim to protect user’s privacy, to avoid the security breaches and to build trust over IoT technology. The constant evolution of IoT, the growing number of attacks, the new possible security breaches will bring continuous research and in depth knowledge, together with the collaboration with different stakeholders in order to develop effective solutions and to protect the IoT ecosystems, that are more and more important in our daily life. The constant monitoring of the new threats, the constant update of the regulations and a proactive attitude in term of privacy protection could be very important to maintain the security and integrity of the IoT ecosystems in a world that is more and more connected.
References
[1]. Sarker, Iqbal H., et al. "Internet of things (iot) security intelligence: a comprehensive overview, machine learning solutions and research directions." Mobile Networks and Applications 28.1 (2023): 296-312.
[2]. Chawla, Diksha, and Pawan Singh Mehra. "A survey on quantum computing for internet of things security." Procedia Computer Science 218 (2023): 2191-2200.
[3]. Taherdoost, Hamed. "Security and internet of things: benefits, challenges, and future perspectives." Electronics 12.8 (2023): 1901.
[4]. Bazgir, Ehsan, et al. "Security aspects in IoT based cloud computing." World Journal of Advanced Research and Reviews 20.3 (2023): 540-551.
[5]. Ahmid, Maroua, and Okba Kazar. "A comprehensive review of the internet of things security." Journal of Applied Security Research 18.3 (2023): 289-305.
[6]. Amoo, Olukunle Oladipupo, et al. "Cybersecurity threats in the age of IoT: A review of protective measures." International Journal of Science and Research Archive 11.1 (2024): 1304-1310.
[7]. Rodríguez, Eva, Beatriz Otero, and Ramon Canal. "A survey of machine and deep learning methods for privacy protection in the internet of things." Sensors 23.3 (2023): 1252.
[8]. Murugeshwari, B., et al. "Data Mining with Privacy Protection Using Precise Elliptical Curve Cryptography." Intelligent Automation & Soft Computing 35.1 (2023).
[9]. Brauneck, Alissa, et al. "Federated machine learning, privacy-enhancing technologies, and data protection laws in medical research: scoping review." Journal of Medical Internet Research 25 (2023): e41588.
[10]. Oyewole, Adedoyin Tolulope, et al. "Data privacy laws and their impact on financial technology companies: a review." Computer Science & IT Research Journal 5.3 (2024): 628-650.
[11]. El-Haggar, Nahla, et al. "The effectiveness and privacy preservation of IoT on ubiquitous learning: Modern learning paradigm to enhance higher education." Applied Sciences 13.15 (2023): 9003.
[12]. Paul, Metty, et al. "Digitization of healthcare sector: A study on privacy and security concerns." ICT Express 9.4 (2023): 571-588.
Cite this article
Li,Z. (2024). Navigating the intersection of computer technology and IoT: Innovations, challenges, and strategies for privacy protection. Applied and Computational Engineering,102,24-29.
Data availability
The datasets used and/or analyzed during the current study will be available from the authors upon reasonable request.
Disclaimer/Publisher's Note
The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of EWA Publishing and/or the editor(s). EWA Publishing and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content.
About volume
Volume title: Proceedings of the 2nd International Conference on Machine Learning and Automation
© 2024 by the author(s). Licensee EWA Publishing, Oxford, UK. This article is an open access article distributed under the terms and
conditions of the Creative Commons Attribution (CC BY) license. Authors who
publish this series agree to the following terms:
1. Authors retain copyright and grant the series right of first publication with the work simultaneously licensed under a Creative Commons
Attribution License that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this
series.
2. Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the series's published
version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial
publication in this series.
3. Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and
during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work (See
Open access policy for details).
References
[1]. Sarker, Iqbal H., et al. "Internet of things (iot) security intelligence: a comprehensive overview, machine learning solutions and research directions." Mobile Networks and Applications 28.1 (2023): 296-312.
[2]. Chawla, Diksha, and Pawan Singh Mehra. "A survey on quantum computing for internet of things security." Procedia Computer Science 218 (2023): 2191-2200.
[3]. Taherdoost, Hamed. "Security and internet of things: benefits, challenges, and future perspectives." Electronics 12.8 (2023): 1901.
[4]. Bazgir, Ehsan, et al. "Security aspects in IoT based cloud computing." World Journal of Advanced Research and Reviews 20.3 (2023): 540-551.
[5]. Ahmid, Maroua, and Okba Kazar. "A comprehensive review of the internet of things security." Journal of Applied Security Research 18.3 (2023): 289-305.
[6]. Amoo, Olukunle Oladipupo, et al. "Cybersecurity threats in the age of IoT: A review of protective measures." International Journal of Science and Research Archive 11.1 (2024): 1304-1310.
[7]. Rodríguez, Eva, Beatriz Otero, and Ramon Canal. "A survey of machine and deep learning methods for privacy protection in the internet of things." Sensors 23.3 (2023): 1252.
[8]. Murugeshwari, B., et al. "Data Mining with Privacy Protection Using Precise Elliptical Curve Cryptography." Intelligent Automation & Soft Computing 35.1 (2023).
[9]. Brauneck, Alissa, et al. "Federated machine learning, privacy-enhancing technologies, and data protection laws in medical research: scoping review." Journal of Medical Internet Research 25 (2023): e41588.
[10]. Oyewole, Adedoyin Tolulope, et al. "Data privacy laws and their impact on financial technology companies: a review." Computer Science & IT Research Journal 5.3 (2024): 628-650.
[11]. El-Haggar, Nahla, et al. "The effectiveness and privacy preservation of IoT on ubiquitous learning: Modern learning paradigm to enhance higher education." Applied Sciences 13.15 (2023): 9003.
[12]. Paul, Metty, et al. "Digitization of healthcare sector: A study on privacy and security concerns." ICT Express 9.4 (2023): 571-588.









