

Volume 197
Published on October 2025Volume title: Proceedings of the 7th International Conference on Computing and Data Science
This paper establishes a mathematical model based on the initial position and trajectory of enemy missiles, the positions of our real and decoy targets, the initial position of drones, the number of smoke grenades carried, deployment and detonation timing, and drone allocation. The model aims to find a global optimal solution to enhance the effective coverage duration of smoke clouds and improve drone combat effectiveness. For Problem 1, we first establish mathematical models for drone deployment of smoke interference grenades for enemy missiles M1, drones MY1, real targets, and decoy targets. Subsequently, we calculate their positions at any moment using relevant motion models. Finally, through a line-of-sight (LOS) occlusion model, real targets are abstracted into 16 test points to determine whether missile line-of-sight can be effectively occluded at any moment. The effective coverage duration is calculated by subtracting the initial and final times of effective occlusion. For Problem 2, we first define approximate ranges for four parameters: FY1's flight direction, speed, smoke interference grenade deployment point, and detonation point. We then narrow these parameter ranges using binary search and iteratively solve the objective function for these four parameters using an Evolutionary Search Genetic Algorithm (ESGA) optimized with an early termination mechanism. Genetic algorithm operations identify the maximum effective occlusion duration, with fitness analysis and patience value comparison used to determine whether early termination is necessary to avoid local optima. Finally, sensitivity analysis is conducted using differential evolution and particle swarm optimization models to verify solution accuracy after accounting for uncertain factors.

 View pdf
View pdf


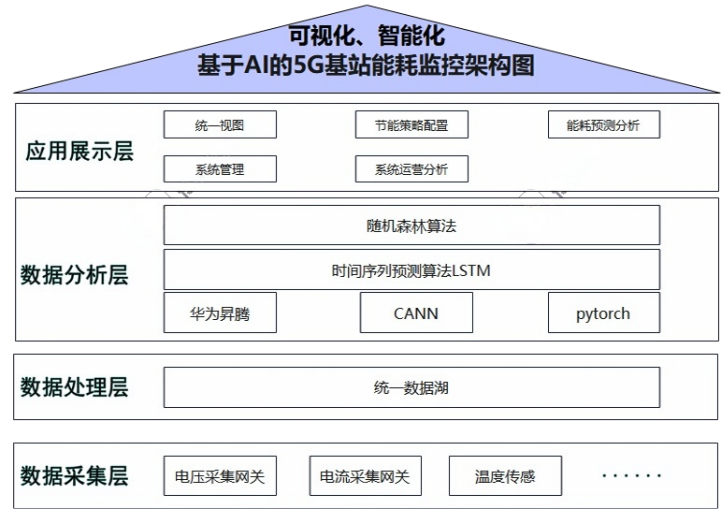
This paper addresses the issue of energy consumption management in 5G base stations and proposes a solution in the form of an AI-based energy supervision cloud platform. Leveraging cloud computing and artificial intelligence technologies, the platform enables real-time monitoring, intelligent analysis, and optimized control of 5G base station energy consumption. By analyzing the characteristics of 5G base station energy use and supervisory requirements, the overall architecture and key modules of the platform are designed. The platform employs deep learning for energy consumption prediction and anomaly detection, and integrates reinforcement learning to achieve energy-saving control. Experimental results indicate that the platform effectively reduces energy consumption in 5G base stations, improves energy utilization efficiency, and provides strong support for the green and sustainable development of 5G networks.

 View pdf
View pdf


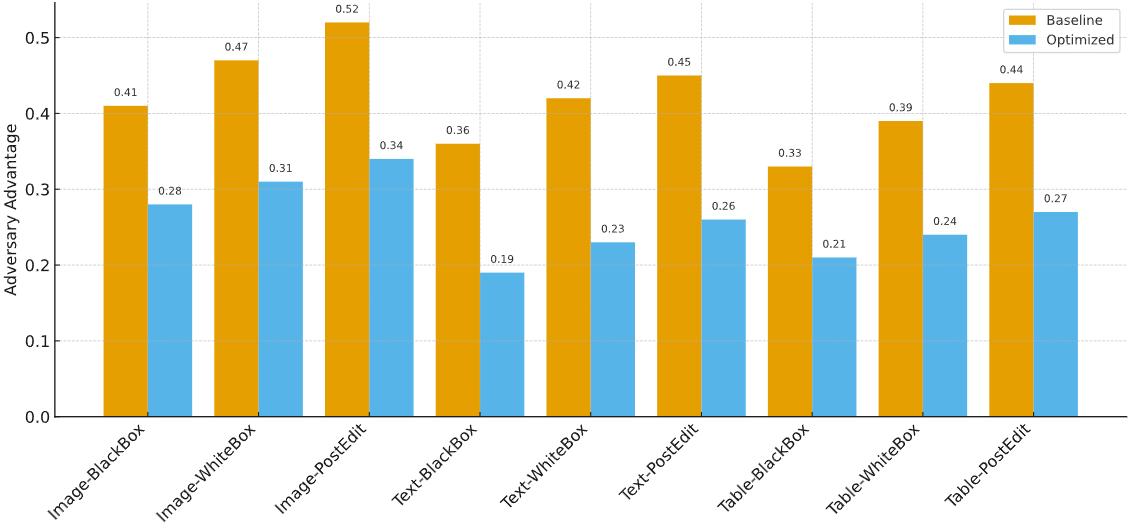
Synthetic data has become a vital component in AI training and data governance, addressing challenges of data scarcity and regulatory compliance while introducing new concerns regarding security and controllability. A central tension arises between privacy protection and traceability, membership inference attacks can exploit model output differences to infer the presence of individual records in training data, leading to privacy leakage, while watermarking mechanisms provide traceability but often compromise task utility through embedding strength and robustness. To resolve this conflict, this study proposes a joint design framework that integrates adversary-advantage–based resistance metrics with verifiable watermarking, optimized through a multi-objective paradigm to enable coordinated training of generators and watermark embedders. Experiments conducted on CIFAR-10, CelebA, IMDB, and UCI Adult datasets demonstrate that the framework significantly reduces membership inference risks under black-box, white-box, and post-editing attacks, with an average reduction of approximately 30% in adversary advantage, while maintaining over 95% watermark detection accuracy and less than 2% utility loss. These findings validate the feasibility of achieving a dynamic balance among privacy resistance, traceability, and data quality through joint optimization, establishing a unified evaluation protocol and practical governance pathway, with significant implications for the trustworthy deployment of synthetic data in research and industry.

 View pdf
View pdf


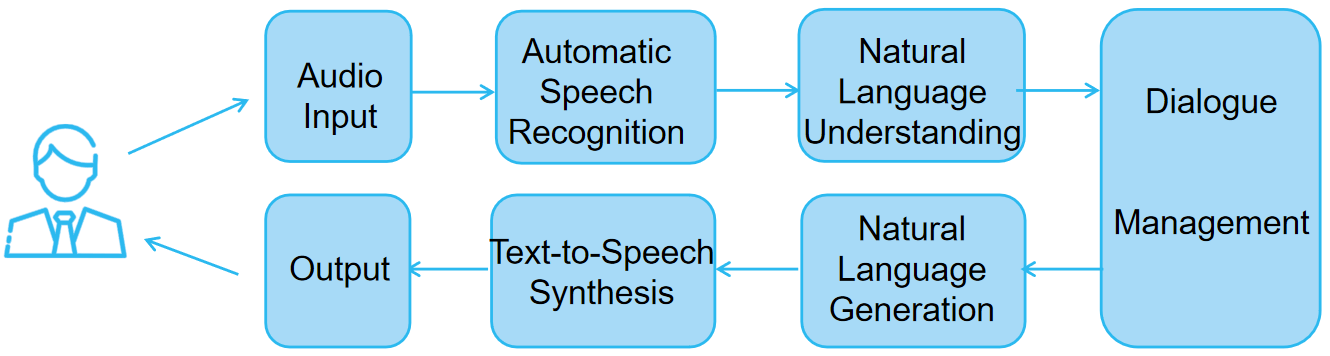
Intelligent speech assistants, as a representative application of artificial intelligence and big data, have been widely adopted in domains such as mobile devices, smart homes, education, and healthcare. This paper presents a comprehensive survey of recent research on speech assistants, focusing on their core architectures, key technologies (automatic speech recognition, natural language understanding, dialogue management, and text-to-speech), and representative application scenarios. The challenges of privacy protection, multilingual support, personalization, and low-resource optimization are also analyzed. To further demonstrate the practical aspects of speech assistants, we implement a lightweight prototype for weather query based on speech recognition, natural language processing, and text-to-speech synthesis. Experimental results show that the prototype can effectively support real-time user interaction, which verifies the feasibility of combining big data services with intelligent assistants. Finally, future research directions are discussed, including integration with large language models, multimodal interaction, and edge-cloud collaboration. This study provides both a systematic literature review and an exploratory case study, offering insights for the development and optimization of speech assistant systems in the era of big data.

 View pdf
View pdf


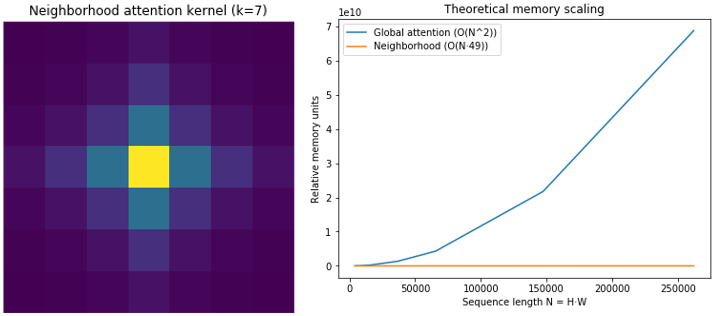
Edge detection remains a foundational operation in computer vision pipelines, yet the community still grapples with the trade-off between accuracy, crisp localization, and computational efficiency. Convolutional networks excel at local gradient modeling but struggle to maintain global coherence without heavy multi-scale designs, while global self-attention achieves long-range reasoning at quadratic cost. We present EdgeNAT, a Transformer-based edge detector that integrates neighborhood attention with dynamic multi-scale tokenization to realize strong boundary sharpness at markedly lower compute and memory requirements. EdgeNAT employs a lightweight convolutional stem for gradient-preserving tokens, a pyramid of Neighborhood Attention Transformer (NAT) blocks with dilated neighborhoods to enlarge the receptive field without quadratic complexity, and a decoder with deep supervision aligned to boundary thickness. Theoretically, EdgeNAT reduces the attention complexity fromO(N2)toO(N⋅M)with neighborhood sizeM≪N, which translates into consistent efficiency gains for high-resolution imagery. We further introduce a composite loss that couples balanced cross-entropy with a Dice consistency term to discourage thick or fragmented boundaries. Analyses and ablations against recent journal models suggest that EdgeNAT occupies a favorable Pareto region for accuracy–efficiency in edge tasks and boundary rendering. We also provide theoretical complexity profiles and visualizations that clarify how neighborhood size controls the compute–accuracy frontier. Collectively, these results indicate that locality-biased attention with gradient-aware tokens is a principled and practical design for fast, crisp, and transferable edge detection.

 View pdf
View pdf




