1. Introduction
Nowadays, cybersecurity technologies are employed in the cutting-edge development and implementation in a range of spheres of social life, becoming an important mean to protect information and privacy [1]. With the acceleration of digital transformation, cybersecurity technology is widely used in various industries such as finance, healthcare, manufacturing, and energy to protect sensitive data, maintain system integrity, and prevent malicious attacks. The introduction of technological innovations such as artificial intelligence used in cloud, big data, Internet of things, artificial intelligence and nanotechnology, also accelerate the adoption of cybersecurity technology [2]. Meanwhile, information technology advancements also have had a significant impact on communications and business transactions between companies and their customers and suppliers [3]. Ginni Rometty, Chairman and CEO of IBM, made the following observation in that regard, data is a contemporary phenomenon [4].
However, with rapid development of digital transformation and rapidly utilization of Internet, network security issues are becoming one of the most significant and rapidly evolving issues in the modern world [5]. With the rising frequency and complexity of cyberattacks, various types of assaults such as data breaches, ransomware, distributed denial of service (DDoS) attacks, constitute a substantial threat to individuals, organizations, and government agencies [6-8]. Simultaneously, the legal and compliance obligations for cybersecurity are becoming increasingly strict and enterprises are experiencing increased pressure to guarantee data security and privacy protection.
Based on several studies which examines the financial health and market position of companies in cybersecurity domain, this study analyzes four prominent companies within the cbersecurity sector: Check Point Software Technologies Ltd. (CHKP), Qualys Inc. (QLYS), Rapid7 Inc. (RPD), and Gen Digital Inc. (GEN). In cybersecurity domain, CHKP is a pioneer recognized for its all encompassing threat-protection solutions [9]. For example, it could be an alternative to control lists in modern network security [10]. Due to its robust production line and lengthy history, CHKP has established its name in this industry. By contrast, QLYS is a global leader in cloud security and compliance solutions, providing businesses protect IT environment. Moreover, it greatly contributes to ACCESS project for enhance cybersecurity [11]. RPD focuses on IT analysis and automation to provide solutions, and its Nexpose vulnerability analysis has made great job in tax administration [12]. In terms of GEN, formerly called Symantec Corporation and NortonLifeLock, is a multinational software company which specializes in digital identity protection and cybersecurity products. Consequently, this study will examine the financial performance of four top cybersecurity firms. To better understand the network security industry, financial data will be used to analyze their market performance and growth potential.
This study aims to provide a comprehensive analysis of CHKP compared to QLYS, RPD and GEN. Through comparing key financial factors, this study will reveal their advantages and disadvantages on their financial performance. The framework for this part is given as following. The Sec. 2 gives the sources of the data, selected companies and reasons for selection, methods for comparison. The Sec. 3 presents comparison analysis, explanation and implications, limitation and prospects. Eventually, a conclude remark is presented in Sec. 4.
2. Data and Method
The primary data for this study originates from financial database, academic publications and company financial statement. Financial database provides historical financial record, basic financial index and comprehensive market analysis, playing a pivotal role in financial analysis. According to this information, it is possible to delve into financial trends over a specific time and provide a solid basis for comparative analysis. Meanwhile, academic publications and company financial statement also can provide information about valuable insights and background, contributing a deeper understanding of financial data. The combination of financial database, academic publications and company financial information guarantees the comprehensiveness and detail of the study. This study selected the following four companies with an important position in the field of cybersecurity for analysis.
Check Point Software Technologies (CHKP) is a prominent player in the cybersecurity sector, boasting a lengthy history in this field. CHKP distinguishes itself in the competitive market and has gained customer trust and industry recognition due to its extensive and strong security solutions and exceptional defense capabilities. Simultaneously, its wide range of products and services covers various essential domains, effectively catering to the intricate requirements of diverse network security users, and consistently upholding a crucial role in safeguarding the security and stability of the network environment. QLYS has gained significant prominence in the market as a vulnerability management solution due to its comprehensive and integrated features, scalability, flexibility, real-time monitoring, early warning capabilities, and widespread acceptance by many enterprises. QLYS is a formidable competitor in the field of cyber security due to the importance of vulnerability management in this context. RPD specializes in the automation and analysis of security, providing tools to improve security operations. The company gains a competitive edge by utilizing its automation capabilities and making strategic acquisitions. GEN has a lengthy historical background and was previously known as Symantec. The company offers a diverse array of cyber security solutions, including endpoint security and identity protection. Furthermore, in order to accommodate changes in the market, the company has experienced substantial rebranding and strategic modifications. The selection of these four companies was based on their substantial market presence and leadership in the cybersecurity sector. Each company has a unique strategic approach and product focus that accurately reflect the industry's development trends and competitive landscape.
This study conducted an analysis of the financial data from the years 2019 to 2024 for the following four companies. This period enables a thorough evaluation of the company's financial performance in various market situations and economic circumstances, considering both immediate and long-lasting patterns. Examining data from this period can reveal how recent market events, economic conditions, and strategy decisions affected organizations, revealing their financial health and operational effectiveness.
This study employs the subsequent financial indicators and measurements to evaluate the financial performance of the four companies:
• Earnings Per Share (EPS) = (Net Income - Dividends on Preferred Stock) / Average number of shares, which is used to measure the company's profitability.
• EPS growth rate= (NTM EPS - TTM EPS)/TTM EPS*100%, which indicates the growth trend of the company's earnings.
• Price to Earnings (P/E) Ratio = Market Price per Share / Earnings per Share, a way to assess the market's valuation level of the company.
• Price/Earnings to Growth (PEG) Ratio= (P/E) EPS growth rate, which is utilized to comprehensively evaluate the extent to which a company's valuation correlates with its potential for growth.
• Gross Profit Margin = (Gross Profit / Revenue) * 100%, which reflects the company's capacity to control costs and maximize profitability with respect to its products or services.
• Net Profit Margin = (Net Income/ Revenue) *100%, which can further measure the company's profitability.
• Gross Profit to Assets (GP/A) ratio = (Gross Profit / Total Assets)*100%, which can evaluate the utilization efficiency and profitability of the company's assets.
The performance of each company's financial status, profitability, growth potential, market valuation, and asset utilization efficiency can be comprehensively evaluated through the comprehensive application and analysis of these indicators, thereby providing a strong foundation for investment decisions.
3. Results and Discussion
In-depth analyses of the financial data of Check Point Software Technologies (CHKP), Qualys (QLYS), Rapid7 (RPD), and Gen Digital (GEN) offer a comprehensive perspective on their competitive position and performance in the cybersecurity industry. This stage is designed to analyze the prospective impact of each company's financial performance on investment decisions, interpret the meaning behind the data, and investigate the financial performance of each company. The subsequent section of the study will provide a detailed analysis of the results of a variety of financial indicators in order to elucidate the competitive position and investment potential of these companies in the cybersecurity sector.
3.1. Comparison Analysis
A summary of the indicators for four companies are presented in Table 1. The stock prices of CHKP are $156.41, QLYS is $136.02, RPD is $37.64, and GEN is $24.72, based on the latest data. These prices reflect estimates of the companies' financial performance and development potential made by the market. CHKP and QLYS have significantly higher stock values than RPD and GEN, which indicates more market confidence.
Table 1: Indicators for the four selected companies.
Company name |
CHKP |
QLYS |
RPD |
GEN |
Stock price |
$156.41 |
$136.02 |
$37.64 |
$24.72 |
TTM EPS |
8.68 |
5.63 |
1.95 |
1.96 |
NTM EPS |
9.3 |
5.24 |
2.17 |
2.21 |
TTM P/E |
18.02 |
24.16 |
19.30 |
12.61 |
NTM P/E |
16.82 |
25.96 |
17.35 |
11.19 |
Revenue growth rate |
6.0% |
8.7% |
6.1% |
2.6% |
EPS growth rate |
7.1% |
-6.9% |
11.3% |
12.8% |
PEG |
2.52 |
N/A |
1.71 |
0.99 |
GP/A |
37.4% |
55.0% |
36.3% |
19.5% |
With a trailing twelve-month (TTM) EPS of 8.68, CHKP is ahead of QLYS (5.63), RPD (1.95), and GEN (1.96). The NTM (Next Twelve Months) EPS forecasts show a similar trend, with CHKP expected to reach 9.3, QLYS at 5.24, RPD at 2.17, and GEN at 2.21, indicating that CHKP would maintain its position as the industry leader in profitability. NTM and TTM P/E ratios are critical for determining how the market values these companies in terms of earnings. CHKP has a TTM P/E of 18.02 and an NTM P/E of 16.82, indicating a steady valuation. Despite its lower present profitability, QLYS has higher ratios of 24.16 (TTM) and 25.96 (NTM), indicating greater market expectations for future growth. However, RPD and GEN have lower P/E ratios, reflecting differing market perceptions and potentially larger perceived risks. Revenue growth rates and EPS growth rates are essential for evaluating the companies' potential for future expansion. QLYS shows the highest revenue growth rate at 8.7%, followed by RPD at 6.1%, CHKP at 6.0%, and GEN at 2.6%. Interestingly, QLYS has a negative EPS growth rate of -6.9%, suggesting challenges in converting revenue growth into profitability. In contrast, RPD demonstrates strong EPS growth at 11.3%, indicating effective cost management and operational efficiency. GEN also shows a positive EPS growth rate of 12.8%, while CHKP has a modest growth rate of 7.1%.
Revenue growth rate and EPS growth rate are key metrics to evaluate company potential for future expansion. QLYS possesses the highest revenue growth rate, with 8.7%, followed by RPD, CHKP and GEN with 6.1%, 6.0% and 2.6%, respectively. Despite its strong revenue growth, QLYS has a negative EPS growth rate with -6.9%, suggesting difficulties in converting its revenue growth into its profitability. This also indicates QLYS may invest a great deal of capital in its growth initiatives, contributing to higher costs. In contrast, RPD demonstrates strong EPS growth at 11.3%, indicating effective cost management and operational efficiency. Such balance between revenue growth and profitability makes RDP an energetic participant in cybersecurity domain. Despite its moderate revenue growth, GEN exhibits the greatest EPS growth rate of 12.8%, indicating an excellent profit conversion from its revenue. With a 7.1% EPS growth rate and a 6.0% revenue growth rate, CHKP is growing steadily, which is consistent with its well-established market position and extensive threat-protection offerings.
The PEG ratio evaluates a stock's valuation and growth prospects by combining the P/E ratio and predicted growth rate. It is notable that CHKP possesses the highest figure with 2.52, indicating a relatively balanced valuation according to its growth. The negative figure of QLYS shows that it lacks meaningful PEG ratio. By contrast, GEN has the lowest PEG ratio with 0.99, showing that it might be undervalued. The value for RPD is 1.71, indicating relatively positive growth potential. GP/A ratio reflects the efficiency of asset utilization. The data shows that QLYS leads the other three companies at 55.0%, indicating its high efficiency in generating gross profit from its assets. CHKP and RPD follow at 37.4% and 36.3%, respectively, also suggesting solid asset utilization from its gross profit margin. Nevertheless, despite its robust EPS growth, a 19.5% GP/A ratio shows the low efficiency in asset utilization, suggesting that measures should be taken to improve this condition.
3.2. Explanation and Implications
The following financial data in Fig. 1 highlights key insights into the performances of these cybersecurity firms. The financial performance data provide a comprehensive insight on the following three most important aspects, operating efficiency, profitability and valuation index of each company. Gross profit margin is a key indicator to measure the operating efficiency of a company. From the tables and line graphs, it is clear that CHKP has consistently high gross profit margins, showing its outstanding ability on cost management and operating performance. Such excellent ability can make CHKP more competitive especially in such fierce market. Meanwhile, QLYS also exhibits a positive trend, indicating its improvement on management efficiency and pricing strategy. However, RPD lags its rivals, showing that there should be more improvement on its cost management or pricing strategy. As for GEN, there is a notable decline, indicating that external factors have been greatly influenced this company and measures should be taken to sustain its profitability. Net profit margin is a significant indicator to exhibit profitability of one company. It is shown from the graphs that CHKP and QLYS have consistently high net gross margins, indicating its strong profitability and effective cost management. By contrast, RPD experienced a negative trend and great fluctuations, indicating its unpredictable profitability and notable difficulties in operation. In terms of GEN, it also performed badly, witnessing a notable decrease, peaking in 2019 and dropping to its lowest point in 2023. This phenomenon also indicates that GEN has serious problems in its profitability and it is necessary to take measure to change strategies for recover its economy. GP/A ratio provides pivotal information on asset utilization. Overall, QLYS has relatively high GP/A ratio, indicating its excellent ability in operating management and high efficiency in asset utilization. These figures may attract more investors due to its high capital return. Meanwhile, CHKP and RPD witnessed an increasing trend in GP/A ratio, indicating its better asset utilization over time. However, GEN has an extremely low GP/A, indicating that this company should find some methods to improve its operations.
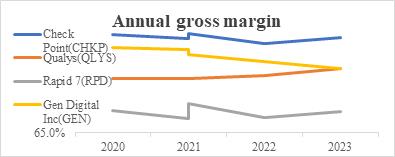
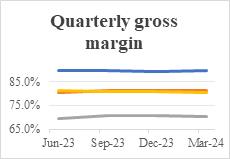
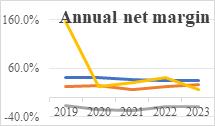
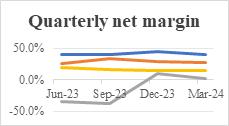
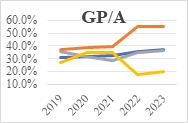
Figure 1: Annual gross margin, quarterly gross margin, annual net margin and GP/A for four selected company.
According to the financial data, the investment implications for each company can be summarized as follows. Based on overall performance, CHKP is the most reliable and steady investment. Its consistently high net and gross profit margins indicates CHKP is more competitive in cost management, pricing strategies and profitability. The GP/A ratio demonstrates its exceptional capacity to balance the usage of assets and profitability. Even though its PEG ratio is relatively high with 2.52, it possesses robust profitability and relatively low P/E ratio, indicating its potential in earning growth. Therefore, CHKP can be especially appealing investment for conservative investors who prioritize stability and consistency over high-risk, high-reward opportunities. The advantages of QLYS are its high gross profit margin and robust revenue growth rate, indicating its robust competitiveness and potential in cybersecurity domain. However, its low net profit margin (27.3% in 2023) and negative EPS growth rate (-6.9%) exhibits that there are some issues in profitability. Furthermore, its high TTM and NTM P/E ratio makes it less attracting, indicating a higher risk in investment. Therefore, even though QLYS possesses its advantages, its weaknesses in profitability and valuation makes it not an ideal investment. RPD has a relatively competitive EPS growth rate (11.3%) and rational GP/A ratio (36.3%), indicating its potential in this domain. However, its consistently negative net profit margin (-19.2% in 2023) and great fluctuations in its quarterly net profit margin reflects its deficiencies in profitability. Furthermore, the TTM and NTM P/E ratio of RPD is relatively high, indicating higher risks in investment. Therefore, despite the growth potential, its consistently losses and high valuations makes it the worst investment. With a PEG ratio of 0.99, GEN may be undervalued and its growth potential may not be fully appreciated by the market. However, investors should be wary because the company's net margins and declining GP/A ratio show that it is having major problems with profitability. There is a possibility of a turnaround if the company can improve asset utilization and address its operational inefficiencies. If the company successfully implements strategic reforms to enhance performance, GEN could be a high-risk, high-reward scenario for risk-averse investors.
3.3. Limitations and Prospects
There are several limitations of the study. Firstly, the study relies on financial data from 2019-2024, which may limit its ability to fully capture long-term trends and cyclical patterns. While this study offers comprehensive information for the current period, it may overlook historical performance characteristics that could provide valuable insights into the financial health and strategic posture of these organizations. Secondly, the study extensively employs quantitative financial measurements, including net and gross margin, EPS ratios, and P/E ratios. While these data offer valuable insights into the performance of each organization, they do not encompass important information such as managerial efficiency, brand strength, customer contentment, and innovative capabilities. Qualitative elements, which are not shown in financial accounts, can have a significant impact on a company's long-term performance. Thirdly, the cybersecurity environment is constantly evolving, with threats perpetually shifting and technology progressing rapidly. The user's text is a single letter "F". This study does not take into account any future occurrences that could significantly influence the competitive environment, such as emerging cybersecurity risks, legislative modifications, or technology breakthroughs. Hence, the outcomes may lack practicality in forecasting future performance beyond the duration of the study. Lastly, the study specifically examines four companies: CHKP, QLYS, RPD, and GEN. Although these organizations play a crucial role in the cybersecurity sector by offering various strategic approaches, this study is limited in its analysis due to the lack of inclusion of other prominent competitors.
Although there are limitations as discussed earlier, the outlook for the cybersecurity industry remains optimistic. The increasing importance of digital security, along with the rising occurrence of cyber-attacks, emphasizes the necessity for cyber security solutions to safeguard vital data. The anticipated growth in this pattern is projected to drive a continuous need for sophisticated cybersecurity solutions and services, which will be advantageous for companies such as CHKP, QLYS, RPD, and GEN. CHKP has consistently capitalized on the increasing demand for its complete cybersecurity solutions due to its robust market position, steady growth, and consistently excellent profit margins. Nevertheless, the company's wide range of products and efficient operational management are promising indications of its continued dominance in the industry in the future. QLYS exhibits strong development potential due to its rising profitability and efficient utilization of assets. The emphasis on real-time analysis and cloud-based security aligns perfectly with the current industry trends of cloud adoption and enhanced threat detection, laying the foundation for future success. RPD's strong growth potential, as demonstrated by its PEG ratio and rising financial measures, suggests that it is heading in the right direction. Nevertheless, in order to completely achieve its maximum capability, organizations must surmount fluctuations in profitability. The potential to improve its competitive position is present due to the ongoing innovation in IT security analysis and automation. Despite profitability issues, GEN is cheap and has the potential for operational improvement, making it a high-risk, high-return investment. Strategic asset use and cost management can boost turnaround chances. In terms of GEN, even though it is cheap and has potential to improve its operations, it still is a high-risk, high return investment. If this company follows excellent strategic asset utilization and cost management, it may enhance the profitability of turnaround.
4. Conclusion
To sum up, the study analyses four prominent companies in cybersecurity domain, which are CHKP, QLYS, RPD and GEN, respectively. According to comparison data, it is evident that CHKP has better performance on investment return compared to the other three companies due to its consistently high net profit margins and stable performance on profitability. Meanwhile, its effective control, diversified product offerings and strategic market position makes it keeping robust financial condition and providing stable return to investors. However, due to various factors, QLYS, RPD and GEN have consistently lower competition in this field. With increasing cyber-attacks and growing significance of digital security, cybersecurity is becoming more and more important in future life. Therefore, a comprehensive financial analysis in evaluating a success of a company and making wise investment choice is pivotal. The study provides methods to choose advantageous companies through comprehensive analysis. Simultaneously, these findings offer investors and stakeholders valuable insights when evaluating a company.
References
[1]. Ansari, M.F., Dash, B., Sharma, P. and Yathiraju, N. (2022) The impact and limitations of artificial intelligence in cybersecurity: a literature review. International Journal of Advanced Research in Computer and Communication Engineering, 11.
[2]. Kumar, S. and Mallipeddi, R.R. (2022) Impact of cybersecurity on operations and supply chain management: Emerging trends and future research directions. Production and Operations Management, 31(12), 4488-4500.
[3]. Walton, S., Wheeler, P.R., Zhang, Y. and Zhao, X. (2021) An integrative review and analysis of cybersecurity research: Current state and future directions. Journal of Information Systems, 35(1), 155-186.
[4]. Gao, L., Calderon, T.G. and Tang, F. (2020) Public companies' cybersecurity risk disclosures. International Journal of Accounting Information Systems, 38, 100468.
[5]. Ali, M.L., Thakur, K. and Atobatele, B. (2019) Challenges of cyber security and the emerging trends. In Proceedings of the 2019 ACM international symposium on blockchain and secure critical infrastructure, 107-112.
[6]. Zhang, X., Yadollahi, M.M., Dadkhah, S., Isah, H., Le, D.P. and Ghorbani, A.A. (2022) Data breach: analysis, countermeasures and challenges. International Journal of Information and Computer Security, 19(3-4), 402-442.
[7]. Tandon, A. and Nayyar, A. (2019) A comprehensive survey on ransomware attack: A growing havoc cyberthreat. Data Management, Analytics and Innovation: Proceedings of ICDMAI 2018, Volume 2, 403-420.
[8]. Kaur, C.J., Bhandari, A. and Behal, S. (2019) Distributed denial of service attacks: a threat or challenge. New Review of Information Networking, 24(1), 31-103.
[9]. Joao, A.R. (2011) Equity research project check point software technologies. UNL search, 11.
[10]. Etuk, E. E. (2016). Check point as alternative to access control lists in modern network security. Theseus, 1.
[11]. Moncy, M.M. (2023) Vulnerability Management in Practice: Contribution of Qualys to the ACCESS Project for Enhanced Cybersecurity.Springer, Berlin.
[12]. Muliński, T. (2020) ICT security in tax administration-Rapid7 Nexpose vulnerability analysis. Studia Informatica. System and information technology, 24(1-2), 37-51.
Cite this article
Ding,J. (2024). Analysis of Financial Performances for CHKP: Comparison with QLYS, RPD and GEN. Advances in Economics, Management and Political Sciences,107,20-27.
Data availability
The datasets used and/or analyzed during the current study will be available from the authors upon reasonable request.
Disclaimer/Publisher's Note
The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of EWA Publishing and/or the editor(s). EWA Publishing and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content.
About volume
Volume title: Proceedings of ICFTBA 2024 Workshop: Finance's Role in the Just Transition
© 2024 by the author(s). Licensee EWA Publishing, Oxford, UK. This article is an open access article distributed under the terms and
conditions of the Creative Commons Attribution (CC BY) license. Authors who
publish this series agree to the following terms:
1. Authors retain copyright and grant the series right of first publication with the work simultaneously licensed under a Creative Commons
Attribution License that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this
series.
2. Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the series's published
version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial
publication in this series.
3. Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and
during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work (See
Open access policy for details).
References
[1]. Ansari, M.F., Dash, B., Sharma, P. and Yathiraju, N. (2022) The impact and limitations of artificial intelligence in cybersecurity: a literature review. International Journal of Advanced Research in Computer and Communication Engineering, 11.
[2]. Kumar, S. and Mallipeddi, R.R. (2022) Impact of cybersecurity on operations and supply chain management: Emerging trends and future research directions. Production and Operations Management, 31(12), 4488-4500.
[3]. Walton, S., Wheeler, P.R., Zhang, Y. and Zhao, X. (2021) An integrative review and analysis of cybersecurity research: Current state and future directions. Journal of Information Systems, 35(1), 155-186.
[4]. Gao, L., Calderon, T.G. and Tang, F. (2020) Public companies' cybersecurity risk disclosures. International Journal of Accounting Information Systems, 38, 100468.
[5]. Ali, M.L., Thakur, K. and Atobatele, B. (2019) Challenges of cyber security and the emerging trends. In Proceedings of the 2019 ACM international symposium on blockchain and secure critical infrastructure, 107-112.
[6]. Zhang, X., Yadollahi, M.M., Dadkhah, S., Isah, H., Le, D.P. and Ghorbani, A.A. (2022) Data breach: analysis, countermeasures and challenges. International Journal of Information and Computer Security, 19(3-4), 402-442.
[7]. Tandon, A. and Nayyar, A. (2019) A comprehensive survey on ransomware attack: A growing havoc cyberthreat. Data Management, Analytics and Innovation: Proceedings of ICDMAI 2018, Volume 2, 403-420.
[8]. Kaur, C.J., Bhandari, A. and Behal, S. (2019) Distributed denial of service attacks: a threat or challenge. New Review of Information Networking, 24(1), 31-103.
[9]. Joao, A.R. (2011) Equity research project check point software technologies. UNL search, 11.
[10]. Etuk, E. E. (2016). Check point as alternative to access control lists in modern network security. Theseus, 1.
[11]. Moncy, M.M. (2023) Vulnerability Management in Practice: Contribution of Qualys to the ACCESS Project for Enhanced Cybersecurity.Springer, Berlin.
[12]. Muliński, T. (2020) ICT security in tax administration-Rapid7 Nexpose vulnerability analysis. Studia Informatica. System and information technology, 24(1-2), 37-51.









