1. Introduction
Quantum entanglement has been applied to various quantum protocols such as teleportation and dense coding assisted by classical channels [1, 2]. References [3, 4] showed showed the operational principles and mathematical foundations of several existing quantum communication protocols. Besides, quantum protocols can also be applied to classical computers [5]. Currently existing classical encryption methods are no longer entirely secure, as methods for rapidly breaking classical encryption have been proposed [6]. After addressing issues such as decoherence and noise [7, 8], the unique advantages of quantum encryption are gradually becoming apparent [9,10]. Subsequently, researchers investigated practical steps for quantum information transmission protocols, aiming to reduce costs and enhance efficiency [11]. Next, the quantum cost of dense coding and teleportation protocols has been evaluated in terms of CNOT gates [12]. Authors in [13] showed that the quantum remote control may be applied to realize the teleportation unitary gates. Furthermore, a similar technique has been used to teleport angles in a secure manner [14]. Further, multi partite scenarios have been considered for a deterministic single qubit. That is, recent advancements in the field of remote implementation of partially unknown quantum operations on multiple qubits have led to significant breakthroughs, rendering practical operations feasible. These developments have substantially propelled the potential applications of quantum communication and networking forward [15]. Besides, operation sharing with five-qubit cluster state has been established [16,17]. These operations and protocols provide a good foundation for realizing more complex protocols of transmitting information securely.
In this paper, we extend the above protocols by constructing a multi-party quantum security protocol based on the so-called remote-controlled implementation of operations. In Section II, we delve into the entangled state, inner product, and the Kronecker product. In Section III, we discuss a quantum communication protocol in which Bob sends messages to Charlie, and Alice has the ability to control the message transmission. By redesigning the communication protocol, we achieve the controlled communication among Alice and Bob. Alice measures her qubit and then sends it to the receiver Bob. As a result, Bob can perform a local measurement as a projection, and he manages to decode the secret from Alice. We finally conclude in Section V.
2. Preliminaries
We define the inner product of two n-dimensional vectors
Next we present the Bell state used in the protocol of quantum dense coding. The state is
Where
A general complex number x = a + bi with real a, b can be written as
2.1. Kronecker product and the vec operator
Definition 1. Let A be an n × p matrix and B an m × q matrix. The mn × pq matrix
is called the Kronecker product of A and B. It is also called the direct product or the tensor product.
2.2. Gates and states
We introduce the Hadamard gate as follows.
The Hadamard operation can transform the qubits |0〉and |1〉into their superposition with equal weights. The specific formulas are as follows.
Next, the CNOT gate is a quantum gate capable of transforming quantum states in the form of |a, b〉into |a, a ⊕ b〉where a, b = 0, 1. The operating principle of the CNOT gate is to take the first qubit as the control qubit, and perform the opposite transformation on the second qubit based on the state of the control qubit. It is important to note that the CNOT gate cannot operate on individual quantum states, as it automatically considers the first qubit as the decision maker. The CNOT gate has the matrix form as follows.
There are four forms of Bell states, each of which is a maximally entangled state of two quantum bits. The properties of entanglement are used to transfer information in the following quantum communication. The specific formula of four Bell states are as follows.
3. Result on dense coding
In this section, we introduce the basics of quantum dense coding protocol, see a simple description in Figure 1. As the first step, we generate a pair of entangled EPR states through the source S, shared between Alice and Bob. The state of the EPR pair can be represented as the Bell state (37). To obtain the Bell state |ϕ〉, a Hadamard gate is first applied to the initial state |0〉, namely on the first qubit. This is followed by a controlled-NOT (CNOT) operation. Mathematically, this process is as follows:
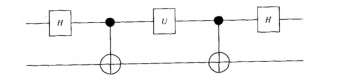
In the computational basis |00〉, |01〉, |10〉, and |11〉, the EPR pair and the gate operations can be represented using matrices. The result shows that the obtained |ϕ〉can be expressed in matrix form as,
In the computational basis |00〉, |01〉, |10〉, and |11〉, (Note: The first digit refers to Alice’s half of the EPR pair, and the second digit refers to Bob’s half), the transformation (4.20) has the following matrix representation,
The value of U is determined by the classical comparison of the two bits that Alice wants to transmit to Bob. If she wants to transmit |00〉, she performs the following operation on her half of the EPR pair,
If she wants to transmit |01〉, she applies the Pauli matrix σx on her half of the EPR pair,
In the computational basis, the state is represented as follows,
If she wants to transmit |10〉, she applies σz on her half of the EPR pair,
and the matrix form is shown as,
Finally, if she wants to transmit |11〉, she applies
and the matrix form is shown as,
We calculate the tensor products
Since
we have
We also need decode the message by inverse operation. That is,
We record this operator as B. By taking the decoding operator, Bob can finally obtain the correct message.
Any unitary operator U is orthogonal and thus can be diagonalized. Therefore, its spectral decomposition can be written as
Since a unitary operator preserves the inner product of vectors, we have
This implies that |
where
Since A is already in diagonal form, the operator
Thus,
Thus, the condition
Computing the commutator
The first instrument measures the final state |+⟩z = |1⟩. The particle in state |1⟩ then enters the second instrument and is prepared in the state
Finally, the third instrument analyzes the state |+⟩y, measuring σx. With equal probabilities p0 and p1, the two possible output states |0⟩x = |0⟩ and |1⟩x = |1⟩ are obtained,
The solution to the Schrodinger equation is given by
where the unitary time evolution operator is
and
Expanding U(t), we obtain
Finally, in matrix representation,
4. Quantium teleportation
Quantum invisible transmission of states through quantum entanglement of Bell states allows the transmission of quantum information at both ends solely through the classical channel. The principles and methods are as follows. Suppose Alice wants to convey to Bob the two-energy-level quantum information that is in a superposition state
Step 1. We build the EPR pair.
The source S generates an EPR pair namely a Bell state, and sends the first half to Alice and the second half to Bob. Make sure the pair of quanta is in an entangled state
By sending the EPR pair to Alice and Bob, Alice has two particles, which are respectively half of the EPR pair and the message qubit she wants to transmit to Bob. On the other hand, Bob only has one qubit, namely the other half of EPR pair.
The state of the three qubits are given by the tensor product of
Step 2. Joint measurement by Alice.
The reason why Alice needs to do the joint measurement is that if Alice only determines message qubit, this quantum will collapse to |0〉or |1〉. The way out of this problem is to make measurements on the Bell state, i.e.,
Then we insert Eq. (37) into (36), by transforming the computational basis into the Bell basis.
In this case, if Alice does a Bell Measurement, she has the same chance to obtain every state of
Step 3. Unitary operation is carried out by Bob.
Alice sends the result of the Bell measurements to Bob by classical messages. Bob can use this message to determine which of the quantum states is this message corresponds to.
By taking this operation, Bob can obtain the message qubit α|0〉+β|1〉. So we have completed the protocol of quantum teleportation.
5. Conclusions
We have shown the dense coding protocol of controlled remote implementation of operations in two participants. They show the quantum security guaranteed by the basic rules of quantum mechanics by using entanglement and measurement. An open problem unsolved in this paper is to extend the results to implementation of operations of many parties. Whether entanglement in this protocol could be decreased is also an interesting issue for the next step.
References
[1]. Bennett, Brassard, Crepeau, Jozsa, Peres, and Wootters. Teleporting an un- known quantum state via dual classical and einstein-podolsky-rosen channels. Phys- ical review letters, 70(13): 1895–1899, 1993.
[2]. Bennett and Wiesner. Communication via one- and two-particle operators on einstein-podolsky-rosen states. Physical review letters, 69(20): 2881–2884, 1992.
[3]. Nicolas Gisin, Gr ´egoire Ribordy, Wolfgang Tittel, and Hugo Zbinden. Quan- tum cryptography. Reviews of Modern Physics, 74: 145–195, 2002.
[4]. Christopher Portmann and Renato Renner. Security in quantum cryptography. Reviews of Modern Physics, 94: 025008, 2022.
[5]. Deutsch D. and Jozsa R. Rapid solution of problems by quantum computation. Proceedings of the Royal Society A: Mathematical, 439(1907): 553–558, 1992.
[6]. Peter W. Shor. Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. Siam Journal on Computing, 1997.
[7]. Yuri Alexeev. Quantum computer systems for scientific discovery. PRX Quantum, 2: 017001, 2021.
[8]. J. I. Cirac, A. K. Ekert, S. F. Huelga, and C. Macchiavello. Distributed quantum computation over noisy channels. Physical Review A, 59: 4249–4254, 1999.
[9]. Alessio Serafini, Stefano Mancini, and Sougato Bose. Distributed quantum computation via optical fibers. Physical Review Letters, 96: 010503, 2006.
[10]. Dik Bouwmeester, Jian-Wei Pan, Klaus Mattle, Manfred Eibl, Harald We- infurter, and Anton Zeilinger. Experimental quantum teleportation. Nature, 390(6660): 575–579, 1997.
[11]. Iulia Georgescu. 25 years of experimental quantum teleportation. Nature Reviews Physics, 2022.
[12]. Xinyu Qiu and Lin Chen. Quantum cost of dense coding and teleportation. Physical Review A, 105: 062451, 2022.
[13]. S. F. Huelga, J. A. Vaccaro, A. Chefles, and M. B. Plenio. Quantum remote control: Teleportation of unitary operations. Physical Review A, 63(4), 2001.
[14]. S. F. Huelga, M. B. Plenio, and J. A. Vaccaro. Remote control of restricted sets of operations: Teleportation of angles. Physical Review A, 65(4), 2002.
[15]. An Min Wang. Combined and controlled remote implementations of par- tially unknown quantum operations of multiqubits using greenberger-horne-zeilinger states. Physical Review A, 75(6), 2007.
[16]. M. A. Nielsen and I. L. Chuang. Quantum Computation and Quantum In- formation. Cambridge University Press, Cambridge, 2000.
[17]. Shengfang Wang, Yimin Liu, Jianlan Chen, Xiansong Liu, and Zhanjun Zhang. Deterministic single-qubit operation sharing with five-qubit cluster state. Quantum Information Processing, 12(7): 2497-2507, 2013.
Cite this article
Liu,Y. (2025). On Quantum Dense Coding for Bipartite Systems. Theoretical and Natural Science,136,9-20.
Data availability
The datasets used and/or analyzed during the current study will be available from the authors upon reasonable request.
Disclaimer/Publisher's Note
The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of EWA Publishing and/or the editor(s). EWA Publishing and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content.
About volume
Volume title: Proceedings of CONF-APMM 2025 Symposium: Multi-Qubit Quantum Communication for Image Transmission over Error Prone Channels
© 2024 by the author(s). Licensee EWA Publishing, Oxford, UK. This article is an open access article distributed under the terms and
conditions of the Creative Commons Attribution (CC BY) license. Authors who
publish this series agree to the following terms:
1. Authors retain copyright and grant the series right of first publication with the work simultaneously licensed under a Creative Commons
Attribution License that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this
series.
2. Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the series's published
version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial
publication in this series.
3. Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and
during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work (See
Open access policy for details).
References
[1]. Bennett, Brassard, Crepeau, Jozsa, Peres, and Wootters. Teleporting an un- known quantum state via dual classical and einstein-podolsky-rosen channels. Phys- ical review letters, 70(13): 1895–1899, 1993.
[2]. Bennett and Wiesner. Communication via one- and two-particle operators on einstein-podolsky-rosen states. Physical review letters, 69(20): 2881–2884, 1992.
[3]. Nicolas Gisin, Gr ´egoire Ribordy, Wolfgang Tittel, and Hugo Zbinden. Quan- tum cryptography. Reviews of Modern Physics, 74: 145–195, 2002.
[4]. Christopher Portmann and Renato Renner. Security in quantum cryptography. Reviews of Modern Physics, 94: 025008, 2022.
[5]. Deutsch D. and Jozsa R. Rapid solution of problems by quantum computation. Proceedings of the Royal Society A: Mathematical, 439(1907): 553–558, 1992.
[6]. Peter W. Shor. Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. Siam Journal on Computing, 1997.
[7]. Yuri Alexeev. Quantum computer systems for scientific discovery. PRX Quantum, 2: 017001, 2021.
[8]. J. I. Cirac, A. K. Ekert, S. F. Huelga, and C. Macchiavello. Distributed quantum computation over noisy channels. Physical Review A, 59: 4249–4254, 1999.
[9]. Alessio Serafini, Stefano Mancini, and Sougato Bose. Distributed quantum computation via optical fibers. Physical Review Letters, 96: 010503, 2006.
[10]. Dik Bouwmeester, Jian-Wei Pan, Klaus Mattle, Manfred Eibl, Harald We- infurter, and Anton Zeilinger. Experimental quantum teleportation. Nature, 390(6660): 575–579, 1997.
[11]. Iulia Georgescu. 25 years of experimental quantum teleportation. Nature Reviews Physics, 2022.
[12]. Xinyu Qiu and Lin Chen. Quantum cost of dense coding and teleportation. Physical Review A, 105: 062451, 2022.
[13]. S. F. Huelga, J. A. Vaccaro, A. Chefles, and M. B. Plenio. Quantum remote control: Teleportation of unitary operations. Physical Review A, 63(4), 2001.
[14]. S. F. Huelga, M. B. Plenio, and J. A. Vaccaro. Remote control of restricted sets of operations: Teleportation of angles. Physical Review A, 65(4), 2002.
[15]. An Min Wang. Combined and controlled remote implementations of par- tially unknown quantum operations of multiqubits using greenberger-horne-zeilinger states. Physical Review A, 75(6), 2007.
[16]. M. A. Nielsen and I. L. Chuang. Quantum Computation and Quantum In- formation. Cambridge University Press, Cambridge, 2000.
[17]. Shengfang Wang, Yimin Liu, Jianlan Chen, Xiansong Liu, and Zhanjun Zhang. Deterministic single-qubit operation sharing with five-qubit cluster state. Quantum Information Processing, 12(7): 2497-2507, 2013.









