1. Introduction
As technology progressed, the focus of research shifted from the macroscopic to the microscopic level, and quantum physics was born. Among the various fields of quantum mechanics, quantum entanglement is one of the major discoveries in the history of human physics.
The transmission of information is an integral part of people's daily lives today. It can break the limits of space and allowing us to communicate quickly over long distances. However, traditional communication methods are increasingly unable to meet the demands for speed, capacity and confidentiality. As a result, people are looking for help at the microphysical level. Quantum entanglement has some principles and it has the ability to be applied to the fields of messaging and cryptography [1-3]. At the same time, there are interactions between mutually entangled quanta that transcend space [4]. These may enable it to help people to fulfil their needs in messaging, making it one of the hottest objects of research in this field.
This article will investigate the state-of-art applications and the function of quantum entanglement in quantum information. This is the format for the remaining portion of the paper. Sec. 2 will introduce the basic principles of quantum entanglement and the history of its development. Sec. 3 will give examples and introduce cutting-edge applications of quantum entanglement in quantum information. Quantum teleportation, quantum key distribution, and quantum radar are a few examples. Sec. 4 will analyse the limitations and prospects of quantum entanglement as applied to quantum information. Eventually, Sec. 5 will give a conclusion of this article.
2. Quantum entanglement & quantum information
2.1. Definition
Quantum entanglement is the process of fusing the properties of different substances into a single state when multiple particles interact with each other. This means that two substances in an entangled state will form a relationship such that, regardless of the distance between them, if the properties of one substance change, the properties of the other substance with which it is entangled will also change accordingly. These changes are not affected by distance. In two entangled particles, an entangled state| \( ψ \) ⟩ is formed. Using the Dirac notation, this can be expressed as:
\( |ψ⟩=\frac{1}{\sqrt[]{2}}(|↑⟩⨂|↓⟩-|↓⟩⨂|↑⟩) \) (1)
In the Equation (1), |↑⟩ means the particle spin is up-spin and |↓⟩ means the particle spin is down-spin. In quantum mechanics, the information about the nature and state of a particle conveyed by quantum entanglement is known as quantum information. Unlike what is referred to as information in everyday life, quantum information is usually measured in quantum bits. Similar to binary, a quantum bit is a quantum system with only two states.
2.2. Development history
At the Solvay Conference in 1927, two rival schools of thought were formed, the Copenhagen School and the Copenhagen Opposition. These two schools of thought made arguments about quantum mechanics at the conference. The Copenhagen School supporting the existence of quantum mechanics and the Copenhagen Opposition putting forward a negative view.
Einstein, Podolsky and Rosen published a milestone in the Physical Review Letters in the year of 1935 [5]. The three authors address the incompleteness of quantum mechanics in the paper [5]. For a long time after the essays by Einstein, Podolsky and Rosen was published in the year 1927, not much attention was paid to this area. In 1964, Bell published a paper supporting fixed-domain positivism and proposed Bell's inequality, which has the mathematical form shown in Equation (2) [6]:
\( |{P_{xz}}-{P_{zy}}|≤1+{P_{xy}}\ \ \ (2) \)
Numerous experiments have been conducted by scientists to validate Bell's inequality. Clauser and Freedman first completed the experiment in 1972. In 1982, Aspect et al. performed experiments to verify Bell's inequality. Although the experimental results are completely consistent with those made by quantum theory, they are diverged by 5 standard deviations from Bell's inequality predictions [7]. In 1998, university students in Innsbruck sent photons flying 400 metres apart. The experimental results deviated from the local hidden variable theory predictions by 30 standard deviations [8]. Although these experimental findings are in line with predictions made by quantum mechanics, they are not in line with those made by the hidden variable theory of definiteness. Therefore, it can be tentatively proved that the theory of fixed-domain hidden variables is not valid, and further confirmed the reality of quantum entanglement.
In recent years, researchers have continued to work on the study of quantum entanglement. Bennett and Brassard proposed the BB84 Protocol and Eckert proposed the E91 Protocol [9, 10]. On 16 June 2017, the Mozi satellite distributed two quantum entangled photons to more than 1200 km apart, achieving for the first time the continued quantum entanglement of these two photons [11]. This study once again verifies the incorrectness of Bell's inequality. Therefore, it favours the development of quantum entanglement. On 25 April 2018, a team led by Sillanpää successfully entangled two 15-micron-wide, solitary vibrating tympanic membranes made of 10 aluminium atoms and made them interact for about 30 minutes, in a superconducting microwave circuit and at close to -273.15°C. This experiment demonstrates macroscopic quantum entanglement [12, 13]. Fig. 1, Fig. 2, and Fig. 3 show a diagram of the experimental set-up [14, 15].
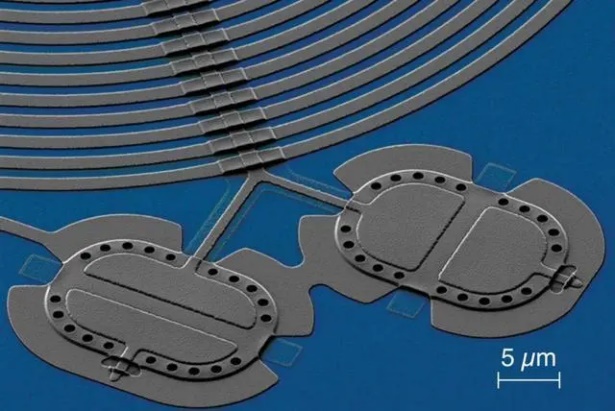
Figure 1. Scanning electron microscope photograph of the aluminum tympanum used in the experiment (pseudo-colour image).

Figure 2. Schematic diagram of the experimental system.
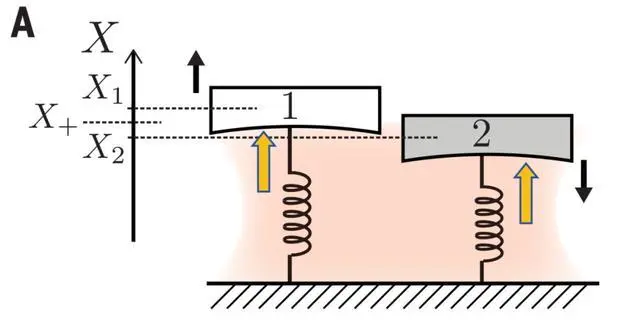
Figure 3. Schematic diagram of the experiment.
3. Applications of quantum entanglement
There are not many applications that apply to a broader scale because quantum mechanics is a science that is still relatively new. As a result, applications of quantum entanglement are still mainly in the experimental part.
3.1. Quantum communication
Quantum mechanics is characterised by Uncertainty Principle, Collapse Measurement and No-Cloning Theorem [1-3]. Once a quantum message receives interference during transmission, it immediately changes state and will be detected by both the sender and receiver. Quantum communication therefore has a security that is difficult to eavesdrop and computationally decipher. Quantum communication is mainly divided into quantum teleportation and quantum key distribution. Quantum teleportation of states makes use of dispersive quantum entanglement with the conversion of some physical messages. It is a method for sending a quantum state and the quantum information it contains to a destination that is any distance away [16]. The Fig. 4 shows the schematic diagram of quantum teleportation [17].
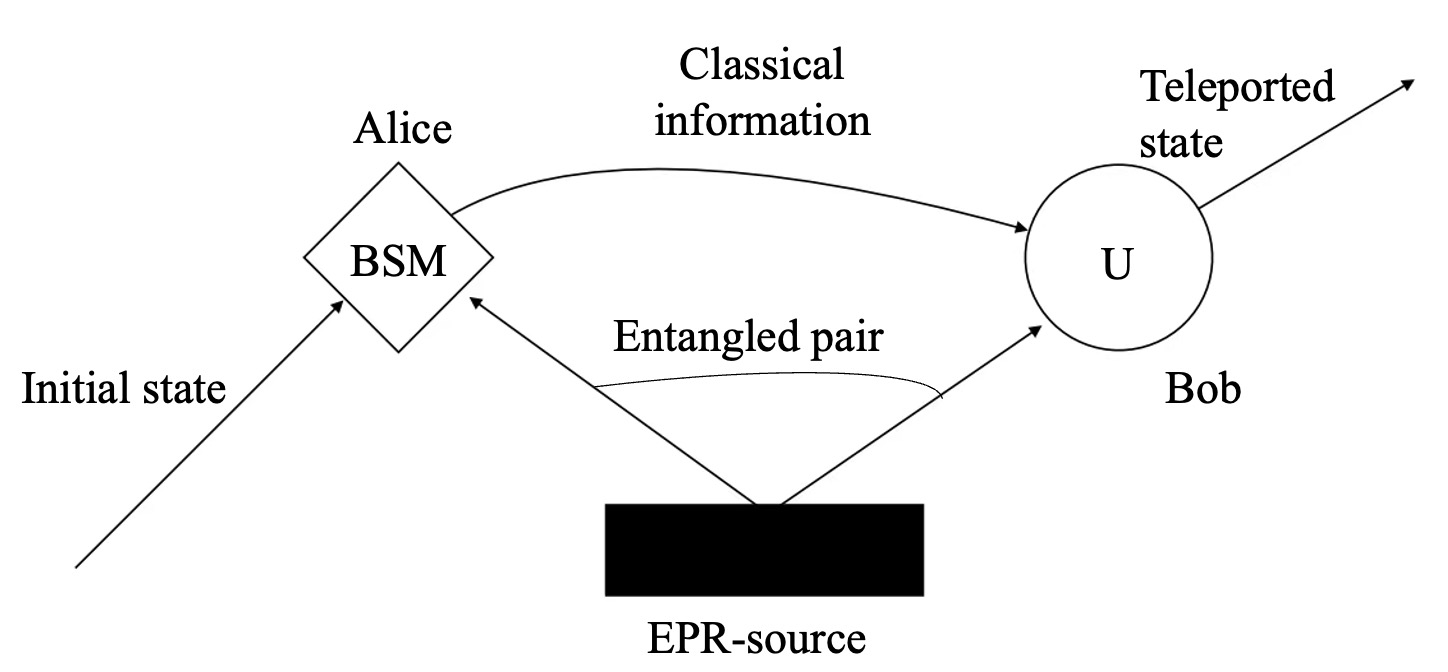
Figure 4. Fundamentals of quantum teleportation.
The first proof of principle experiment of quantum teleportation was done indoors by Zeilinger's group in Austria in 1997 [18]. This group went on to increase the distance of quantum teleportation to 600 metres in 2004 [19]. In 2005, Pan of the University of Science and Technology of China and others achieved a bidirectional quantum entanglement spread of 13 kilometres [20]. This distance broke the previous record [20]. At the same time, they have verified the feasibility of distributing entangled photon pairs between outer space and Earth [20]. In August 2012, scientists from China, including Pan, successfully achieved international quantum teleportation and entanglement distribution in free space on the order of 100 km [21, 22]. This is the first time this experiment has been done in the world. Quantum teleportation is the simplest of the many types of quantum communication. In recent years, scientists around the world are still working on quantum teleportation.
In addition to quantum teleportation, quantum key distribution is also an important manifestation of quantum entanglement applied to quantum information. Text that is normally seen and from which information can be obtained directly is called plaintext. Texts that people cannot read, that are encrypted or that have been disrupted in some ways are called ciphertexts. There is a correspondence between the plaintext and the ciphertext. Converting plaintext into ciphertext (encryption) or deciphering ciphertext into plaintext (decryption) requires a parameter, namely a secret key. Quantum key distribution belongs to the cryptographic field of cryptography. It makes use of the quantum mechanics properties, which was mentioned by the author in the previous section, enabling two parties to a communication to generate and share a key. This secret key is random and secure and can be used to encrypt and decrypt the message, thus securing the communication [23]. The protocols involved in quantum key distribution are the BB84 protocol (its basic principle is shown in Fig. 5), the BBM92 protocol and the E91 protocol [9, 10, 24]. In February 2022, the world record for secure transmission distance for quantum key distribution was raised by more than 200 km, bringing fiber optic quantum key distribution to 833 km. This achievement was accomplished by Professor Han and his collaborators from Academician Guo's team at the University of Science and Technology of China [25].
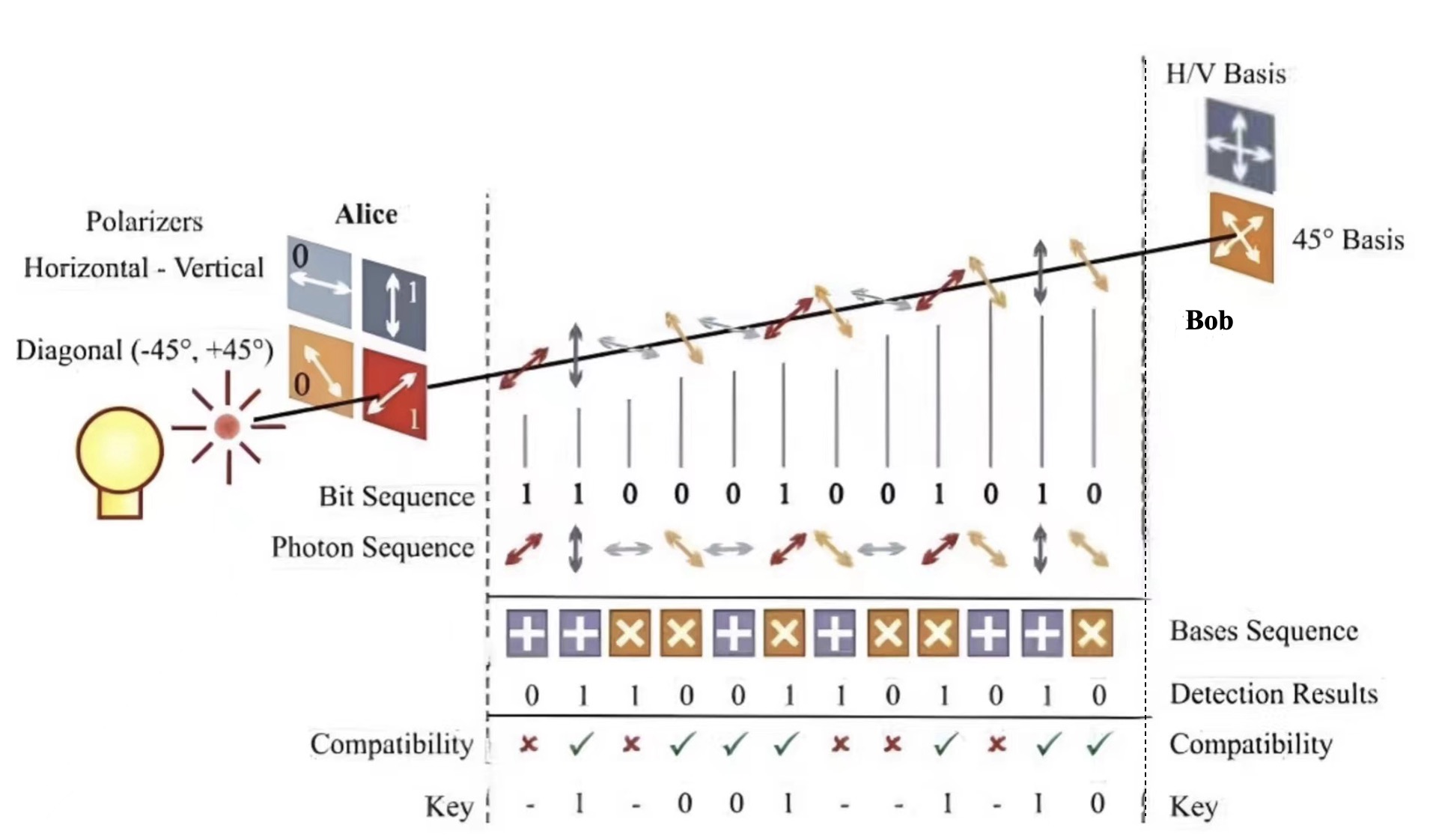
Figure 5. The basic principle of BB84 protocol.
3.2. Quantum radar
Radar is used to calculate the position of the object to be measured by transmitting an electromagnetic signal and receiving the reflected signal from the object to be detected through time and angle. It is mainly used for early warning, surveillance, weather forecasting, tracking, etc. [26]. Due to objective physical laws limiting its measurement accuracy, conventional radar can no longer meet the increasingly demanding requirements of today [27]. In contrast to conventional radar, quantum radar utilises quantum phenomena and is a quantum remote sensor for target state sensing and information acquisition, which is showed in Fig. 6 [28]. Quantum radar can be used to identify stealthy combat aircraft. At the same time, it is not subject to interference from other radars.
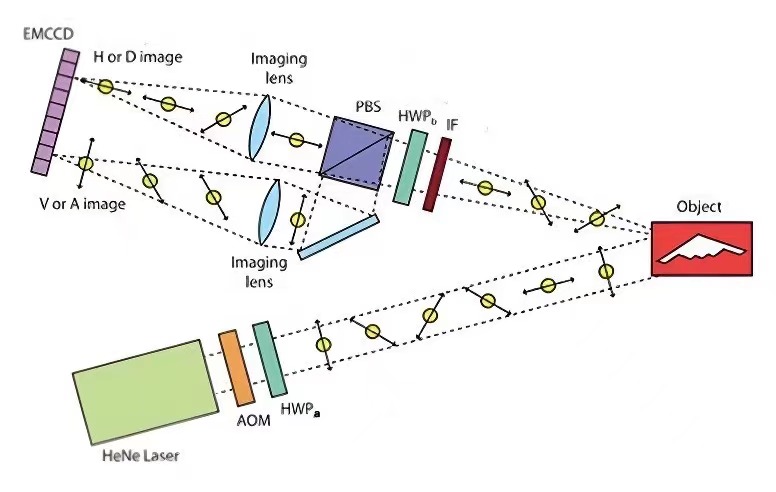
Figure 6. Quantum radar utilises quantum phenomena and is a quantum remote sensor for target state sensing and information acquisition.
4. Limitations & prospects
Quantum entanglement has some aspects of unparalleled superiority. If it is applied to quantum information, it can largely secure information and improve transmission efficiency. Quantum entanglement has wonderful characteristics not present in conventional physical phenomena. As a result, it might have a unique function in quantum communication [29]. However, quantum entanglement still has certain limitations and technical difficulties. For example, the way to avoid noise interference, the rigour of the conditions required for the experiment, the difficulty of measurement and the number of manipulable quanta. These limitations and technical difficulties can make it difficult for both sides of the communication to tell whether the message has been interfered with by external factors or is being listened to. At the same time, these problems have led to many applications of quantum entanglement being done only in the laboratory, but not being applied on a large scale. In the future, the applications of quantum entanglement might be extended. It can provide security for national information. At the same time, quantum entanglement will also make a great contribution to quantum computing. Scientists still need to explore and try a lot to find the right materials and conditions for their experiments. Perhaps someday in the future, quantum entanglement will be widely used, coming into people's homes, and participating in their lives.
5. Conclusion
In summary, this study investigates the state-of-art applications and the function of quantum entanglement in quantum information, and shows the limitations and prospects of them. Overall, these results offer a guideline for the development of quantum information. However, one thing is for sure, once researchers have achieved the wide application of quantum entanglement, it will be a very significant milestone in the history of human physics.
References
[1]. Heisenberg W 1927 Uber Den Qnschaulichen Inhalt Der Quantentheoretischen Kinematik und Mechanik Zeitschrift Für Physik 43(3-4) pp 172-198.
[2]. Wootters W K and Zurek W H 1982 A Single Quantum Cannot be Cloned Nature 299 pp. 802.
[3]. Kumar M 2009 Quantum: Einstein, Bohr, and the Great Debate About the Nature of Reality Biography An Interdisciplinary Quarterly 135(6) pp. 93-93.
[4]. Ye M, Zhang Y, and Guo G 2007 Quantum Entanglement and Quantum Manipulation. Science in China Series G 37(6) pp. 7.
[5]. Einstein A, Podolsky B and Rosen N 1935 Can Description of Physical Reality be Considered Complete? J. Phys. Rev, 47 pp. 777-780
[6]. Bell J S 1964 On the Einstein-Podolsky-Rosen Paradox. Physics 1 pp. 195.
[7]. Aspect A, Dalibard J and Roger G 1982 Experimental Realization of Einstein-Podolsky-Rosen-Bohm Gedankenexperiment: A New Violation of Bell's Inequalities. Physical Review Letters, 49(2), pp. 91-94.
[8]. Weihs G, Jennewein T, and Simon C H et al 1998 Violation of Bell inequality under strict Einstein locality conditions. 81, pp. 5039-5043.
[9]. Bennett C H and Brassard G 1984 Quantum Cryptography: Public Key Distribution and Coin Tossing. IEEE International Conference on Computers, Systems and Signal Processing, New York: IEEE 1 pp. 175-179.
[10]. Ekert A K 1991 Quantum Cryptography Based on Bell's Theorem. Physical Review Letters 67(6) pp. 661-663.
[11]. ScienceNet.cn 2017 Chinese Quantum Satellite Achieves 1000 km Quantum Entanglement Distribution. Public Communication of Science & Technology 12 2.
[12]. Riedinger R, Wallucks A and Marinković I. et al 2018 Remote Quantum Entanglement Between Two Micromechanical Oscillators Nature 556 pp. 473–477.
[13]. Ockeloen-Korppi C F, Damskägg E and Pirkkalainen J M et al 2018 Stabilized entanglement of massive mechanical oscillators Nature 556 pp. 478–482.
[14]. Kotler S, Peterson G A, and Shojaee E, et al 2014 Direct observation of deterministic macroscopic entanglement. Science 372(6542) pp. 622-625.
[15]. LMD Lépinay, Ockeloen-Korppi C F, and Woolley M J, et al 2014 Quantum mechanics-free subsystem with mechanical oscillators Science 372(6542) pp. 625-629.
[16]. Bennett C H, Brassard G, and Crépeau C, et al 1993 Teleporting an unknown quantum state via dual classical and Einstein-Podolsky-Rosen channels Physical review letters 70(13) 1895.
[17]. Su X, and Guo G 2004 Teleportation of Quantum Theory of Contact Progress in Physics, 24(3) 15.
[18]. Bouwmeester D, Pan J W, Matfle K, Eibl M, Weinfurter H, and Zeilinger A 1997 Experimental Quantum Teleportation Nature 390 pp. 575-579.
[19]. Aspelmeyer M, Bhm H R, and Gyatso T, et al 2003 Long-Distance Free-Space Distribution of Quantum Entanglement Science 301(5633) pp. 621-623.
[20]. Zhang J, Peng C, and Bao X, et al 2015 New Progress on Experimental Quantum Cryptography--Experimental Free-Space Distribution of Entangled Photon Pairs Over 13km. Physics, 34(10), pp. 7.
[21]. Gui Y. University of Science and Technology of China Sets New World Record for Quantum Teleportation Across 100 km for the First Time. Anhui Daily, August 11, 2012.
[22]. Wu C. University of Science and Technology of China Successfully Achieves the First Quantum Teleportation Across 100 km for the First Time Satellite Helps Make Global Quantum Communication Network Feasible. Anhui Science & Technology, 2012, 9: 2.
[23]. Bennett C H. Quantum Key Distribution and Coin Tossing. International Conference on Computers, 1984.
[24]. Bennett C H, Brassard G, and Mermin N D 1992 Quantum Cryptography Without Bell’s Theorem. Physical Review Letters 68(5) pp. 557-559.
[25]. Wang S, Yin Z Q, and He D Y, et al 2022 Twin-field Quantum Key Distribution Over 830-km Fibre. Nat. Photon 16 pp. 154–161.
[26]. Hu F, Cui G, and Kong L 2014 Network Design of Integrated Radar and Communication System. Radar Science and Technology 12(5) pp. 455-459, 469.
[27]. Han G, Ye R, and Liu L, et al. 2014 Simulation and Analysis of New Deceptive Jamming Effect on ISAR. Radar Science and Technology 12(5) pp. 532-538.
[28]. Lanzagorta M 2011 Quantum Radar. Synthesis Lectures on Quantum Computing 3(1) pp. 1-139.
[29]. Liu Y, Huang Y, and Wang Y, et al 2011 Analysis on Features and Limits of Quantum Communication. Information Security and Communication Privacy 9(9) 3.
Cite this article
Wang,Y. (2023). State-of-art applications and the function of quantum entanglement in quantum information. Theoretical and Natural Science,10,9-15.
Data availability
The datasets used and/or analyzed during the current study will be available from the authors upon reasonable request.
Disclaimer/Publisher's Note
The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of EWA Publishing and/or the editor(s). EWA Publishing and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content.
About volume
Volume title: Proceedings of the 2023 International Conference on Mathematical Physics and Computational Simulation
© 2024 by the author(s). Licensee EWA Publishing, Oxford, UK. This article is an open access article distributed under the terms and
conditions of the Creative Commons Attribution (CC BY) license. Authors who
publish this series agree to the following terms:
1. Authors retain copyright and grant the series right of first publication with the work simultaneously licensed under a Creative Commons
Attribution License that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this
series.
2. Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the series's published
version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial
publication in this series.
3. Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and
during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work (See
Open access policy for details).
References
[1]. Heisenberg W 1927 Uber Den Qnschaulichen Inhalt Der Quantentheoretischen Kinematik und Mechanik Zeitschrift Für Physik 43(3-4) pp 172-198.
[2]. Wootters W K and Zurek W H 1982 A Single Quantum Cannot be Cloned Nature 299 pp. 802.
[3]. Kumar M 2009 Quantum: Einstein, Bohr, and the Great Debate About the Nature of Reality Biography An Interdisciplinary Quarterly 135(6) pp. 93-93.
[4]. Ye M, Zhang Y, and Guo G 2007 Quantum Entanglement and Quantum Manipulation. Science in China Series G 37(6) pp. 7.
[5]. Einstein A, Podolsky B and Rosen N 1935 Can Description of Physical Reality be Considered Complete? J. Phys. Rev, 47 pp. 777-780
[6]. Bell J S 1964 On the Einstein-Podolsky-Rosen Paradox. Physics 1 pp. 195.
[7]. Aspect A, Dalibard J and Roger G 1982 Experimental Realization of Einstein-Podolsky-Rosen-Bohm Gedankenexperiment: A New Violation of Bell's Inequalities. Physical Review Letters, 49(2), pp. 91-94.
[8]. Weihs G, Jennewein T, and Simon C H et al 1998 Violation of Bell inequality under strict Einstein locality conditions. 81, pp. 5039-5043.
[9]. Bennett C H and Brassard G 1984 Quantum Cryptography: Public Key Distribution and Coin Tossing. IEEE International Conference on Computers, Systems and Signal Processing, New York: IEEE 1 pp. 175-179.
[10]. Ekert A K 1991 Quantum Cryptography Based on Bell's Theorem. Physical Review Letters 67(6) pp. 661-663.
[11]. ScienceNet.cn 2017 Chinese Quantum Satellite Achieves 1000 km Quantum Entanglement Distribution. Public Communication of Science & Technology 12 2.
[12]. Riedinger R, Wallucks A and Marinković I. et al 2018 Remote Quantum Entanglement Between Two Micromechanical Oscillators Nature 556 pp. 473–477.
[13]. Ockeloen-Korppi C F, Damskägg E and Pirkkalainen J M et al 2018 Stabilized entanglement of massive mechanical oscillators Nature 556 pp. 478–482.
[14]. Kotler S, Peterson G A, and Shojaee E, et al 2014 Direct observation of deterministic macroscopic entanglement. Science 372(6542) pp. 622-625.
[15]. LMD Lépinay, Ockeloen-Korppi C F, and Woolley M J, et al 2014 Quantum mechanics-free subsystem with mechanical oscillators Science 372(6542) pp. 625-629.
[16]. Bennett C H, Brassard G, and Crépeau C, et al 1993 Teleporting an unknown quantum state via dual classical and Einstein-Podolsky-Rosen channels Physical review letters 70(13) 1895.
[17]. Su X, and Guo G 2004 Teleportation of Quantum Theory of Contact Progress in Physics, 24(3) 15.
[18]. Bouwmeester D, Pan J W, Matfle K, Eibl M, Weinfurter H, and Zeilinger A 1997 Experimental Quantum Teleportation Nature 390 pp. 575-579.
[19]. Aspelmeyer M, Bhm H R, and Gyatso T, et al 2003 Long-Distance Free-Space Distribution of Quantum Entanglement Science 301(5633) pp. 621-623.
[20]. Zhang J, Peng C, and Bao X, et al 2015 New Progress on Experimental Quantum Cryptography--Experimental Free-Space Distribution of Entangled Photon Pairs Over 13km. Physics, 34(10), pp. 7.
[21]. Gui Y. University of Science and Technology of China Sets New World Record for Quantum Teleportation Across 100 km for the First Time. Anhui Daily, August 11, 2012.
[22]. Wu C. University of Science and Technology of China Successfully Achieves the First Quantum Teleportation Across 100 km for the First Time Satellite Helps Make Global Quantum Communication Network Feasible. Anhui Science & Technology, 2012, 9: 2.
[23]. Bennett C H. Quantum Key Distribution and Coin Tossing. International Conference on Computers, 1984.
[24]. Bennett C H, Brassard G, and Mermin N D 1992 Quantum Cryptography Without Bell’s Theorem. Physical Review Letters 68(5) pp. 557-559.
[25]. Wang S, Yin Z Q, and He D Y, et al 2022 Twin-field Quantum Key Distribution Over 830-km Fibre. Nat. Photon 16 pp. 154–161.
[26]. Hu F, Cui G, and Kong L 2014 Network Design of Integrated Radar and Communication System. Radar Science and Technology 12(5) pp. 455-459, 469.
[27]. Han G, Ye R, and Liu L, et al. 2014 Simulation and Analysis of New Deceptive Jamming Effect on ISAR. Radar Science and Technology 12(5) pp. 532-538.
[28]. Lanzagorta M 2011 Quantum Radar. Synthesis Lectures on Quantum Computing 3(1) pp. 1-139.
[29]. Liu Y, Huang Y, and Wang Y, et al 2011 Analysis on Features and Limits of Quantum Communication. Information Security and Communication Privacy 9(9) 3.









