1. Introduction
Fractal is a mathematic theory that contributes to the generation or explanation of an irregular object. The word chaos in the title could be considered as a property of a fractal object. This is because when people write an IFS (its full name is an iterated function system) this function group controls the movement of point A [1, 2]. Mathematicians start to operate the program and observe the movement or the track of point A. They will find out that the action path of this point A couldn’t be predicted in other words it has a chaotic movement. In doing so, chaos could be considered as a property of Fractal. Nowadays, many pictures need to be encrypted or processed. The reason why some pictures must be encrypted is that some people will use a picture to send some important and private messages via the Internet. However, the internet is not 100% safe. Some hacker will hack their account or chat and get these pictures. As a result, it will lead to a high possibility of private information leakage. Meanwhile, the quality, reliability, and complexity would be three essential points for customers to judge and evaluate the level of safety of a type of encryption. This is because coding with less complexity, low quality, and reliability will lead to a problem in that hackers can quite easily decode those pictures which leads to the disclosure of privacy. Under this circumstance, fractal image coding which is also called FIC could be seen as a method with a bright future. The purpose of encryption is to convert to unrecognizable noise-like by using a mathematical formula [3, 4]. Since fractal and Iterated Function System has the characteristic of chaotic and unpredictable, FIC could be considered a high-level and high-standard coding method. This is because this method breaks through the boundaries of previous entropy compression coding. On the other side, Fractal also has great potential in picture processing. Some pictures are clear because of low resolution and the picture will become illegible. So that people cannot identify the stuff that appears in this picture. Meanwhile, in some pictures, the edges of objects are not clear and smooth. In some pictures, the edges of some objects won’t be curved, they will be come straight line indeed. In doing so, the person who looks at this picture will be confused about whether the object in this picture is real or not. It will provide a very bad impression. Fractal image coding is one of the more promising image coding methods at present, and it is also one of the most widely studied coding methods. It has been studied for nearly ten years. In the coding process, similar descriptions are used method, and decoding is completed iteratively and has resolution-independent decoding characteristics, etc. Image compression has been studied for decades, with proposed methods such as DPCM, DCT, VO, and other compression methods, and has introduced international compression standards based on DCT and other technologies, such as JPEG, MPEG, H.261, etc., image compression has been widely used in practical applications [5-7].
In this research, the author analyses the future of fractal coding by discussing the advantages and disadvantages of this method from different articles. Furthermore, in this article, the author discusses the definition of fractals and the properties of fractals. Iterative Function System (IFS) is also a key point in photo processing.
2. Fractal and Chaos
2.1. Introduction of fractal and IFS
In the previous chapter, the author said that chaos could be seen as a property of Fractal. This is because when researchers are trying to describe the movement of the point, they find out that the locus is unpredictable and disordered. For example, if a writer wants to produce a fractal object, like Barnsley Fern, what the writer needs to do is write four different affine transformations and this function group, mathematicians give it a name, called IFS which stands for iterated function system. The general structure of affine transformation is set up by three parts. The first part is the matrix which controls the angle of the stem, the angle of each piece of leaf. And then the matrix will multiply by \( (\begin{matrix}x \\ y \\ \end{matrix}) \) [8]. The last part of this function is the translation. The purpose of this part is to control the displacement of the point. This means that this part decides the distance that the point will move in X direction and in Y direction. This transformation only happened in \( {R^{2}}* {R^{2}} \) , which also means that this is a two-dimensional transformation. To conclude this the basic affine transformation looks like this: \( (\begin{matrix}a & b \\ c & d \\ \end{matrix})(\begin{matrix}x \\ y \\ \end{matrix})+(\begin{matrix}e \\ f \\ \end{matrix}) \) [8]. And this is a basic second order matrix used to control the changes in the angle of the movement of the point or pieces in a fractal object. For example, if the author wants the angle to be α, the matrix should look like this: \( (\begin{matrix}cosα & -sinα \\ sinα & cosα \\ \end{matrix}) \) . However, in a more complex fractal object and in fractal coding people usually use third-order matrix, this is because in fractal coding, programmers usually use third-order affine transformation. The simple form of third-order affine transformation is:
\( [\begin{matrix}a & b & 0 \\ c & d & 0 \\ 0 & 0 & p \\ \end{matrix}][\begin{matrix}x \\ y \\ z \\ \end{matrix}] \) + \( [\begin{matrix}e \\ f \\ g \\ \end{matrix}] \) [9].(1)
To conclude, the three-dimensional affine transformation could just be seen as a two-dimensional affine transformation that involves the z-axis. Furthermore, a third-order affine transformation is quite useful in adjusting the angle of some pieces in a specific fractal object. For example, in Barnsley Fern, when people use third order matrix instead of second order matrix, people can adjust the angle that stem and leaves bending [10]. For example, those two pictures come from IFS playground.


Figure 1. The effect of changing the angle.
In the Iterated Function System, there are four third-order affine transformations. Only one of them controls the angle, which is
\( [\begin{matrix}0.85 & -a & 0 \\ a & 0.85 & 0 \\ 0 & 0 & 1.6 \\ \end{matrix}] \) . (2)
In doing so, by adjusting the value of a, people can change the angle that the leaves bend. So, in Figure 1 on the left, the value of a is 0.04. and in the right-hand side picture, the value of a is 0.17. There is also the difference between the chances that each equation can happen. For example, the picture on the left hand has four different affine transformations. However, the probability of each formula happening is different. The probability of each transformation happening is 0.01, 0.85, 0.07, and 0.07.
2.2. The contracting mapping theory
Contracting is a transformation that shrinks or shortens the distance of two objects. Let f: \( X*X \) be terrible on the metric space (X, d) Change, if there is a constant 0≤S < 1, such that \( d((f x),(f y))≤S· d(x,y) \) . There is another key term in contracting mapping theorem is unique fixed point. In the collage, the theorem is that the object after several transformations the object that formed looks similar or identical to the original object. In doing so, that object will call a unique fixed point. In a picture that unique fixed point the point doesn’t change after several transformations like contraction, shrink, rotation, and translation.
2.3. Chaos game
This game explained the reason why chaos and order both appeared in Fractal. The rule this like this: There are n points 1, 2, 3..., n in the plane; randomly select a point P in the plane and randomly generate a string of random numbers containing these numbers. If the random number is 1, then the paper let this point move towards Go half way to 1, and if it’s 2, go half way to 2... Usually players throw dices to generate random numbers. For example, when n=3, Serpinski Triangle as shown in Figure 2.
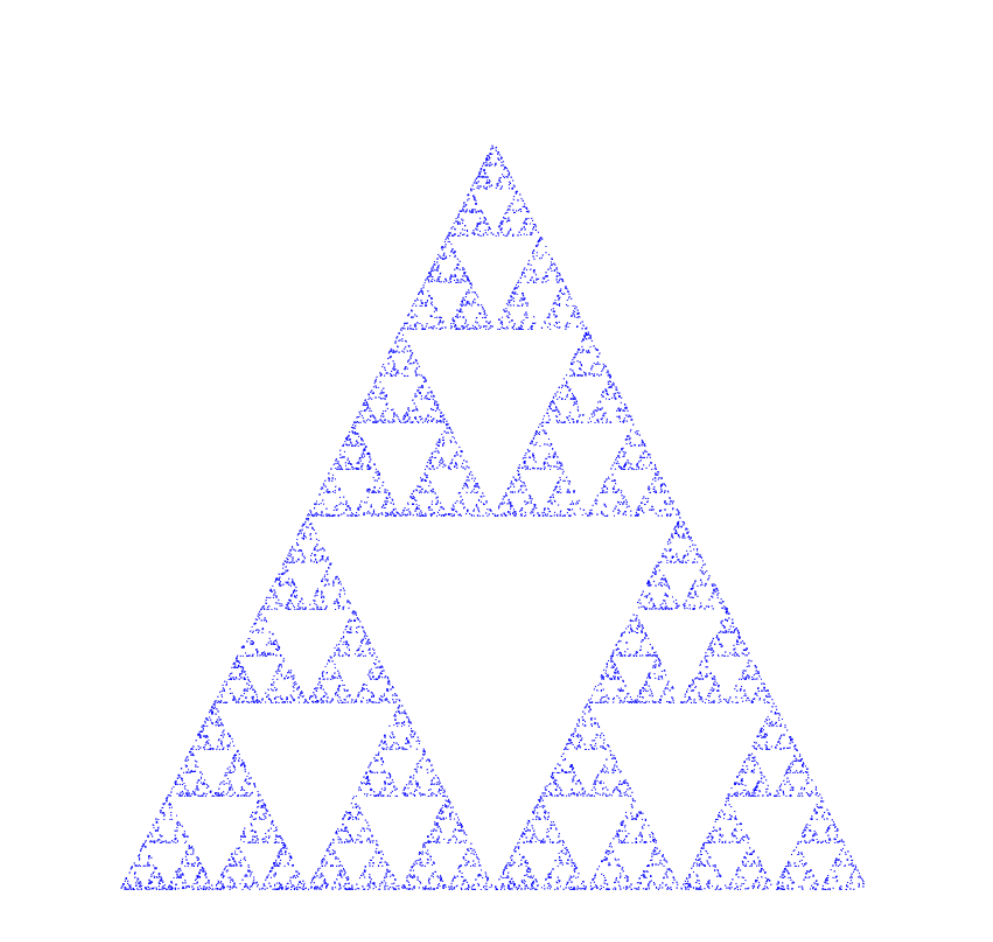
Figure 2. The finial result when n=3.
3. The application
Fractal coding of images is a new coding technology that uses cross-scale similarities between different areas in real images to reduce image data redundancy. It breaks through the previous image coding framework and uses a function to describe the entire image, cleverly Applying fractal self-similarity to image coding to achieve good compression results.
The concept box-counting dimension is used in picture processing. This type of method increases the speed of the coding and processing process. However, building up a fractal code requires lots of time. This is because researchers need to find the best match block in the database. But this type of method can help programmer throw away those block that doesn’t match what researchers require.
Meanwhile, some mathematician suggests that researchers can use an LIC chaotic system to compress and encrypt the picture. A chaotic system is a mathematical model or equation describing chaotic behavior, which has characteristics such as randomness, unpredictability, and nonlinearity, and can meet the requirements of image encryption. LIC chaotic system only contains low calculated amounts. This is because most of the calculation is based on one-dimensional chaotic system. And due to the property of chaos, safety is not an issue.
Besides the LIC system, there is also an encoding system that could be used in encryption which is called Spiht encoding. This method uses an image coding method that combines wavelet and fractal to compress images, and based on this, a chaotic encryption technology algorithm is proposed.
Aside from Spiht encoding, finding sub-block differences shortens the coding process. What the box dimension do is split a picture into several different blocks and separate it into important and not essential part. Then researchers will match those blocks with the database separately. In doing so, the computer won’t process overload and deal with too much stuff at once. But, this type of method sacrificed some amount of quality of the picture in not important part.
There is another fast compression coding method as well. This method builds up a small dictionary which is used for increasing the coding process. Then use Julia’s set to complete the dictionary. The conception, design, implementation, and application of using commonly used fractal coding dictionaries, coding dictionaries composed of Julia image block sets, and average image coding dictionaries to replace the always-changing fractal image compression coding dictionaries.
This method not only increases the speed but also increases the quality of the figure than the common method. This method studies the fractal image texture detail enhancement technology that considers gradient edge information and proposes a fractal image texture detail enhancement algorithm that considers gradient edge information. And it can show more and better details in a picture.
And the last application that I want to talk about is used in producing fragile watermarking. The algorithm can effectively detect whether the image has been maliciously tampered with, and different host images can produce different chaotic binary watermarks, which strengthens the confidentiality of the algorithm and has more obvious advantages when processing large batches of images.
4. Conclusion
The method that introduces Fractal into photo processing has a lot of benefits. First, it can save art expenses. For example, researchers can use fractals to draw tons of patterns such as lightning, tree branches, snowflakes, carpets, flames, starry sky, grass, etc., and just slightly adjust a few parameters to make the entire picture look completely different. It is undoubtedly unrealistic to use human power to draw one by one. If researchers use a randomly generated method, they will face various rendering results that look unnatural, messy, or lack beauty, and the rendering speed will also be relatively slow. Meanwhile, after several generations and improvements, the speed of photo processing increased a lot. The speed of encryption boosts as well. However, there are also several disadvantages. For example, there is still a serious block effect in the restored image. Furthermore, it is quite easy to be affected by the noise, less important and no meaning block.
References
[1]. Yao Z, Hongxing W, Baozong Y 2000 Doctoral dissertation
[2]. Jiaqi W, Miao Z, Xiaoyun T, Zhu W 2022 Application Research of Computers Jisuanji Yingyong Yanjiu 39 12
[3]. Hua Z, Zhou Y 2016 Infor.Sci. 39 237-253
[4]. Haq T, Shah T 2021 J. of Infor. Secu. and Applications 61 102931
[5]. Deping Z, Zhi G, Lijia G 2002 J. of North. Uni. Natural Science Edition 23 9 825
[6]. Junjia Y, Wenbo L 2015 Electronic Measurement Technology 6 64-67
[7]. Min H, Haimin Z, Fei C 2022 J. of Tonghua Normal University 10 6-12
[8]. Sainan X, Mengchao D, Zhangfan Z, Tianqi Y 2023 Sci. and Tech. Innovation and Application 01
[9]. Chuanjiang H, Juanjuan H, Gaoping L 2007 Chinese J. of Image and Graphics 02
[10]. Ruisong Y, Yueming C 2023 J. of Shantou University Natural Science Edition 02
Cite this article
Bian,H. (2023). The application of fractal and chaos theory in photo processing. Theoretical and Natural Science,25,78-82.
Data availability
The datasets used and/or analyzed during the current study will be available from the authors upon reasonable request.
Disclaimer/Publisher's Note
The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of EWA Publishing and/or the editor(s). EWA Publishing and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content.
About volume
Volume title: Proceedings of the 3rd International Conference on Computing Innovation and Applied Physics
© 2024 by the author(s). Licensee EWA Publishing, Oxford, UK. This article is an open access article distributed under the terms and
conditions of the Creative Commons Attribution (CC BY) license. Authors who
publish this series agree to the following terms:
1. Authors retain copyright and grant the series right of first publication with the work simultaneously licensed under a Creative Commons
Attribution License that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this
series.
2. Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the series's published
version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial
publication in this series.
3. Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and
during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work (See
Open access policy for details).
References
[1]. Yao Z, Hongxing W, Baozong Y 2000 Doctoral dissertation
[2]. Jiaqi W, Miao Z, Xiaoyun T, Zhu W 2022 Application Research of Computers Jisuanji Yingyong Yanjiu 39 12
[3]. Hua Z, Zhou Y 2016 Infor.Sci. 39 237-253
[4]. Haq T, Shah T 2021 J. of Infor. Secu. and Applications 61 102931
[5]. Deping Z, Zhi G, Lijia G 2002 J. of North. Uni. Natural Science Edition 23 9 825
[6]. Junjia Y, Wenbo L 2015 Electronic Measurement Technology 6 64-67
[7]. Min H, Haimin Z, Fei C 2022 J. of Tonghua Normal University 10 6-12
[8]. Sainan X, Mengchao D, Zhangfan Z, Tianqi Y 2023 Sci. and Tech. Innovation and Application 01
[9]. Chuanjiang H, Juanjuan H, Gaoping L 2007 Chinese J. of Image and Graphics 02
[10]. Ruisong Y, Yueming C 2023 J. of Shantou University Natural Science Edition 02









