1. Introduction
Fraud refers to that when an individual deliberately misrepresents facts for their benefit by “promising to provide goods, services or other financial benefits that do not exist or are not intended to be provided”, and attempts to mislead another person [1]. Fraud is a common and serious social "sickness" in the world [2]. According to statistics, the annual loss caused by fraud in the world reaches 5.127 trillion US dollars. Fraud affects millions of people and bears huge costs for individuals and society [3,4].
With the popularization of the Internet, a new type of fraudulent method— telecommunication fraud was born and became more and more popular among fraudsters. Telecom fraud refers to using modern technology and the means of communication to obtain people's information and commit fraud crimes against people. This includes, but is not limited to, fraud through social networking platforms, gaming platforms, job hunting platforms, or direct phone calls [5]. Telecommunication services have penetrated every aspect of people's daily lives. While it brings convenience to people, it is also used by criminals. With the intervention of high-tech communication tools, the scope of the crime and the number of objects is far more than the ordinary fraud crime [6]. Nowadays, telecommunications fraud has become the main method of fraud for criminal gangs, and more and more people have been harmed by telecom fraud. The "Telecom and Internet Fraud Judicial Big Data Report" shows that the number of Internet fraud cases from 2016 to 2018 ranked first among all cybercrimes, accounting for more than 30%. In addition to frequent cases, losses are also increasing. According to statistics, from 2014 to 2019, the per capita loss caused by online fraud has increased year by year. In 2019, the per capita loss reached 24,549 yuan, a record high. Internet fraud has become a recognized "social cancer" and a social nuisance that violates the safety of citizens' property [7].
Nowadays, there are numerous studies on telecom fraud, but most of them focus on the prediction and analysis of telephone fraud. For example, Yu Chenchen et al. focus on using AI@TSS technology (Intelligent Technical Support Scam Aware System) to predict and analyze telecom fraud [8]; Xu Hongkui used the BilSTM of Attention mechanism to predict fraud calls [9]; Yang Jiankun does the research from another perspective, based on user behavior analysis to identify fraud phone [10].
Although it is very meaningful to use artificial intelligence to automatically detect and block telecom fraud, today, we can't totally rely on AI to do this kind of work, and their efficiency is far from enough [11]. At present, there is very little research on the “people” part of telecom fraud, that is research about what internal or external factor may lead a person to be telecom frauded, that is, what factors may lead people to be cheated by telecom fraud, and this kind of research is also very important. In the face of telecom fraud, the most important part is the people to make decisions [12], and "people" are the weakest part of these fraud prevention links. Lots of focus should be put on the “people” ’s perspective when study on the topic of telecom frauds.
2. Literature Review
2.1. Previous Research on Cognitive Ability
Cognitive ability refers to the ability to accept, understand, analyze, and use knowledge. Cognitive ability plays an essential role in the personal characteristics of middle-aged and elderly people [13]. Judges and Gamble, argue that aging causes cognitive decline in middle-aged and older people and that the aging brain increases the likelihood of deceptions and the number of such deceptions. Gamble et al also argues that objective and subjective financial literacy decrease with cognitive decline in older adults, which directly leads to greater vulnerability to fraud [14,15]. James also reached a similar conclusion and found a clear negative correlation between financial literacy and the probability of fraud in the elderly [16].
2.2. Previous Research on Cognitive Flexibility and Critical Thinking
Cognitive flexibility is a kind of cognitive ability, and it is very important. Cognitive flexibility refers to an individual's ability to change cognition freely in response to different stimuli or environmental changes [17]. Research has shown that people with higher cognitive flexibility have the stronger problem-solving ability, interpersonal communication ability, and more comprehensive coping styles [18]. And that gave an insight that cognitive flexibility can be an important reason to decide whether an individual is gullible.
Critical thinking reflects the rational reflection ability of individuals. People with strong critical thinking are good at evaluating, analyzing, and interpreting problems from multiple perspectives, comprehensively considering the evidence, concepts, background knowledge, and other information, and have highly complex thinking abilities and Cognitive characteristics [19]. A related study has found that gullible people have lower cognitive complexity and poorer thinking skills than other people [20]. That gave an insight that critical thinking may be a factor that impacts people’s vulnerability to fraud.
2.3. Previous Research on Material Desire
Material desire refers to the willingness to pursue material, such as money or luxury. When people are overly focused on their instinctual needs and desires (such as monetary rewards), their actions are often intuitive and instinct-driven, lack thoughtfulness, and tend to ignore the consequences of their actions [21], which means once a fraud victim’s greed or other instinctual motives are activated, thinking about the legitimacy of a transaction other than money or other rewards is greatly reduced or even eliminated.
3. Hypothesis Development
3.1. Negative Impact of Cognitive Flexibility on Vulnerability Toward Telecom Fraud
People with high cognitive flexibility can quickly become aware of their environment, and they can adjust their cognition even when the environment changes [17]. Thus, people with high cognitive flexibility tend to be more flexible in their thinking. When wire fraud occurs, the scammer often creates a specific situation for the victim, which can lead them to fall into the trap. Cognitively flexible people are more likely than others to be aware of the scammer's trap and avoid being scammed.
Hypothesis 1: Cognitive flexibility is negatively correlated with vulnerability to telecom fraud; that is, the higher the cognitive flexibility, the less vulnerability to telecom fraud.
3.2. Negative Impact of Critical Thinking on Vulnerability toward Telecom Fraud
Critical thinkers tend to consider multiple aspects of an event. When in a telecom scam, people with strong critical thinking tend to not believe what the liar said and suspect the veracity of what the liar said. Therefore, people with critical thinking are often more difficult than others to scam.
Hypothesis 2: There is a negative correlation between critical thinking and vulnerability to telecom fraud, that is, the more critical thinking, the lower the vulnerability to telecom fraud.
3.3. Moderating Effect of Material Motive on the Relationship between Independent Variables and Vulnerability to Telecom Fraud
People who pursue material interests more often lack reason when pursuing the material they want [21]. In scams, scammers often throw out benefits to lure people into the scam. Those who pursue profits are often more affected by this temptation and thus fall into the trap of liars.
Hypothesis 3: Material interest pursuit plays a negative moderating effect between cognitive flexibility and vulnerability to telecom fraud, that is, the stronger the material interest pursuit, the less the effect of cognitive flexibility to vulnerability to telecom fraud.
Hypothesis 4: Material interest pursuit plays a negative moderating effect between critical thinking and vulnerability to telecom fraud, that is, the stronger the material interest pursuit, the less the effect of critical thinking on vulnerability to telecom fraud.
3.4. Effect of Social Attributes on Vulnerability to Telecom Fraud
Individual social attributes are different, and these differences can easily become factors affecting everyone's thinking patterns and behaviors. Therefore, in our research model, we believe that each person's social status, for example, age, education, work status, marital status, etc., will affect their vulnerability to telecom fraud. Because the influence of social attributes is not the focus of this study, it will be conducted data analysis and draw insights, but no hypothesis test on it.
4. Methodology
4.1. Research Design
The cross-sectional design is adopted in this study (that is, multiple objects are investigated and measured at the same time). Since the factors of variables we attempt to measure will not change in a short time, the influence of time on the experiment can be ignored in the study. After obtaining all the data indicators required for the same period, we will conduct a hypothesis testing analysis and finally get the results.
4.2. Samples and Sampling Methods
The main research object of this study is towards Chinese people, so we will conduct a sample survey in this group. This study intends to use the method of distributing questionnaires online. The advantages of this method are 1, widespread, and not limited by geographical factors. Since our research object is Chinese people, to eliminate the problem that the samples obtained from a single region may not represent the whole population, it needs to invite people in several cities across the country to fill out the questionnaires, which can be easily solved through an online questionnaire. 2, easy to collect and analyze, and the online questionnaire is more conducive to statistical and analytical work after collecting samples.
4.3. Questionnaire Design
4.3.1. Material Desire
This study uses the Materialism Values Scale compiled by Li Jing and Guo Yongyu, which includes 13 questions, of which 5 are reversed. This scale can accurately measure people's material desire dimension with concise questions.
4.3.2. Cognitive Flexibility
The Chinese version compiled by Dennis and Vander Wal and revised by Wang et al. [22] was adopted to measure cognitive flexibility. The scale includes 20 questions.
4.3.3. Critical Thinking
This research questionnaire adopts the simplified version of the Chinese Critical Thinking Trait Scale that Huang used in her research [23]. The full version of the Critical Thinking Inventory (CTDI-CV) has a total of 70 questions. Too many questions may cause fatigue and boredom among the respondents, which is not suitable for questionnaire sampling. The simplified version of the critical thinking scale collects the most representative 18 questions in the full version of the scale so that it can accurately measure the characteristics of critical thinking, and it is more conducive to the filling and collection of questionnaire data.
4.3.4. Vulnerability to Telecom Fraud
We intend to ask respondents if they have been victimized by telecom fraud (e.g., swiping part-time scams, game top-up scams, impersonating customer service fraud, public security law fraud, etc.), how many times have they suffered, and the amount of property they have lost, to measure the individual’s vulnerability to fraud.
The questionnaire uses the 6-point Likert scale, which avoids people's more neutral attitude in choosing options than a five-point scale [24], thereby avoiding the situation where most people choose the middle option without expressing their attitude. At the same time, to avoid the situation where someone fills in the questionnaire casually, this questionnaire sets a screening question in the middle of the question –– what is the number “2” plus “3” equal, questionnaire with an option other than “5” will be excluded from the data analysis. This can greatly improve the reliability of the questionnaire.
5. Data Analysis & Hypothesis Test Results
5.1. Descriptive Statistics
A total of 307 questionnaires were collected in this questionnaire survey, but one of the questionnaires chose the wrong answer to the screening questions. This questionnaire was filled casually and will not be included in the data analysis. Therefore, the total number of questionnaires we received was 306. As shown in chart 1, among the 306 people, 123 had the experience of being scammed by telecommunications, and 183 had no experience of being scammed by telecommunications.
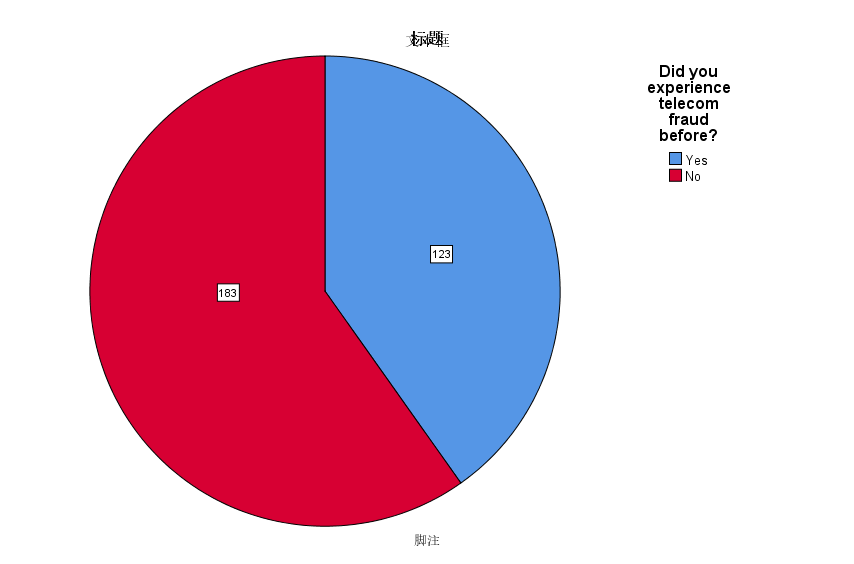
Figure 1: Distribution of Experience of Telecom Fraud.
5.2. Preprocessing of the Data
When measuring "cognitive flexibility", "critical thinking" and "material desire", the relevant forward questions are summed, the scores of all reverse questions are subtracted, and the final average is obtained to represent the value of the variable. When measuring the score of "vulnerability to telecom fraud", those who have never experienced telecom fraud are recorded as "0" points. At the same time, research also included the amount of loss of property by telecom fraud in the scoring item. The more the amount, the higher the score. Finally, we averaged the scores for "Number of Telecom Frauds Experienced" and "Amount of Property loss in Telecom Fraud" to get a score for "Vulnerability to Telecom Fraud".
Because most people have no experience of being scammed by telecommunications, this leads to a large part of the data in the variable of " Vulnerability to Telecom Fraud" being "0", which makes the data extremely unbalanced, and not conducive to the subsequent hypothesis testing analysis. Therefore, the data needs to be balanced. 85 pieces of data are randomly deleted from the data of people who have not experienced telecom fraud, so as to obtain relatively balanced data.
5.3. Correlation & Hypothesis Test Results
Correlation analysis was performed on the processed data, and the results showed in Table 1. From the matrix, we can see that vulnerability to telecom fraud has a significant negative correlation with both cognitive flexibility and critical thinking, but its relationship with material desire is not statistically significant. At the same time, cognitive flexibility was also significantly positively correlated with critical thinking, and critical thinking was significantly negatively correlated with material desire.
Table 1: Correlation Matrix.
|
| Cognitive Flexibility | Material Desire | Critical Thinking | Vulnerability to Telecom Fraud |
Cognitive Flexibility | 1 | ||||
Material Desire | 0.148 | 1 | |||
Critical Thinking | -0.598 | -0.171 | 1 | ||
Vulnerability to Telecom Fraud | -0.188 | -0.04 | -0.157 | 1 | |
**Correlation is significant at the 0.01 level (2-tailed) | |||||
*Correlation is significant at the 0.05 level (2-tailed) |
|
|
|
| |
5.3.1. The Direct Effect of Cognitive Flexibility& Critical Thinking on Vulnerability to Telecom Fraud
In the linear regression analysis of cognitive flexibility and vulnerability to telecom fraud, the normalized beta was -0.188, and the p-value was equal to 0.017 (<0.05); this indicates that cognitive flexibility has a statistically significant negative effect on vulnerability to telecom fraud; that is, the higher a person's cognitive flexibility, the less susceptible he is to telecom fraud. As a result, Hypothesis 1 is supported.
Similarly, in the linear regression analysis of critical thinking on vulnerability to telecom fraud, the results showed that the adjusted beta was -0.157, and the p-value was equal to 0.047 (<0.05), and there was also a statistically significant negative linear relationship between two variables, which means that the more critical a person is, the less susceptible he is to telecom fraud. Therefore hypothesis 2 is supported.
5.3.2. The Moderating Effect of Material Desire on Relationship between Independent Variables and Vulnerability to Fraud
In this study, the moderating effect was tested by examining the variation of the R-square before and after the introduction of the interaction term between the independent variables and the moderating variable. In the measurement of the moderating effect of material desire on perceived flexibility and susceptibility to telecommunications fraud, the R-square before and after the introduction of the interaction term did not change significantly (p=0.09, >0.05), so the material desire doesn’t have a statistically significant impact on the relationship between cognitive flexibility and vulnerability to telecom fraud (p=0.09, >0.05). Similarly, when studying the moderating effect of material desire on the other group, the R-square before and after the introduction of the interaction term was not significant either (p=0.313,>0.05), so the relationship between critical thinking and vulnerability to telecom fraud is also not impacted by material desire significantly. Therefore, Hypothesis 3 and Hypothesis 4 are rejected.
Table 2: Hypothesis Test Result.
Hypotheses | Test Results | Significant level (P Value) |
Hypothesis 1 | Supported | 0.017 |
Hypothesis 2 | Supported | 0.047 |
Hypothesis 3 | Rejected | 0.090 |
Hypothesis 4 | Rejected | 0.313 |
5.3.3. The Effect of Social Attributes on Vulnerability to Telecom Fraud
We use ONE-WAY ANOVA to determine whether social attributes are a factor that affects a person's vulnerability to telecom fraud. We separately analyzed “gender”, “age”, “education level”, “employment status”, “marital status”, “number of household members”, and “disposable income” to explore whether these factors affect a person's vulnerability to wire fraud. Through ONE-WAY ANOVA analysis, we found that there is no difference in vulnerability to telecom fraud among groups of different gender, ages, education levels, work status, marital status, and the number of household members (p>0.05); however, among people with different disposable incomes, their vulnerability to telecom fraud is different, and the ANOVA test results are statistically significant, with a p-value of 0.0001 (<0.05). Through further POST HOC TEST, we found that this difference mainly comes from people with a monthly disposable income of 20,000 yuan. Through figure 1, we can find that people with a monthly income of more than 20,000 yuan are more vulnerable to telecom fraud.
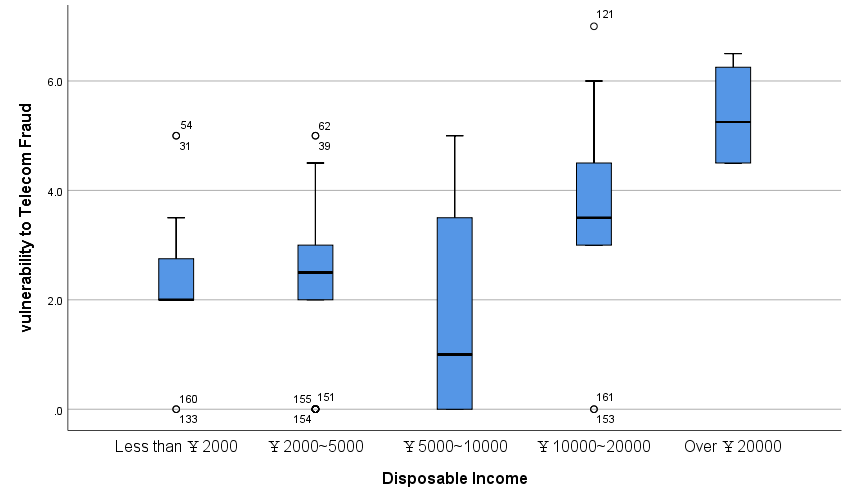
Figure 2: Distribution of Vulnerability to Telecom Fraud in Different Disposable Income.
Table 3: ANOVA Test Result.
Social Status | Whether an Influencing Factor | ANOVA Test Significance |
Gender | NO | p=0.74 |
Age | NO | p=0.69 |
Education Level | NO | p=0.94 |
employment status | NO | p=0.87 |
marital status | NO | p=0.09 |
household members | NO | p=0.14 |
disposable income | YES | p=0.00 |
6. Discussion& Recommendation
Through the results of the research, it can be seen that the improvement of critical thinking and cognitive flexibility can reduce the probability of people being scammed. Relevant departments can use this article as theoretical support to focus on anti-fraud propaganda for specific groups of people, the basic of anti-fraud is to start with the public. The relevant departments can design specific activities or promotional videos to emphasize the importance of cognitive flexibility and critical thinking and hold activities to improve the public’s cognitive flexibility and critical thinking. At the same time, the relevant departments should also focus on groups of people who lack these two characteristics and focus on their education and publicity to effectively carry out anti-fraud work.
This study also pointed out that high-income people are more vulnerable to fraud than other groups, which may be because high-income people experience more scams, and the amount of money they are defrauded each time is larger, which makes them more likely to become victims than others. The anti-fraud department should pay more attention to the fraudulent situation of high-income groups to effectively prevent more losses.
In addition, this study can be used as a reference for related research in the future. When studying factors affecting fraud or researching models for predicting fraud, this study can be used as a reference for more in-depth research.
7. Limitation of the Research
This study used the method of a questionnaire survey to obtain data. Although this method is relatively simple and efficient and can obtain primary data, it has some shortcomings. First, the information filled in by the respondents is not necessarily true. They were all defrauded in the past, and their mental characteristics surveyed in the questionnaire are their current characteristics. They may have changed their mental characteristics over time, which can lead to inaccuracies in the data we measure, especially when they experienced telecom fraud long ago.
In addition, the respondents of the questionnaire may intentionally or accidentally fill in some data incorrectly. For example, when investigating whether they have been frauded before, the interviewees may not be willing to admit the fact that they have been frauded, or they may not be aware of it [25, 26], on the other hand, some individuals who have not experienced telecom fraud may not be because they are not easy to fraud, but because they have not encountered the corresponding fraud situation. These situations can make data can't represent the fact [27].
In addition, due to the limited time for collecting the questionnaires, we only collected 306 valid questionnaires in total. Although this is sufficient for data analysis and conclusions, the persuasiveness in many places is still limited.
8. Conclusion
This study focused on investigating the influence of internal factors on vulnerability to telecom fraud. The data were collected through the questionnaire survey, and SPSS 25.0 was used for questionnaire data analysis. Finally, it was concluded that both cognitive flexibility and critical thinking had a direct negative effect on vulnerability to wire fraud, and material desires did not affect the effectiveness of the two variables on vulnerability to telecom fraud; that is, the higher a person's cognitive flexibility and critical thinking, the less likely he is to be telecom scammed, and the relationship is not affected by the person's material desires.
This study introduces the number of times experiencing frauds and the amount of property being frauded, and uses the method of aggregating and averaging to change the binary variable of "whether you have been frauded " into a linear variable —"vulnerability to telecom fraud", this step makes the dependent variable refined, and then their relationship with the growth and change of thinking characteristics is analyzed. This study can provide a reference for further policy and scholars in the related fields of fraud prevention.
At present, the types of telecommunications fraud have not been classified in this study. The influencing factors of different types of telecom fraud may be different. Scholars who conduct related research in the future can consider further in-depth types of telecom frauds. In addition, future research can also study the external characteristics that affect the degree of fraud, and combine internal and external factors to better forecast telecom frauds using machine learning and artificial intelligence.
References
[1]. Titus, R. M., Heinzelmann, F., Boyle, J. M. :Victimization of persons by fraud. Crime & Delinquency, 41(1), 54-72(1995).
[2]. Pak, K., & Shadel, D.: The psychology of consumer fraud. The TAO Institute(2007).
[3]. Gee, J., & Button, M. :The financial cost of fraud 2019: The latest data from around the world(2019).
[4]. Mueller, E. A., Wood, S. A., Hanoch, Y., Huang, Y., Reed, C. L.: Older and wiser: age differences in susceptibility to investment fraud: the protective role of emotional intelligence. Journal of elder abuse & neglect, 32(2), 152-172 (2020).
[5]. Li, C., & Liang, X.: Research On The Comprehensive Governance Of Telecommunications Network Fraud. In 2018 3rd International Conference on Humanities Science, Management and Education Technology (HSMET 2018). Atlantis Press (2018).
[6]. Zhang, J. :A Case Analysis on Fraud Crime through Phone. University of Chongqing(2012).
[7]. Ni, P., Wang, Q.: Internet and Telecommunication Fraud Prevention Analysis based on Deep Learning. Applied Artificial Intelligencee, 36:1, 2137630, DOI: 10.1080/08839514.2022.2137630 (2022)
[8]. Chen, Y., Chen, J., Ma, Y.: AI@TSS- Intelligent technical support scam detection system. Journal of Information Security and Applications(2021).
[9]. Xu Hongkui, Jiang Tongtong, Li Xin, Zhou Junjie, Zhang Zifeng, Lu Jiangkun.: BiLSTM Scam Call Recognition Based on Attention Mechanism. Computer System Applications (03), 326-332. doi: 10.15888/j.cnki.csa. 008385 (2022).
[10]. Yang Jiankun , Xia Wencai.: Fraud phone call identification based on user behavior analysis. Computer System Applications (08), 311-316. doi: 10.15888/j.cnki.csa.007922(2021).
[11]. Marriott, C.: Through the Net: Investigating How User Characteristics Influence Susceptibility to Phishing (2018).
[12]. Alghamdi, H. :Can Phishing Education Enable Users To Recognise Phishing Attacks? Dublin Institute of Technology, School of Computing(2017)..
[13]. Wu, X.: Research on the influencing factors of financial fraud losses suffered. Market weekly, p. 118(2022)
[14]. Judges, R. A., Gallant, N. S., & Yang, L.: The role of cognition, personality, and trust in fraud victimization in older adults. Frontiers in Psychology, 275-282 (2017).
[15]. Gamble, K., Boyle PA, & YU, l.:Aging, financial literacy, and fraud. Electronic Journal(2013).
[16]. James , B., Boyle, P., & Bennett, D.:Correlates of susceptibility to scams in older adults without dementia. J Elder Abuse Negl, p. 107-122(2014).
[17]. Dennis JP., Wal JSV.: The cognitive flexibility inventory: instrument development and estimates of reliability and validity[J]. Cognitive Therapy and Research, 241-253(2010).
[18]. Zhao Bing. A study on the relationship between cognitive flexibility and school adaptation for freshmen [D]. Baoding: Hebei University (2011).
[19]. Facione, P.: Critical thinking: A statement of expert consensus for purposes of educational assessment and instruction (The Delphi Report) (1990).
[20]. Kirwan, G. H., Fullwood, C., & Rooney, B. :Risk factors for social networking site scam victimization among Malaysian students. Cyberpsychology, Behavior, and Social Networking, 21(2), 123-128(2017).
[21]. Langenderfer, J., & Shimp, T. A.: Consumer vulnerability to scams, swindles, and fraud: A new theory of visceral influences on persuasion. Psychology & Marketing, 18(7), 763-783 (2001).
[22]. Wang Yang, Yang Yan, Xiao Wanting & Su Qin.:Validity and reliability of the Chinese version of the Cognitive Flexibility Questionnaire for evaluating college students. Chinese Journal of Mental Health (01), 58-63(2016).
[23]. Huang Xiuyun.: The Chinese version of the Critical Thinking Trait Scale was tested in Taiwanese clinical nurses. Degree thesis of the Department of Nursing, National Cheng Kung University (2008).
[24]. Xia, T.: Research on the Influencing Factors of College Students' Video Game Krypton Gold Behavior Based on Technology Acceptance Model. Shanghai Normal University Master's Thesis (2021).
[25]. Button, M., Nicholls, C. M., Kerr, J., & Owen, R.: Online frauds: Learning from victims why they fall for these scams. Australian & New Zealand journal of criminology, 47(3), 391-408(2014).
[26]. Deliema, M., Shadel, D., Pak, K.: Profiling victims of investment fraud: Mindsets and risky behaviors. Journal of Consumer Research, 46(5), 904-914 (2020).
[27]. Deevy, M., Lucich, S., & Beals, M. Scams, schemes & swindles: a research review of consumer financial fraud. Financial Fraud Research Center. http://longevity3.stanford.edu/wp-content/uploads/2014/01/Scams-Schemes Swindles-FINAL-On-Website.pdf, (2012).
Cite this article
Wei,Z. (2023). Internal Factors Influencing Vulnerability to Telecom Fraud. Advances in Economics, Management and Political Sciences,6,438-447.
Data availability
The datasets used and/or analyzed during the current study will be available from the authors upon reasonable request.
Disclaimer/Publisher's Note
The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of EWA Publishing and/or the editor(s). EWA Publishing and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content.
About volume
Volume title: Proceedings of the 2022 International Conference on Financial Technology and Business Analysis (ICFTBA 2022), Part 2
© 2024 by the author(s). Licensee EWA Publishing, Oxford, UK. This article is an open access article distributed under the terms and
conditions of the Creative Commons Attribution (CC BY) license. Authors who
publish this series agree to the following terms:
1. Authors retain copyright and grant the series right of first publication with the work simultaneously licensed under a Creative Commons
Attribution License that allows others to share the work with an acknowledgment of the work's authorship and initial publication in this
series.
2. Authors are able to enter into separate, additional contractual arrangements for the non-exclusive distribution of the series's published
version of the work (e.g., post it to an institutional repository or publish it in a book), with an acknowledgment of its initial
publication in this series.
3. Authors are permitted and encouraged to post their work online (e.g., in institutional repositories or on their website) prior to and
during the submission process, as it can lead to productive exchanges, as well as earlier and greater citation of published work (See
Open access policy for details).
References
[1]. Titus, R. M., Heinzelmann, F., Boyle, J. M. :Victimization of persons by fraud. Crime & Delinquency, 41(1), 54-72(1995).
[2]. Pak, K., & Shadel, D.: The psychology of consumer fraud. The TAO Institute(2007).
[3]. Gee, J., & Button, M. :The financial cost of fraud 2019: The latest data from around the world(2019).
[4]. Mueller, E. A., Wood, S. A., Hanoch, Y., Huang, Y., Reed, C. L.: Older and wiser: age differences in susceptibility to investment fraud: the protective role of emotional intelligence. Journal of elder abuse & neglect, 32(2), 152-172 (2020).
[5]. Li, C., & Liang, X.: Research On The Comprehensive Governance Of Telecommunications Network Fraud. In 2018 3rd International Conference on Humanities Science, Management and Education Technology (HSMET 2018). Atlantis Press (2018).
[6]. Zhang, J. :A Case Analysis on Fraud Crime through Phone. University of Chongqing(2012).
[7]. Ni, P., Wang, Q.: Internet and Telecommunication Fraud Prevention Analysis based on Deep Learning. Applied Artificial Intelligencee, 36:1, 2137630, DOI: 10.1080/08839514.2022.2137630 (2022)
[8]. Chen, Y., Chen, J., Ma, Y.: AI@TSS- Intelligent technical support scam detection system. Journal of Information Security and Applications(2021).
[9]. Xu Hongkui, Jiang Tongtong, Li Xin, Zhou Junjie, Zhang Zifeng, Lu Jiangkun.: BiLSTM Scam Call Recognition Based on Attention Mechanism. Computer System Applications (03), 326-332. doi: 10.15888/j.cnki.csa. 008385 (2022).
[10]. Yang Jiankun , Xia Wencai.: Fraud phone call identification based on user behavior analysis. Computer System Applications (08), 311-316. doi: 10.15888/j.cnki.csa.007922(2021).
[11]. Marriott, C.: Through the Net: Investigating How User Characteristics Influence Susceptibility to Phishing (2018).
[12]. Alghamdi, H. :Can Phishing Education Enable Users To Recognise Phishing Attacks? Dublin Institute of Technology, School of Computing(2017)..
[13]. Wu, X.: Research on the influencing factors of financial fraud losses suffered. Market weekly, p. 118(2022)
[14]. Judges, R. A., Gallant, N. S., & Yang, L.: The role of cognition, personality, and trust in fraud victimization in older adults. Frontiers in Psychology, 275-282 (2017).
[15]. Gamble, K., Boyle PA, & YU, l.:Aging, financial literacy, and fraud. Electronic Journal(2013).
[16]. James , B., Boyle, P., & Bennett, D.:Correlates of susceptibility to scams in older adults without dementia. J Elder Abuse Negl, p. 107-122(2014).
[17]. Dennis JP., Wal JSV.: The cognitive flexibility inventory: instrument development and estimates of reliability and validity[J]. Cognitive Therapy and Research, 241-253(2010).
[18]. Zhao Bing. A study on the relationship between cognitive flexibility and school adaptation for freshmen [D]. Baoding: Hebei University (2011).
[19]. Facione, P.: Critical thinking: A statement of expert consensus for purposes of educational assessment and instruction (The Delphi Report) (1990).
[20]. Kirwan, G. H., Fullwood, C., & Rooney, B. :Risk factors for social networking site scam victimization among Malaysian students. Cyberpsychology, Behavior, and Social Networking, 21(2), 123-128(2017).
[21]. Langenderfer, J., & Shimp, T. A.: Consumer vulnerability to scams, swindles, and fraud: A new theory of visceral influences on persuasion. Psychology & Marketing, 18(7), 763-783 (2001).
[22]. Wang Yang, Yang Yan, Xiao Wanting & Su Qin.:Validity and reliability of the Chinese version of the Cognitive Flexibility Questionnaire for evaluating college students. Chinese Journal of Mental Health (01), 58-63(2016).
[23]. Huang Xiuyun.: The Chinese version of the Critical Thinking Trait Scale was tested in Taiwanese clinical nurses. Degree thesis of the Department of Nursing, National Cheng Kung University (2008).
[24]. Xia, T.: Research on the Influencing Factors of College Students' Video Game Krypton Gold Behavior Based on Technology Acceptance Model. Shanghai Normal University Master's Thesis (2021).
[25]. Button, M., Nicholls, C. M., Kerr, J., & Owen, R.: Online frauds: Learning from victims why they fall for these scams. Australian & New Zealand journal of criminology, 47(3), 391-408(2014).
[26]. Deliema, M., Shadel, D., Pak, K.: Profiling victims of investment fraud: Mindsets and risky behaviors. Journal of Consumer Research, 46(5), 904-914 (2020).
[27]. Deevy, M., Lucich, S., & Beals, M. Scams, schemes & swindles: a research review of consumer financial fraud. Financial Fraud Research Center. http://longevity3.stanford.edu/wp-content/uploads/2014/01/Scams-Schemes Swindles-FINAL-On-Website.pdf, (2012).









