

Volume 13
Published on October 2023Volume title: Proceedings of the 5th International Conference on Computing and Data Science
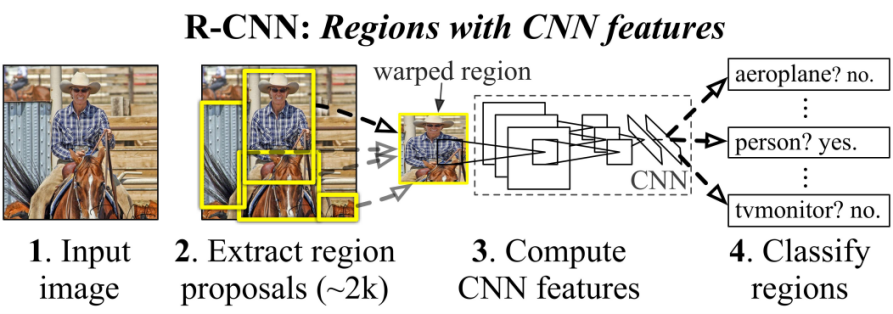
In recent years, with the quantum leap in deep learning, self-driving vehicle as one of its applications has been gaining tremendously increasing popularity as well as making a multitude of achievements. Object detection, which has made significant contribution to driver-less vehicle, has had been applied to a tremendously wide range of fields. However, reports relevant to automatic vehicle stating that accidents are caused by Automatic driving technology, present problems pointing out that existing target detection algorithms, which are already fairly well reliable, can probably be interfered by adverse conditions such as high temperature, raise dust and transmission loss, and be not capable of providing precise output. This paper recaps on these previous classic algorithms, and their large-scale application domain. Meanwhile, this paper presents improvements focusing on enhancing the robustness of these algorithms to overcome these problems caused by adverse conditions and improve the accuracy. Thus these improvements could augment the security of these driver-less vehicles, and eventually reduce traffic accident mortality relative to self-driving vehicles and safeguard road safety, and may potentially benefit to further research.

 View pdf
View pdf


Motion Capture technology refers to the technology of recording and processing the actions of people or other objects, and generating corresponding virtual asset action animations. It has been widely used in our daily life. Virtual characters like Hulk, Gollm, and Avatar were all built based on the technology. It can also be applied to sports analysis, human biomechanics, automotive, virtual reality, etc, showing its huge application prospects. Specifically, 3D Motion Capture Market was forecast to reach $270.9 million by 2026 suggested by industry ARC. To help readers get familiar with the field without much background knowledge, this paper reviews the origin of the motion capture technology, the way motion capture technology was realized and the mainstream methodologies of capturing motion. This paper provides the reader with some existing applications of motion capture technology in different fields so that the reader can understand the importance of the technique. Readers can also get some insight into what future studies may be focused on and if there is any promotion of the motion-capturing methods.

 View pdf
View pdf


Three-dimensional objects are usually represented by point cloud based on lidar reflection of the sensors. However, the point clouds are commonly sparse since the lidar reflection is restricted by the location where the machine scans the objects around it. Commonly, the point cloud data that we use in autonomous driving are basically concentrated on one side or two sides and can seldom depict the whole image of all the objects. In this paper, we propose methods based on symmetry to diminish this intrinsic problem. Our work uses CenterPoint as our backbone and we do some fine-tune on it to make the data augmented. Moreover, we use FutureDet as the detector and the predictor to see whether the results of the methods fit the design. We obtain the information of CenterPoint from the detector and use the position information of the center point to do symmetry so as to make the points exist on the other side. We are trying to address the issue by comparing the results of metrics from the FutureDet and the fine-tune model on nuScenes dataset.

 View pdf
View pdf


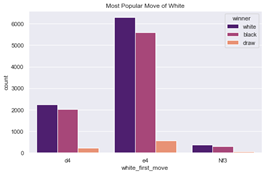
With many gaming AI being developed and being able to defeat top human players in recent years, AI has once again become the hottest topic in research and even in our daily life. This paper also researches on gaming AI and chess. Instead of using deep learning and the Monte Carlo Search algorithm, this paper focuses on the opening only with multi-armed bandit algorithms to find the best moves and opening. Specifically, the method used in this paper is epsilon greedy and Thompson sampling. The dataset used in this paper is from Kaggle. This paper considers each move as a set of choices one needs to make and considers the big picture as a multi-armed bandit problem. This paper aims to develop a relative best strategy to counter those opening or make changes to a disadvantaged situation.

 View pdf
View pdf


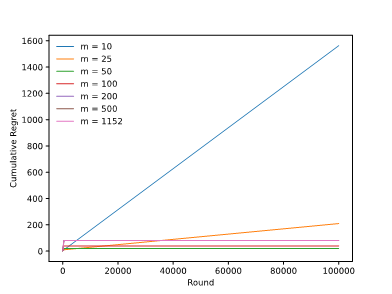
Explore-then-commit (ETC) algorithm is a widely used algorithm in bandit problems, which are used to identify the optimal choice among a series of choices that yield random outcomes. The ETC algorithm is adapted from A/B testing, a popular procedure in decision-making process. This paper explores the multi-armed bandit problem and some related algorithms to tackle the multi-armed bandit problem. In particular, this paper focuses on the explore-then-commit (ETC) algorithm, a simple algorithm that has an exploration phase, and then commits the best action. To evaluate the performance of ETC, a variety of settings is made in the experiment, such as the number of arms and input parameter m, i.e., how many times each arm is pulled in the exploration phase. The result shows that the average cumulative regret increases when the number of arms gets larger. With the increase of parameter m, the cumulative regret decreases in the beginning, until reaching the minimum value, and then starts increasing. The purpose of this paper is to empirically evaluate the performance of the ETC algorithm and investigate the relationships between the parameter settings and the overall performance of the algorithm.

 View pdf
View pdf


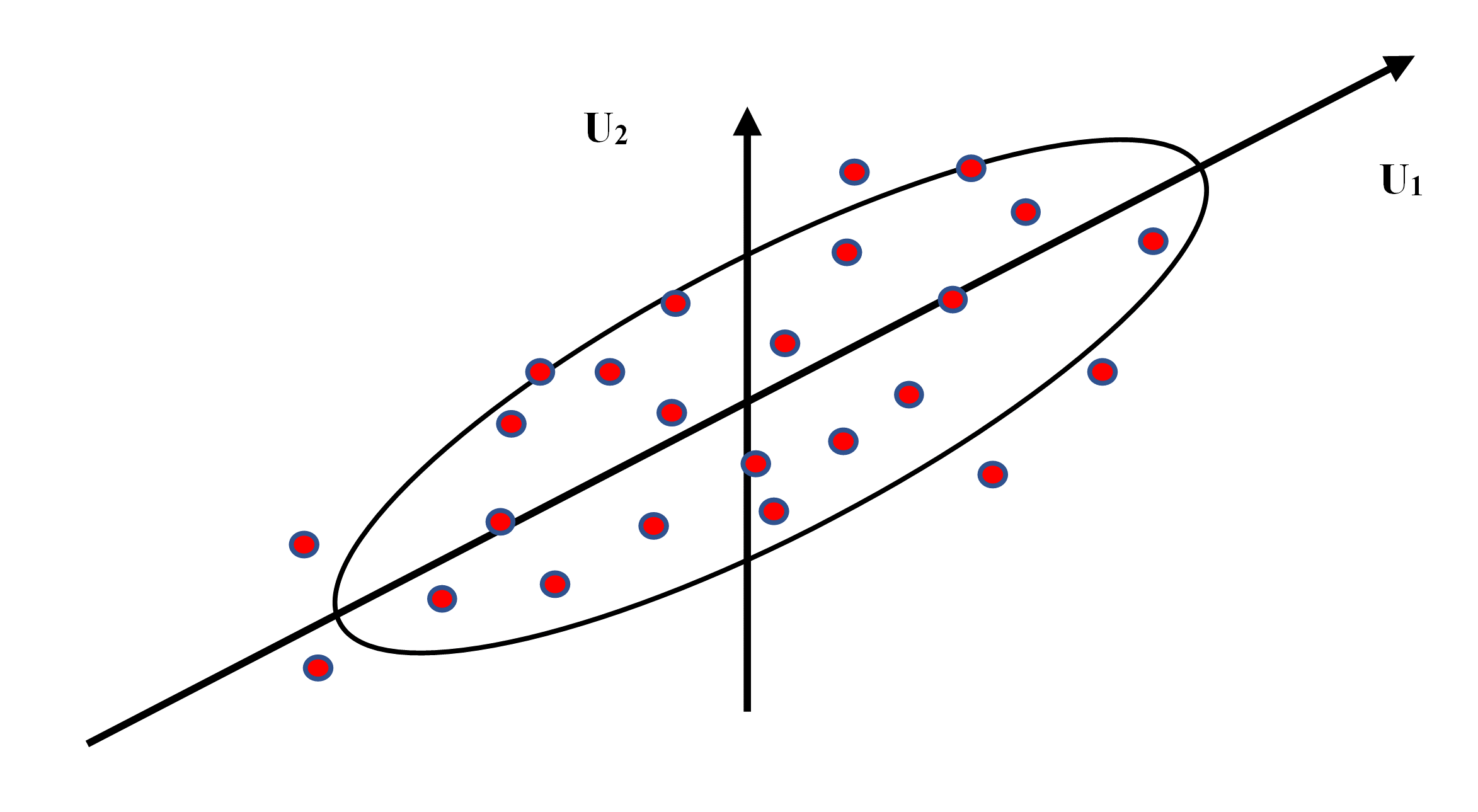
In the past decades, tons of data have been generated every single day as people increasingly rely on electronic products and networks in their lives. The developments in techniques and storage capabilities provide a fundamental condition for analyzing those huge-volumed data. Each captured feature represents a dimension of the data. So far, high dimensional data analysis has become a challenging task in various study fields. Redundant and irrelevant features can be removed by using different dimensionality reduction techniques. Effective information extraction can be achieved by using the proper method. This paper reviews the most widely used dimensionality reduction techniques and their application fields. It can be found that though DRTs have been successfully applied to many areas (i.e., image, audio/video data, biomedical), DRTs still need to be improved and developed to achieve better classification and prediction accuracy. Inter-method combinations will remain the focus of research in the future. Computation time and cost may not be a limitation anymore as the computation power of the computer is still developing. So, the development of the algorithm is becoming particularly important. This study provides a brief introduction to widely used DRTs and their variants, it will be helpful for understanding HDD analysis, and more DRTs will be researched in future work.

 View pdf
View pdf



Crop disease detection is an important factor in agricultural production. Traditional object detection methods can't effectively screen key features, resulting in weak crop disease control in many countries. In recent years, several convolutional neural networks for object detection have been proposed, which makes it possible to apply computer vision to crop disease identification through deep learning. YOLOv5 is an advanced object detection network, which can extract key features and use human visual attention mechanism as a reference. This paper would evaluate the performance of four pre-trained models of YOLOv5 in object detection of crop diseases. And transfer learning was used to train the corresponding dataset. The experiment results have showed that the F1 values of the four models all reached above 0.93, and the Yolov5x got the best result, which achieved 0.963. Furthermore, the detection accuracy of the four models has reached more than 98%. This shows that the YOLOv5 series network models have great application prospects in the identification of crop diseases. In the near future, the object detection model can be applied to various mobile devices, even unmanned aerial vehicles, which would play a significant role in crop disease prevention.

 View pdf
View pdf


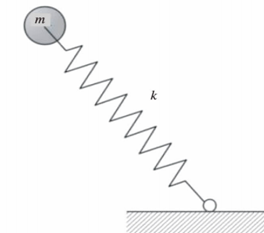
The spring inverted pendulum model was used to analyze the motion of the biped robots under different motion states and the effective model parameters were obtained. In this paper, the biped robot was simplified to an inverted pendulum model and the kinematics equations of the robot under different motion states were obtained. The kinematics equations were solved by MATLAB, and the analysis was used to get the right sports condition during motion process. The corresponding simulation of the inverted pendulum model was carried out based on MATLAB, a series of data such as the trajectory of mass point of the robot and the variation of the ground reaction force during motion process were obtained. By analyzing the results, the model parameters and conditions of the biped robots to keep stable in different motion states were obtained.

 View pdf
View pdf


With the rapid growth of the internet today, cloud storage services have had an impact on numerous internet users worldwide. Internet users, in order to avoid potential risk of data loss, can outsource their local data to remote cloud servers instead of using local media. However, this kind of cloud storage services is sometimes unreliable enough and the data security of users cannot be guaranteed. In this case, data auditing mechanisms for cloud storage are studied to avoid the destruction of user data. The traditional audit schemes are based on provable data possession mechanisms, while the third-party organization relies on the recent blockchain-based methods, conventional single-cloud storage system and recently emerging multi-cloud storage models. Some audit schemes not only provide auditing capability, but also have some other ancillary functions to ensure applicability for different potential malevolent situations. Gathered correlated studies about data auditing schemes of cloud service are analyzed and classified in this paper, based on research objects and research methods in order to seek probable innovation points. We also analyze experiments in their papers. Toward the finish of this review, we sum up all the examination, list the bearings not investigated, and give a few creative spots.

 View pdf
View pdf


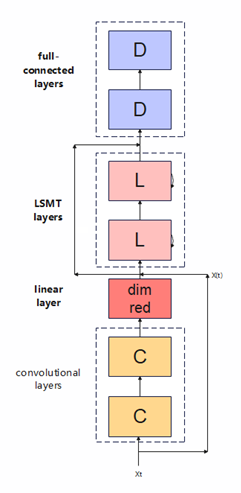
A language is a valuable tool for human development and progress, and it is also an important medium for human beings to transmit information and express emotions. Language signals are ubiquitous, and it is an indispensable part of human life. This article will take the analysis of language as the starting point, combined with the relevant content of computer deep learning, and summarize various methods of language emotion recognition based on a convolutional neural network. In recent years, with the gradual intelligentization of computers, more in-depth discoveries and research have been made on language emotion research. In the deep neural network sector, most of the models used are CNN, LSTM, MO-LSTM models, and this paper aims to propose a new CLDNN (CONVOLUTIONAL, LONG SHORT-TERM) that integrates CNN, DNN, and LSTM into the same network. MEMORY, FULL CONNECTED DEEP NEURAL NETWORKS) model, compare with it, and summarize the advantages and disadvantages of CLDNN.

 View pdf
View pdf




