

Volume 16
Published on October 2023Volume title: Proceedings of the 5th International Conference on Computing and Data Science
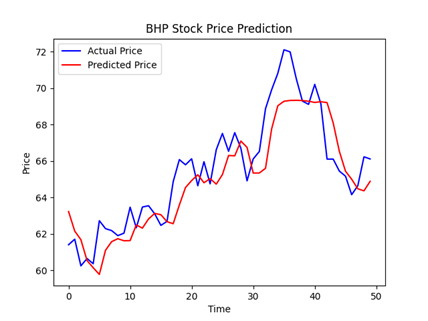
The volatility of Australian companies' stock prices in 2020, caused by China's trade restrictions, poses a significant challenge for predicting financial gain or loss. This research contributes to future scholarship in predicting stock prices under specific circumstances or during special time periods. The study proposes a novel approach to stock price prediction, incorporating news sentiment analysis into a deep learning model. The research collected news items potentially affecting the stock price, incorporating them into an analysis model to generate a new feature for the Long Short-Term Memory (LSTM) model. The LSTM model used in this study was bidirectional, with two sets of gates per layer, and a three-layer model with different units. Each layer employed a dropout layer and a dense layer in the final stage. The study also utilized the feature engineering of lookback, selecting a window of time in the past to predict the next day's stock prices. Following multiple hyperparameter tunings and feature engineering adjustments, the results and graphs demonstrate a successful prediction for all three of the chosen companies, even during an unstable stock market. The overall trend lines achieve optimal predictions for the stock prices, illustrating both upward and downward trends.

 View pdf
View pdf


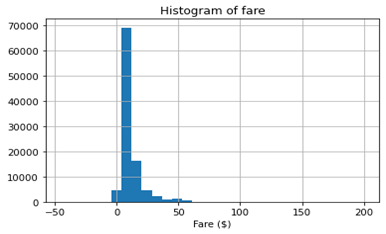
The use of taxis as a fundamental mode of transportation in everyday life has led to the increased popularity of various ride-hailing applications such as Uber and Lyft, enabling users to conveniently request and view the predicted fare for their desired destination. Accurately predicting the fare is thus of significant importance. In this study, machine learning models were employed to forecast taxi fares based on factors such as distance and passenger count. As the initial data only contained latitude and longitude values, the Haversine formula was utilized to calculate the distance between two locations. Moreover, the raw data was plagued with inconsistencies such as negative fares and grossly exaggerated distances, which were resolved by implementing four data cleaning criteria. Following the preprocessing stage, three distinct models (i.e., linear regression, decision tree, and random forest) were trained and evaluated using the root mean square error metric. The results indicated that the random forest model produced the smallest error (1.264), followed by the decision tree model with a similar error rate (1.277), and lastly, the linear regression model with the highest error (1.718). Thus, the random forest model demonstrated superior performance and is recommended for accurate fare predictions.

 View pdf
View pdf


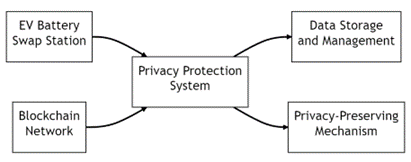
As electric vehicles become more popular, battery swap stations are gaining attention as a new type of charging facility. However, the charging process for electric vehicles involves privacy information such as user location and charging mode, which can be easily stolen or leaked, posing security risks and personal privacy concerns for users. Therefore, protecting the privacy of electric vehicle battery swap station users has become an important issue. This paper aims to study a privacy protection system for electric vehicle battery swap stations using blockchain technology. First, the basic principles and application scenarios of blockchain technology are introduced. Second, potential privacy leaks in electric vehicle battery swap stations are analysed, and a privacy protection scheme based on blockchain is proposed, including anonymous identity authentication, zero-knowledge proof, and encrypted communication. Third, a blockchain-based privacy protection system for electric vehicle battery swap stations is designed and implemented, and its performance is experimentally evaluated and compared with traditional privacy protection schemes in terms of security and efficiency. This paper demonstrates that the blockchain-based privacy protection scheme for electric vehicle battery swap stations possesses high levels of security and reliability, effectively safeguarding users' privacy information. Furthermore, this scheme exhibits promising application prospects and potential for widespread adoption. With the continuous development and utilization of blockchain technology, the privacy protection scheme for electric vehicle battery swap stations using blockchain is expected to provide users with more secure, reliable, and convenient charging services.

 View pdf
View pdf


In the past years, digital signature development has rapidly with new products combined with blockchain, named distribute networks, and quantum computers, while there plays a vitally important role in file authorization and verification. In combination with various new technologies, digital signatures present a vigorous vitality, and new algorithms are widely used in varieties of scenarios including banking, financial services, and insurance (BFSI), education, E-government, healthcare, and the military. In this case, there is no paper illustrating a summary of those new digital signature applications, which is the aim of this paper working on. This paper indicates the technology details of digital signatures and blockchain. And the paper discusses which digital signature algorithms are used in different fields to give an overview of the relationship between algorithms and scenarios. Furthermore, the paper demonstrates the comparison in the most commonly used digital signature algorithm containing Rivest–Shamir–Adleman (RSA) algorithms, Lamport algorithms, Elliptic Curve Digital Signature Algorithm (ECDSA), and Edwards-curve Digital Signature Algorithm (EdDSA) algorithms on their difference in performance.

 View pdf
View pdf


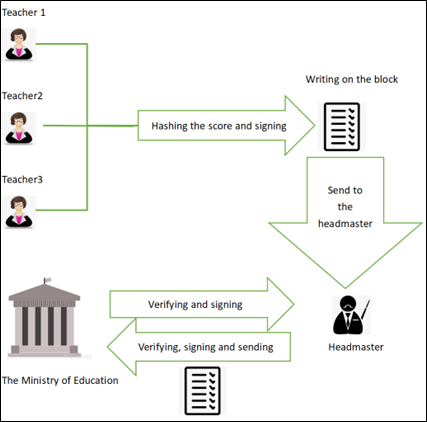
The purpose of designing this system is to provide schools with a new way to make score certifications of a student and a safer way to search for a student’s previous academic scores. When a student is applying for a new school to further his study, the school always uses his previous academic scores to decide whether to enroll him. The current way for a school to mark a student and to search for a new student’s score record is depend on the student himself, which faces the problem of illegal modification and data leakage. The system mentioned in this paper can add a certification that includes the time information and score information. It can also use the digital signatures of teachers and headmasters to ensure that the scores are given by the corresponding teacher. This system does not include the direct Grade Point Average (GPA), but just includes the raw scores of each subject. Because different schools have different ways to turn the raw scores into a GPA and they also have different GPA upper limitations.

 View pdf
View pdf


Recently, deep learning has gained considerable success and acceptance in a variety of fields, attracting an increasing number of researchers who are delving deeper and gaining a broader perspective on the subject. It provides more sustainability and opportunities to advance the development of society and transform the lives of individuals. Consequently, it is crucial for individuals to understand the neural network development path. This paper provides a concise overview of the structure and components of Convolutional Neural Network, as well as some of the most well-known and influential learning models in the history of its development. Through an analysis of various models of convolutional neural network, the workings of convolutional neural networks were investigated. The paper discovered that the structure of neural networks is becoming deeper and more complex in order to achieve greater efficacy and avoid the overfitting issue. For researchers to enhance and advance neural network performance, there are still numerous parameters and perspectives to improve and advance.

 View pdf
View pdf


In today’s society, the 3D modelling field has become an indispensable part of people’s lives. Whether it is the metaverse, games, industry, or medicine, 3D modelling cannot be separated from them. The models used in various fields are also diverse. In the models of various fields, there are not many models for reference in the food field’s biscuit modelling and there are no special views. This article creates a Chinese New Year biscuit with the Chinese handwritten character “Spring” on it based on the different styles and types of biscuit models in the food industry. OpenSCAD software was used to create this model. This article first introduces the methods and usage of OpenSCAD software that are encapsulated for modelling. Then this paper describes in detail how to layer and create biscuits layer by layer. How to use code to create a handwritten Chinese character and a cream biscuit completely in OpenSCAD is detailed by this article. For the result, this article implements a Chinese New Year biscuit with a reference to the “Spring” character written by the ancient Chinese calligrapher Yan Zhenqing. This work fully implements every stroke of handwritten Chinese characters in the cookie model, and these details have been recognized by the majority of people in the final evaluation.

 View pdf
View pdf


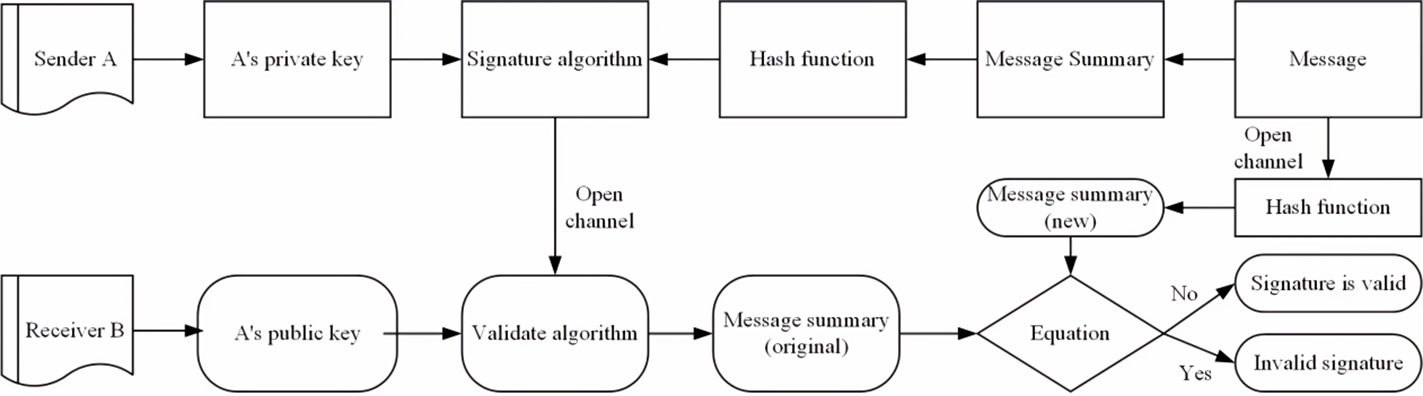
Currently, a lot of studies have been done on the core of Bitcoin, the blockchain. It offers a wide range of distribution mechanisms and infrastructure that keeps the data constant, unchanging, and time consistent. The blockchain is an ideal tool for assertion class applications to offer digital proof of ownership and time stamps as a result of the creation of digital summaries of physical or digital assets. So it is possible to apply the block chain to a wide range of fields, for example, online paying, trading and so on. As the block chain develops, the safety issues directly affect the effectiveness and integrity of the trade. In essence, these questions are about the safety of information. To ensure the security of the data, this paper studies and uses the security of the digital signature. The classification and characteristics of each kind of digital signature are introduced in this article, as well as some other scholars' achievements in this field are analyzed.

 View pdf
View pdf



The YOLOv5 algorithm has gained popularity in recent years as an effective solution for real-time object detection in images and videos. This paper explores its potential for solving the problem of target tracking detection by proposing a modified YOLOv5 architecture that integrates object detection and tracking capabilities.The proposed YOLOv5-based tracking system includes three major components: object detection, object tracking, and object association. The object detection component uses a YOLOv5 model to detect and localize the target object in each frame of the video. The object tracking component then tracks the target object across frames using a Kalman filter and a Hungarian algorithm for data association. Finally, the object association component uses a motion model to handle occlusions and re-identifies the target object when it reappears in the field of view.The performance of the proposed YOLOv5-based tracking system is evaluated on several benchmark datasets, and its results are compared to state-of-the-art tracking algorithms. The experimental results show that the system achieves competitive tracking accuracy and real-time processing speed. Additionally, the effectiveness of the proposed motion model for handling occlusions and re-identification of the target object is demonstrated. In conclusion, the YOLOv5 algorithm has promising potential for target tracking detection in real-world scenarios, and it could have various applications in surveillance, robotics, and autonomous driving.

 View pdf
View pdf


Medical delivery robot refers to the delivery robot used in the medical field. Compared with ordinary delivery robots, the medical delivery robot needs to work in an environment with many people, which means that it needs to deal with many random obstacles at any time. This article will discuss automatically avoiding obstacles, and formulate and compare algorithms to analyze the advantages and disadvantages of automatic road exploration algorithms of different algorithms. In order to accomplish this goal, this paper will use Matlab as the main development tool and use the A-star algorithm and the Euclid algorithm as the main heuristics in the main mathematical model of the program. This program needs to be able to complete the obstacle avoidance task in a map with random size, random position, random shape, and random number of obstacles, and be able to reach the end point from the starting point. In addition, this paper will also discuss the efficiency of the A-star algorithm and the Dijkstra algorithm in obstacle avoidance and route planning, and demonstrate why the A-star algorithm is more efficient by taking time and congestion indicators.

 View pdf
View pdf




